
Trend Micro Internet Security Pro 2008.v16.05.1015 serial key or number
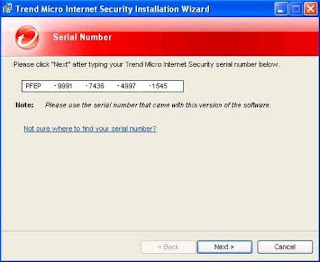
Trend Micro Internet Security Pro 2008.v16.05.1015 serial key or number


What is Photoshop CS3 Extended?
Ideal for film, video, and multimedia professionals and
graphic and web designers using 3D and motion, as well
as professionals in engineering and science,
Adobe® Photoshop® CS3 Extended software delivers
everything in Photoshop CS3 and more. Render and
incorporate 3D images into your 2D composites. Stop
time with easy editing of motion graphics
on video layers. And probe your images with measurement, analysis,
and visualization tools.
Top features
Nondestructive editing
Edit nondestructively with new Smart Filters, which let you visualize different image effects, and Smart Objects, which let you scale, rotate, and warp raster and vector graphics — all without altering the original pixel data.
Rich painting and drawing toolset
Create or modify images with a wide assortment of professional, fully customizable paint settings, artistic brushes, and drawing tools.
Advanced compositing
Create more accurate composites by automatically aligning multiple Adobe® Photoshop® layers or images based on similar content. The Auto-align Layers command quickly analyzes details and moves, rotates, or warps layers to align them perfectly, and the Auto-blend Layers command blends the color and shading to create a smooth, editable result.
3D compositing and texture editing
3D compositing and texture editing
Easily render and incorporate rich 3D content into your 2D composites — even edit existing textures on 3D models directly within Photoshop Extended and immediately see the results. Photoshop Extended supports common 3D interchange formats, including 3DS, OBJ, U3D, KMZ, and COLLADA, so you can import, view, and interact with most 3D models.
Movie Paint
Enhance video directly within Photoshop Extended. Now you can paint, add text, and clone over multiple frames of an imported video sequence.
2D and 3D measurement tools
2D and 3D measurement tools
Extract quantitative information from images with new measurement tools. Easily calibrate or set the scale of an image, and then use any of the Photoshop Extended selection tools to define and calculate distance, perimeter, area, and other measurements. Record data points in a measurement log and export data, including histogram data, to a spreadsheet for further analysis.
Faster, more flexible asset management with Adobe Bridge CS3
Organize and manage images more efficiently with next-generation Adobe Bridge CS3 software, which now delivers improved performance, a Filter panel for easier searching, the ability to group multiple images under a single thumbnail, the Loupe tool, offline image browsing, and more.
Better raw-image processing
Process raw images with increased speed and superior conversion quality using the Photoshop Camera Raw plug-in, which now adds support for JPEG and TIFF formats; new tools including Fill Light and Dust Busting; compatibility with Adobe Photoshop Lightroom™ software; and support for over 150 camera models.
Enhanced Vanishing Point with 3D support
Edit in perspective on multiple surfaces — even those connected at angles other than 90 degrees — with the enhanced Vanishing Point, which also lets you measure in perspective; wrap graphics, images, and text around multiple planes; and output 2D planes as 3D models.
Wide range of supported formats
Import and export an even greater range of file formats, including PSD, BMP, DICOM, Cineon, JPEG, JPEG2000, OpenEXR, PNG, Targa, and TIFF.
Setup Only**NOTE** direct link so speeds get up to 2000kps! (2 mega bytes per second)!
| Code: |
| https://www.adobe.com/cfusion/tdrc/index.cfm?product=photoshop&promoid=BONQJ |

KeyGen+activation **note you must download this in order for it to work*** 100% tested and working by me
| Code: |
| http://rapidshare.com/files/82856820/Photoshop_cs3_extended_keygen.rar |
or try this patch if the keygen/ activation doesnt work for you:
| Code: |
| http://rapidshare.com/files/83085184/PhotoShop_CS3_extended_patch_2.rar |
instructions(for patch):
Install Adobe Photoshop into default location
Run this Patch and overwrite the file tada your done!
avast 4.8 Professional Edition Avast_Antivirus_Pro << Download
Name:www.Piaodown.com Serial : mg37xaj5423
Serial- PS-0HQQ7X-9PKW1R-ZY4ND3-A5XUP2-9CUK9N
Kaspersky internet security 2009 || 4new keys
Kaspersky internet security2009 || 30 keys upto 2011
S/N: 5847-2238-4498-9501-1BD6-500A-5402-A303
Serial- 61E5-7980
Serial- 1045-1090-6246-8353-3166-2968 (This is serial number)
Name: TEAM ROR Serial: 1486567
Babarosa Gif Animator 3.5 also for 3.6
Name-TEAM ANADOXIN Serial key- 64195312F60A8D
WinRAR_v3.71 << download
WinRAR3.80 << download
A-squared Free 4.0.0.46(one of the best)
a-squared Anti-Malware is an all-purpose security product developed by the Emsi Software company. This product provides effective protection not only against most spyware and adware threats, but also against other dangerous security and privacy risks such as trojans, backdoors, keyloggers, rootkits, worms
and dialers.
The program thoroughly checks the Windows registry, running processes, web browser cookies and the entire file system. It also scans in compressed files (Zip, RAR and Cab archives) and NTFS Alternate Data Streams (often used by rootkits). It should be noted that most a-squared Anti-Malware rivals never search for parasites so deeply. Furthermore, the application implements heuristic analysis to detect unknown, emerging threats. All these features allow a-squared Anti-Malware to identify and remove the most sophisticated threats that even some antiviruses cannot find.
The fully functional trial version is available. It expires after 30 days.
CLICK HERE TO DOWNLOAD THE ANTI VIRUS
AUTORUN EATER 2.3 Anti Virus
Autorun Eater was born due to increase of malwares using the ‘autorun.inf’ tactic to infect users unknowingly be it from flash drives, removable hard disks or any other removable storage device. When an infected device is infected with a malware and an ‘autorun.inf’ file is dropped, the shell menu is normally modified to execute the malware whenever the unsuspecting user double-clicks the infected drive.
Most anti-malware apps out there will almost instantly remove any malware detected but more often than not they leave the ‘autorun.inf’ file behind. And what if the anti-malware app fails to catch the malware? Here is when Autorun Eater comes in handy. Autorun Eater will remove any suspicious ‘autorun.inf’ files even before the user attempts to access the drive. This files are auto-backup’ed in case of false positives.
CLICK HERE TO DOWNLOAD THE ANTI VIRUS
AVG Anti Virus Free Edition - trusted by 80 million users
CLICK HERE TO DOWNLOAD THE AVG ANTI VIRUS
CLICK HERE TO DOWNLOAD THE ANTI VIRUS 8.5.278
AVIRA Anti Virus Personal Free Edition
CLICK HERE TO DOWNLOAD THE AVIRA ANTI VIRUS
CLICK HERE TO DOWNLOAD THE ANTI VIRUS 8.2.0.337
AVAST Home Edition 4.8.1335.90205
CLICK HERE TO DOWNLOAD THE AVAST ANTI VIRUS
CLICK HERE TO DOWNLOAD THE ANTI VIRUS 4.8.1335.90205
ESET NOD32 Anti Virus 4.0.314
CLICK HERE TO DOWNLOAD THE ESET NOD32 ANTI VIRUS
KASPERSKY Anti-Virus 7.0.0.125(30 days)
Kaspersky® Internet Security 2009: Next generation multi-award-winning technology for complete protection from viruses, hacker attacks and spam. Offering hourly updates, consistently high detection rates and free telephone technical support, the product includes enhanced protection, performance and reliability, a two-way firewall, parental control features
CLICK HERE TO DOWNLOAD THE KASPERSKY ANTI VIRUS
MACAFREE Anti Virus Free Edition(30days) you need to register first
McAfee has an Antivirus Emergency Response Team that continually monitors the worldwide virus activities to provide you with the utmost safety. The always-on protection guards against viruses, spyware and other Internet threats that may enter your PC via e-mail, instant message attachments, Internet downloads, and web browsing.
One of the newest features is also one of our favorites. It's the QuickScan feature, which basically narrows virus scans to the most vulnerable and frequently attacked parts of your computer. This makes scanning much faster, although we still recommend doing a full scan periodically. Another great feature that can save you some time is SiteAdvisor. This system automatically gives you a visual signal in your browser telling you if the link you are about to click on will send you to a malware site. This can significantly decrease your infection rate, if used properly.
CLICK HERE TO DOWNLOAD THE MACAFREE ANTI VIRUS
MULTI VIRUS CLEANER 2008 8.7.0
CLICK HERE TO DOWNLOAD THE ANTI VIRUS
NORTON Anti Virus 2009 16.0(15-days)
CLICK HERE TO DOWNLOAD THE NORTON ANTI VIRUS
PANDA ACTIVESCAN 2.0(NEWLY ENTERED YOU CAN TRY IT)
CLICK HERE TO DOWNLOAD THE PANDA ANTI VIRUS
PC Tools Anti Virus Free Edition 5
CLICK HERE TO DOWNLOAD THE ANTI VIRUS
THREATFIRE Anti Virus Free Edition 4.0
CLICK HERE TO DOWNLOAD THE THREAT FIRE ANTI VIRUS
TREND MICRO Anti Virus plus Anti Spyware 16(30days)
CLICK HERE TO DOWNLOAD THE TREND MICRO ANTI VIRUS
WEBROOT Anti Virus with Anti Spyware & Firewall 6.0(30 days)
CLICK HERE TO DOWNLOAD THE WEBROOT ANTI VIRUS
USB Disk Security 5.1.0.15 special designed for USB
CLICK HERE TO DOWNLOAD THE USB DISK ANTI VIRUS
NERO BURNER
This is also the cracked free version of the great software . So burn ur CDz and do a lot of jobs hastlefree!
CLICK HERE FOR NERO LINK1
CLICK HERE FOR NERO LINK2
Nero 9 - Lite Edition - Only 51MB!
CLICK HERE TO DOWNLOAD THE NERO 9
NERO 9.0.9.4 FULL VERSIONwith activation serial
Rip & Burn
Best in the World!
Fast and easy ripping, burning and copying of CDs, DVDs and Blu-ray Discs* directly through Nero StartSmart.
With DVD-R Dual Layer and DVD+R Double Layer support, you’ll get more data on a disc than ever before!
DiscCopy Gadget One-click disc copy with Nero DiscCopy Gadget - optimized for Windows Vista® . Personalized Disc Labels Personalize your discs with labels, covers, and booklets, and choose from multiple templates or customize with your own images.
*Please note: Blu-ray capabilities are subject to change.
Video
Whether you’re recording soccer games, concerts, or family reunions, get professional results in an easy-to-use video creation and editing tool. Use the Movie Wizard template library and create entertaining movies for every occasion (birthdays, weddings, vacations). Watch seamless movies or music videos, without commercials or other scenes interrupting, by using Ad Spotter to automatically cut them out. Become the movie director you were meant to be!
Music
Dust off your old CDs and LPs and digitally archive them forever. Easily manage and play your favorite music titles with new music recognition service delivers accurate song and artist information, and album art (Powered by Gracenote®). Browse media for playback, create playlists of your favorite audio tracks, shuffle and categorize tracks for easy reference. Simply create MP3 archives of your favorite Music videos with Music Grabber.
Photo
Make all your digital photos come to life. Share the stories of your life’s most memorable moments with professional photo-editing tools to correct red-eyes, crop, rotate, adjust, and enhance photo quality. Create entertaining photo slideshows with special effects, transitions, and music; burn it on DVD with great 3D menus and share with family and friends.
High-Definition
Make use of the latest AVCHD or HDV camcorders, edit your project in HD quality including Nero SmartEncoding for AVCHD and create an AVCHD disc on a regular DVD medium (red laser) or a BD-AV disc (blue laser).
Convert & enjoy multimedia files on iPod®, PSP®
Convert your music, videos, and photos to DVD, CD, or your portable devices and enjoy them on the go. Convert your old CDs, LPs, and tapes to MP3s and save them forever – Gracenote® MusicID® will give you the track information, titles, and great album art to complete your collection.
Internet
Upload your coolest photos and videos to share with online communities like YouTube™, MySpace, and My Nero. Media Center NEW amazing TV experience from the comfort of your sofa gives you state-of-the-art TV technology, even for HDTV and DVB Radio. Integrates into Windows Vista® Media Center and Windows® XP Media Center Edition.
High-Definition Television Record, manage, playback, and enjoy your favorite TV shows – even for HDTV. Watch High-Definition TV and use the P-i-P (“picture-in-picture”) mode for watching 2 channels at the same time. Playback Media Management DVD and multimedia player features latest digital audio and video file formats, a new playback design – with convenient playlist handling, shuffle playback, as well as docking and stand-by modes of both, the browser window and playlists. New display, with Gracenote® music services, shows clear and accurate track and artist information, as well as album art. DOWNLOAD
Code:
CLICK HERE TO DOWNLOAD NERO-9.0.9.4 LINK1
CLICK HERE TO DOWNLOAD NERO-9.0.9.4 LINK2
CLICK HERE TO DOWNLOAD NERO-9.0.9.4 LINK3
CLICK HERE TO DOWNLOAD NERO-9.0.9.4 LINK4
CLICK HERE TO DOWNLOAD NERO-9.0.9.4 LINK5
CLICK HERE TO DOWNLOAD NERO-9.0.9.4 LINK6
CLICK HERE TO DOWNLOAD NERO-9.0.9.4 LINK7
CLICK HERE TO DOWNLOAD NERO-9.0.9.4 LINK8
Enjoy!
ALL OFFICE CONVERT PLATINUM- Convert any to any
All Office Converter Platinum is an easy-to-use and professional document conversion tool. It can support batch converting documents, web and images with high good quality for business and individual to improve the work efficiency. With this powerful converter, you can create PDF file from versatile formats and convert PDF file to other versatile formats with super output quality and effectively. More, you can convert between different office document formats, web, images. It can support comprehensive formats: Word(doc, docm, docx), Excel (xls .xlsx. xlsm),PowerPoint (ppt, pptc, pptm), PDF,XLS,RTF,TXT,HTM/HTML,Website,JPG,BMP,GIF,TIF,WMF,EMF,TGA, RLE,PNG etc.
Advance Features:
-Provide the customized Command Line service for server/developer.
-It can simultaneously convert different formats to one certain format once.
-It can convert the webpage on the website or your computer.
-Easy to use. Convert with one click.
-More setting options to let you control the output file more accurately.
-Save the imported file list.
-Support encrypted PDF.
-Create PDF and Image with high good quality.
-Open *.HTM or URL as the following framework to convert.
Hi-speed Download:
CLICK HERE TO DOWNLOAD CONVERTER
no PASS needed
HAPPY DOWNLOADING............ USE Ctrl KEY ALONG WITH THE LINK
SOME OLDER ANTIVIRUS WITH HACEKED VERSIONS
KAKA FOLDER Protector 5.36
KaKa Folder Protector is a file-security program allowing the user to hide, lock, encrypt and protect files and folders in the blink of an eye. When folders are password protected and locked, their contents cannot be read, copied, modified or deleted. To access the locked folders, you must supply the correct password.
KaKa Folder Protector has advanced features such as “Security-Level”, allowing the user to select the Strength. Other features of Folder Protector include: Security Level, Show Protected Signs, Password Hint, Change icon of the protected folder, File Filter system.
[Download]
CLICK HERE TO DOWNLOAD KAKA FOLDER PROTECTOR
PROXYCAP Service Edition v3.15
ProxyCap enables you to tunnel Internet applications through HTTP, SOCKS v4, and SOCKS v5 Proxy Servers. You can tell ProxyCap which applications will connect to the Internet through a proxy and under what circumstances. This is done through a user friendly interface, without the need to reconfigure any of your Internet clients. ProxyCap provides flexible rule system and allows you to define your own "tunneling" rules. You can add a new rule with just a few mouse clicks.
[Download]
CLICK HERE TO DOWNLOAD PROXYCAP
F-SECURE Client Security 8.01.133
F-Secure® Client Security™ 8 provides an intelligent way to protect corporate workstations and laptops against traditional and new zero-hour threats. It combines network queries (in-the-cloud), host based intrusion prevention (HIPS) and traditional signature based client security protection. The integrated antivirus, firewall, antispyware, rootkit scanning and behavior monitoring can be centrally managed – easily but effectively.
What's new in F-Secure Client Security version 8:
* F-Secure DeepGuard 2.0: Thanks to this new in-the-cloud technology, all F-Secure users are protected in 60 seconds from the first confirmation of a new threat.
* New updatable scanning architecture allows a quick and smooth response to threats.
* Memory consumption reduced by over a third compared to the previous version.
* Neighborcast feature offers scalable and fast peer-to-peer database update distribution inside a LAN.
* Full IPv6 protection and Windows Vista 64-bit support.
[Download]
CLICK HERE TO DOWNLOAD F-SECURE
DATA GUARDIAN v1.6.1
Data Guardian is a very useful tool because security and privacy are two of the most important issues in today's world; leaving passwords on sticky notes around your computer simply will not cut it anymore.
Data Guardian is a secure database application with up to 448-bits of Blowfish encryption regardless of how sensitive your data is.
Create multiple databases in Data Guardian for a variety of purposes such as an address book, customer database, christmas shopping list, journal, password manager, or even notepad. Easily create categories to store records, and even apply custom color labels and icons!
Change the view options for each category to see the information you want, and even add your own custom data fields. Do not be stuck with a program which forces you to input your information into predefined fields. Enter the data you need to, not what you are forced to.
Aside from Data Guardian's easy to use Keychain integration* to autofill passwords on web sites, it also offers a variety of other tools and features to enhance each record.
Dial phone numbers through your modem with a single click, create new e-mail messages, generate secure passwords (based on an algorithm of your choosing), and even synchronize two databases.
Data Guardian is the ultimate database solution, and not only if security is a priority. Allow Data Guardian to become your computerized Swiss Army Knife in an age of digital chaos.
Here are some key features of "Data Guardian":
· Create unlimited records, collections, and fields!
· Insert pictures into records
· Dial phone numbers directly from records
· Import virtually any flat-text file and map it to custom fields
· Export your database to a flat-text file for use in other programs
· Synchronize databases
· Automatically login to servers
· Synchronize Data Guardian with Safari's Keychain to aid in auto-fill
· QuickBrowser - access to Data Guardian from within any application
· Up to 448-bit Blowfish encryption
· Record application activity to a log
· Auto-clear clipboard after a specified interval
· Dynamically generate passwords based on a user specified algorithm
· Automatically saves databases
· Can discard changes and quit Data Guardian if left idle for a period of time
· Print a sheets of record information in a variety of formats
· Apply changes to a selection of records at the same time
· Powerful RegEx search function
· Cross platform compatible database format between the Mac and Windows versions
· Auto-quit if idle for a specified time period
[Download]
CLICK HERE TO DOWNLOAD DATA GAURD
FOLDER LOCK 6.1.5
Folder Lock™ is a fast data encryption and password protection software for Windows. It can simultaneously encrypt, lock and password protect your files, folders, drives, USB drives and even CD/DVD-RW.
Folder Lock creates encrypted storages called 'Lockers'. You can keep as many of your private files & folders in your Locker and password protect it with a single click. You can transfer, secure and backup these Lockers. Lockers are portable, you can keep them in USB Flash Drives, CD/DVD (R-RW), & notebooks or transfer them via email or upload. Lockers are even undeletable on the computer where Folder Lock is installed.
You can create as many Lockers as you want. Different users on a single PC can create different Lockers as well. With Folder Lock, you can choose either to encrypt using 256-bit AES on-the-fly encryption or lock files, folders and drives anywhere on your computer. Each Locker can contain your encrypted files as well as your personal list of locked items.
Furthermore, Folder Lock's options like hack monitoring, stealth mode, data shredding, history cleaning, auto protection, portable USB autoplay feature & virtual keyboard can enhance data security beyond anything ever achieved. In addition, a locker's delete, move and rename are password protected to prevent data loss.
Folder Lock is compatible on both 32-bit and 64-bit versions of Windows Vista / 2003 / XP / 2000 & is the most downloaded File Security program in the market.
[Download]
http://rapidshare.com/files/198349350/Folder_Lock_6.1.5.rar"target="_blank">CLICK HERE TO DOWNLOAD FOLDER LOCK
Dr.Web 5.00.1.09020 for Windows
* Anti-virus – best active infection curing
* Anti-rootkit – reliable protection against malicious programs featuring rootkit technologies
* Anti-spyware – security of your personal information – best of breed detection of Trojans and key loggers
Cures viruses
High detection rate and speed of scanning are not the only criteria that determine the quality of an anti-virus. It should also be capable of curing files – restoring them to their original state instead of deletion making sure that a user doesn’t lose important information.
The capability to operate in an infected system and exceptional resistance to viruses make Dr.Web a stand-out among anti-virus applications.
* Improved! Dr.Web has the industry-highest successful rate of curing active infections.
* Improved! Unique technologies for scan of processes in the memory and excellent curing capabilities allow installing Dr.Web onto the infected system without its preliminary curing.
* High probability of a successful launch of the scanning process in an infected system without an installation using a removable media.
Protection Components:
* High-performance Dr.Web scanner scans boot sectors, RAM, hard and removable drives, detects and disarms viruses, Trojans and malware of any other type.
* Enhanced by Dr.Web Shield™ it also detects all known rootkits and stealth-viruses.
[Download]
CLICK HERE TO DOWNLOAD Dr WEB
ANTI-TROJAN Elite 4.3.3
Anti-Trojan Elite™ (ATE) is a malware remover. Malware is software designed specifically to damage or disrupt a system, such as a trojan horse, a spyware or a keylogger.
ATE contains a Real-Time File Firewall, it monitor system and clean malwares immediately. It is also a system security tools, you can view and control processes and TCP/IP network connections.
The reasons to choose Anti Trojan Elite:
* Real-time malware firewall, protecting user's computer in real-time.
* Detecting and cleaning binded malware, doesn't hurt normal file and clean the malware.
* Detecting and cleaning no process malware, some malware don't have a EXE file, they are only some DLL files and running as some threads in other process, ATE can detect and clean this type of malware even it's running.
* Free tools. View the information of Tcp/Ip states and processes informations.
Features:
* Disk and memory scan supported.
* Real-time malware firewall.
* Compressed files (RAR ZIP CAB) scan supported.
* Backup module: Backup trojan files before killing.
* Network Manager. View the tcp/udp states and the processes they belonged to. User can disconnect any tcp connection and stop the opposite process.
* Process manager. View the processes and its DLL modules' information. User can terminate any process and unload any DLL module.
* Internet Explorer and registry repair utility.
* Updating online supported, and auto check updates when ATE starts.
* Real-time registry monitor utility.
[Download]
CLICK HERE TO DOWNLOAD ANTI-TROJAN
KEY PROWLER Pro 3.3.6.0
KeyProwler is an easy to setup and easy to use PC monitoring application for Windows that allows you to remotely monitor any PC, secretly or not. KeyProwler runs completely hidden and does not show up in the start menu, add/remove programs, or in the task manager.....
Those who are seriously concerned with remotely monitoring a PC cannot imagine doing so without using this amazing tool with a very simple and elegant interface. Simply install this program and Keyprowler will send you log files right to your inbox! No complex email setup, just simply enter your email address and Keyprowler does the rest!! Start/Stop buttons make logging as easy as using a VCR!!! KeyProwler can be used as a family monitor.
[Download]
CLICK HERE TO DOWNLOAD KEY PROWLER
MCAfee Host Intrusion Prevention Client 7.0.0 Patch 3 MultiOS
Proactively secure desktops against zero-day attacks
Exploits and vulnerabilities are more complex, and they’re released more quickly than ever before. Anti-virus alone can’t do the job. Defend your desktops and laptops from known and new zero-day attacks with McAfee Host Intrusion Prevention. Part of McAfee Total Protection for Endpoint, it boosts security, lowers costs by reducing the frequency and urgency of patching, and simplifies compliance.
System Requirements
* Windows XP Home with Service Pack 2
* Windows XP Professional with Service Pack 2
* Windows XP Tablet PC
* Windows Vista, 32-bit and 64-bit
[Download]
CLICK HERE TO DOWNLOAD MACA FEE
BEST NETWORK Security 2.4
Best Network Security is the best solution for corporations, public libraries, internet cafes, schools, universities and other applications where administrator has to secure and maintain a lot of network PC workstations located in different places. Administrator does not need physically visit workstations to change security settings or install patches.
Best Network Security is intended for securing, protecting, and maintaining PC workstations within a corporate network. This network-based password-protected security software lets you completely secure PC workstations over your network as well as maintain them by uploading and installing any executable patches remotely. It supports tons of security restrictions, options and tweaks to control access to every bit of Windows. You can deny access to each individual component of several Control Panel applets, including Display, Network, Passwords, Printers, System and Internet Options; disable the boot keys, context menus, DOS windows, Registry editing, Internet and Network access; hide desktop icons, individual drives, Start menu items, and taskbar; apply password protection to Windows and restrict users to running specific applications only, Control Internet Usage and much more.
[Download]
CLICK HERE TO DOWNLOAD BEST NETWORK
INTELINET Internet Security Suite 3.1.0
Award Winning Spyware Remover
#1 Rated Anti-Spyware & Anti-Adware Keep Your PC Safe from Spyware & Adware! Spyware grows more sophisticated every day. There's more of it, and it's more malicious than ever before. Experts agree: Intelinet Spyware & Adware Remover delivers the most advanced spyware& Adware detection, blocking and removal available to beat dangerous Spyware & Virus programs.
Award Winning Registry Cleaner
Intelinet 3.1.0 Registry Cleaner is the smart choice in quick and easy PC error diagnostics and repairs. Intelinet Registry Cleaner cleans and repairs unwanted debris left behind by adware and spyware. This top-rated registry tool is extremely powerful, yet easy to use, and will keep your computer operating like new. We guarantee our software will eliminate 100% of your PC errors and restore your computer back to it's original performance! You will be amazed, it's like you just bought a brand new computer!
[Download]
CLICK HERE TO DOWNLOAD INTELINET
SPYWARE NUKER XT 4.9.09.1815
Did you know that SPYWARE is the number one threat to personal computing? Also, 9 out of 10 PCs that are hooked up to the INTERNET are infected with SPYWARE or ADWARE, and in most cases both! Not only can SPYWARE and ADWARE ruin your expensive computer forever, but they can possibly lead to you being fired from your job or even divorced. People can also be sent to prison for what SPYWARE has added to their computer!
[Download]
CLICK HERE TO DOWNLOAD NUKER
FOLDER LOCK 6.0.5 Latest! Serial 100% worked!
Folder Lock™ is a fast data encryption and password protection software for Windows. It can simultaneously encrypt,lock and password protect your files, folders, drives, USB drives and even CD/DVD-RW.
You must block folder.exe to access internet using firewall e.g zonealarm or comodo. it’ll prevent the program to check the serial to it server. Follow the instruction then u’ll have folder lock 100% working for life!
[Download]
CLICK HERE TO DOWNLOAD FOLDER LOCK
USB Disk Security v5.1.0.15 Latest Release
USB disk security is an ultimate tool against the security threats which are related to USB drives. This is the best ever tool against USB drive threats. This should be the part of PC security.
1. USB Disk Security provides 100% protection against any threats via USB drive, however, the majority of other products are unable even to guarantee 90% protection.
2. USB Disk Security is the best antivirus software to permanently protect offline computer without the need for signature updates, but other antivirus software should update signature database regularly, and they cannot effectively protect offline computer.
3. This light and easy to use solution is 100% compatible with all software and doesn’t slow down your computer at all.
[Download]
CLICK HERE TO DOWNLOAD USB SECURITY LATEST
SYMANTEC AntiVirus Corporate Edition 10.2.2
Symantec AntiVirus Corporate Edition combines industry-leading, real-time malware protection for enterprise workstations and network servers with graphical Web-based reporting and centralized management and administration capabilities. The solution automatically detects and repairs the effects of spyware, adware, viruses, and other malicious intrusions to enable enterprise-wide system uptime. Symantec System Center? enables centralized configuration, deployment, policy management, alerting and reporting, and allows administrators to audit the network to determine which nodes are vulnerable to virus attacks. Administrators can manage client and server groups logically, and can create, deploy, and lock down security policies and settings to keep systems up-to-date and properly configured.
[Download]
CLICK HERE TO DOWNLOAD SYMANTIC
[Mirror]
CLICK HERE TO DOWNLOAD MIRROR
ARCLAB Watermark Studio 1.0
Watermark Studio is an easy to use image processing software to add visible and transparent watermarks to multiple images in a batch. It allows you to protect your photos from unauthorized distribution using one of the included or a custom watermark, which could be added on any position and size.
Watermark Studio also can be used to create thumbnails, resize and convert images. There is only one click required to process a whole directory of images.
* Protect your photos using a visible watermark
* Visual marketing
* Supports jpeg,png,gif,tiff, bmp and psd images
* Convert images to popular image formats (jpeg,png,gif,tif,bmp)
* Resize images and create thumbnails
* Transparent watermarks with custom opactiy
* Batch processing
[Download]
CLICK HERE TO DOWNLOAD ARCLAB
[Mirror]
CLICK HERE TO DOWNLOAD MIRROR
ZONE ALARAM ForceField 1.1.82.0
Bank, shop, and browse the Web safely and privately.
ZoneAlarm ForceField provides a protective layer around your browser, shielding you from drive-by downloads, browser exploits, phishing attempts, spyware and keyloggers. So your passwords, your confidential information, and your financial data remain protected.
Nothing else protects you like ZoneAlarm ForceField. What is virtual browsing?
• Block unauthorized downloads and malicious software installations
• Protect your identity by blocking phishers and stopping keyloggers
• Browse the internet in complete privacy–erases all cache, cookies, history and passwords
• Run it with your existing security software–it’s fast, lightweight, and easy to use
[Download]
CLICK HERE TO DOWNLOAD FORCE FEILD
Dr.Web LiveCD 4.44.0.0811010 (ISO)
Dr.Web LiveCD is an image of a bootable compact disk which contains all necessary tools to check your computer for viruses without installation of any programs on the hard drive. The check is made by the anti-virus on-demand scanner with the newest anti-virus bases included into the CD. Dr.Web LiveCD allows to scan files in all file systems of Windows (FAT, FAT32 and NTFS).
[Download]
CLICK HERE TO DOWNLOAD Dr.WEB
PASSWORDPRO 2.4.4.1 - Recover Passwords
PasswordsPro is a professional program to recover the passwords for user hashes. The range of hashes supported include: MySQL, MySQL5, DES(Unix), MD4, MD4(HMAC), MD5, MD5 (HMAC), MD5(Unix), MD5(APR), SHA-1, SHA-1(HMAC), SHA-256, SHA-384, SHA-512, Domain Cached Credentials, Haval-128, Haval-160, Haval-192, Haval-224, Haval-256, Tiger-128, Tiger-160, Tiger-192 and Whirlpool. The program also supports many complex hashes like md5($pass.$salt), md5($salt.$pass), md5(md5($pass)), md5(md5($pass).$salt), md5($salt.md5($pass)), md5($salt.$pass.$salt), and sha1($username.$pass). In addition, the program distributive includes modules written by third party developers for the following hashes: MD2, Oracle DES, and MD5(Cisco PIX). Because the program has a convenient open API, it is possible to quickly modify and supply the program with any required hashing module written in any programming language. The program benefits from a friendly interface, does not require installation, supports several types of attack, and is provided with a range of settings. This ensures flexible and effective recovery of user passwords from hashes.
[Download]
CLICK HERE TO DOWNLOAD PASSWORD
ZoneAlarm Professional 8.0.059.000 - Final
ZoneAlarm Security Suite is the easy-to-use, comprehensive security solution that is based on the world’s best firewall to keep out hackers, viruses, worms, and other threats. It combines the most popular firewall with antivirus, Web site filtering, privacy protection, instant messaging security and more to provide the best overall protection of any PC security suite.
[Download]
CLICK HERE TO DOWNLOAD ZONE ALARAM FINAL
SPYWARE NUKERr XT v4.9.08.1815 WinALL Cracked
Spyware Nuker XT will scan your computer FREE for any malicious spyware, adware or malware. If found, it will notify you of all infections and inform you of steps to remove it!
Operating System Requirements:
This product is designed to run on the following operating systems:
* Windows XP
* Windows 2000
* Windows 98
Additional Requirements:
* Software requirements: Internet Explorer 5.0 or later.
* Hardware requirements: Pentium 233MHz processor or better
* 16MB RAM
* 10MB HDD Space
* Mouse
* Internet Connection (dial-up modem, cable modem or DSL) for program updates.
[Download]
CLICK HERE TO DOWNLOAD SPY NUKER
SPYWARE Doctor with Anti-Virus 6.0.0.385
Spyware Doctor™ provides three-way spyware protection for your PC through real-time threat blocking, advanced system scanning and immunization against known browser infections. Spyware Doctor is a multi-award winning spyware removal utility that detects, removes and protects your PC from thousands of potential spyware, adware, Trojans, keyloggers, spybots and tracking threats. Protect your privacy and computing habits from prying eyes and virtual trespassers with the help of Spyware Doctor.
Anti-virus software and firewalls do not fully protect your system against the majority of spyware and privacy threats. Because spyware is commonly bundled with software downloads, attached to e-mails, or transmitted through networks it can appear to be legitimate software, but once installed it can be nearly impossible to detect and remove without the help of a dedicated spyware removal tool like Spyware Doctor.Spyware Doctor has consistently been awarded Editors’ Choice, by leading PC magazines and testing laboratories around the world, including United States, United Kingdom, Sweden, Germany and Australia. All current versions of Spyware Doctor have won Editors’ Choice awards from PC Magazine in United States. In addition, after leading the market in 2005, Spyware Doctor was awarded the prestigious Best of the Year at the end of 2005.
[Download]
CLICK HERE TO DOWNLOAD SPY DOCTOR
TROJAN REMOVER v6.7.2 - Fast & Effective
Trojan Remover aids in the removal of Malware - Trojan Horses, Worms, Adware, Spyware - when standard anti-virus software either fails to detect them or fails to effectively eliminate them. Standard antivirus programs are good at detecting this Malware, but not always so good at effectively removing it.
Trojan Remover is designed specifically to disable/remove Malware without the user having to manually edit system files or the Registry. The program also removes the additional system modifications some Malware carries out which are ignored by standard antivirus and trojan scanners.
[Download]
CLICK HERE TO DOWNLOAD TROJAN REMOVER
BIT DEFENDER Antivirus 2009
BitDefender Antivirus 2009 provides advanced proactive protection against viruses, spyware, phishing attacks and identity theft, without slowing down your PC.
[Download]
CLICK HERE TO DOWNLOAD BIT DEFENDER
Spyware Doctor 6.0.0.383 & ANTIVIRUS WORKING!
FOR THOSE PEOPLE WHO CANNOT REGISTER THIS LATEST VERSION !
That’s because you’ve installed a previous version using different serial or crack that register it. Spyware Doctor stores this serial in Windows Registry and when you want to register the new version with different serial you can’t because it won’t let you enter the new serial because it uses the old one !!!
To solve this problem do this:
Completely close Spyware Doctor and run this program to reset the registration data.
[Download]
CLICK HERE TO DOWNLOAD SPY DOCTOR
[Mirror]
CLICK HERE TO DOWNLOAD SPY DOCTOR MIRROR
OUTPOST FIREWALL Pro 2009 Build 6.5.2359.316.0607
Outpost Firewall Pro provides a superior arsenal of defense against PC infiltration. Outpost ensures your online security with solid protection against all Internet-borne threats. Outpost is the first personal firewall developed with Open Architecture. It is also the first personal firewall that supports plug-ins. Sample plug-ins are included to show how this revolutionary technology can easily be employed for such tasks as Intrusion Detection, Advertisement Blocking, Content Filtering, E-mail Guard, and Privacy Control. It is equipped with every feature a personal firewall should have. It is the most functional firewall in the world. It supports all the latest security techniques and features such as: Full Stealth Mode, Anti-Leak, and MD5 Authentication.
Being online is fraught with dangers: Internet worms, spyware agents, Trojan horses, hijackers and more can wreak havoc, causing anything from slow performance to system crashes to full-blown identity theft. And to provide you with the kind of protection you need in these days of cyberthieves and online extortionists, your firewall must be able to monitor all inbound and outbound traffic and protect you from any unauthorized intrusion by rendering your PC invisible to anything that you haven’t authorized to see it.
What you get:
* Advanced firewall for secure connections
* Antispyware to keep your PC spyware-free
* Host protection to block zero-day threats
* Web control to protect your PC from web-borne threats
Benefits:
• Safety on the Internet. The two-way firewall stops inappropriate or malicious access to your computer from both internal (LAN) and external (Internet) sources. As a frontline defense, it prevents malware from spreading or “phoning home”, providing protection against hackers, loss of personal data, unknown malware, and unauthorized program activity.
• Preemptive threat protection. Outpost’s Host Protection module monitors how programs interact to protect your system against high-level security breaches and has passed all well-known leaktests to prevent unauthorized transmission of information from your PC.
• No more spyware! Eliminate spyware with Outpost’s dedicated antispyware utility. Regular updates and always-on monitoring ensure that spyware cannot activate and cause damage to your data or divert your applications.
• Secure web surfing. The versatile Web Control module safeguards you against the Internet’s darker side. It steers you away from websites infected with drive-by downloads, prevents the inadvertent disclosure of personal information, limits your exposure to potentially unsafe web properties, and keeps your identity private.
• Bulletproof self-defense. Outpost cannot be deactivated by targeted attacks, ensuring continuity of protection.
• Power without complexity. Whether you’re a security novice or expert, you can easily configure Outpost Firewall Pro to meet your needs. Thanks to automated and context-sensitive help, the firewall can learn how to handle alerts and make decisions for you, so you can focus on what you want to do, and leave the security to Outpost!
Supported platforms: 32- and 64-bit Windows (Vista, XP, Server 2003), Windows 2000 (SP3 and above).
Changes in Outpost Firewall Pro 2009 (build 6.5.2358.316.0607), 15 July 2008:
The following issues are resolved (only significant ones are listed):
* Connections were blocked on sending attachments through POP3
* Improved overall system performance
[Download]
CLICK HERE TO DOWNLOAD OUTPOST FIREWALL
VUSESCAN Professional 8.4.83 - Best Scanner Software
VueScan, the world’s most popular scanner software, is used extensively by photographers, home users, scanning services and corporations. VueScan is a scanning program that works with most high-quality flatbed and film scanners to produce scans that have excellent color fidelity and color balance. It is very easy to use, and also has advanced features for restoring faded colors, batch scanning and other features used by professional photographers.
VueScan changes nothing on your system, installs nothing in your operating system and all other scanner software will continue to function. VueScan increases your productivity and saves you money. VueScan has advanced scanning options, powerful features, and greatly improves your scans with superior color accuracy and better color balance. VueScan supports more than 700 scanners and 209 digital camera raw files and takes about 5 minutes to download and install.
[Download]
CLICK HERE TO DOWNLOAD VUESCAN
NORTON ANTIBOT v1.1
Norton AntiBot provides advanced, real-time protection against emerging threats, including bots that are used to perpetrate identity theft and other online crimes. This powerful new security solution from Symantec detects unusual behavior on your PC and removes the malicious bots causing it. This protects your PC from unauthorized access and tampering, detects and stops attempts by hackers to take remote control of your computer, and delivers extra protection against emerging 'zero-day' threats. To help ensure that you're always protected, Norton AntiBot monitors your PC continuously to stop suspicious programs.
[Download]
CLICK HERE TO DOWNLOAD NORTON ANTIBOT
AIO ULTIMATE Hacking Experience 2008
The collection of Several Tools Features below by which u will feel a real hacking Experiences
* Trojan Horses
* Keyloggers
* Binders
* WebHacks/WordLists
* Brute Forcers
* CGI-Bug Scanners
* Viruses
* Virus Builders
* MSN Hacks & Bots
* Port & IP Scanners
* Nukers And Flooders
* EXTRA
[Download]
CLICK HERE TO DOWNLOAD AIO ULTIMATE
PORTABLE LIMEWIRE Pro 4.18.5
LimeWire - The Fastest P2P File Sharing Program on the Planet, running on the Gnutella Network. It is open standard software running on an open protocol, free for the public to use. LimeWire allows you to share any file such as.mp3s, .avis, jpgs, tiffs, etc., allows you to search for multiple files at the same time, available in several different languages, and is most famous for its ease-of-use and cross-platform compatibility. Limewire is written in Java, and will run on Windows, Macintosh, Linux, Solaris, and other computing platforms.
[Download]
CLICK HERE TO DOWNLOAD LIMEWIRE
MALWARE BYTES' Anti-Malware 1.25
Malwarebytes' Anti-Malware is an anti-malware application that can thoroughly remove even the most advanced malware. It includes a number of features, including a built in protection monitor that blocks malicious processes before they even start.
Malwarebytes' Anti-Malware monitors every process and stops malicious processes before they even start. The Realtime Protection Module uses our advanced heuristic scanning technology which monitors your system to keep it safe and secure. In addition, we have implemented a threats center which will allow you to keep up to date with the latest malware threats.
[Download]
CLICK HERE TO DOWNLOAD MALWARE BYTES'
PORTABLE SPYWARE TERMINATOR 2.3.0.481
Spyware Terminator is a FREE, easy-to-use and effective spyware remover providing real-time protection against spyware, adware, keyloggers, trojan horses, browser hijackers and other malware threats. Spyware Terminator protects your computer through powerful real-time protection shield, advanced system scanning and keeping found spyware in the safe quarantine.
[Download]
CLICK HERE TO DOWNLOAD SPYWARE TERMINATOR
INVISIBLE SECRETS 4.6.2
Keep those prying eyes out of your communications and prevent unwanted people from reading your private files!
Invisible Secrets 4 not only encrypts your data and files for safe keeping or for secure transfer across the net, it also hides them in places that on the surface appear totally innocent, such as picture or sound files, or web pages. These types of files are a perfect disguise for sensitive information. Using our file encryption software nobody, not even your wife, boss, or a hacker would realize that your important papers or letters are stored in your last holiday pictures, or that you use your personal web page to exchange messages or secret documents. With Invisible Secrets 4 - file encryption software you may encrypt and hide files directly from Windows Explorer, and then automatically transfer them by e-mail or via the Internet.
[Download]
CLICK HERE TO DOWNLOAD INVISIBLE SECRETS
RESET Any Windows PASSWORD (including Vista)
Forgot your Windows Admin/User password? Want to find out your computer’s BIOS/CMOS password? This is the right tool for you! Works on USB drives too so no need to burn unto a CD.
[Download]
CLICK HERE TO DOWNLOAD RESET
USB Disk Security v 5.1.0.0
USB Disk Security provides 100% protection against any threats via USB drive, however, the majority of other products are unable even to guarantee 90% protection. USB Disk Security is the best antivirus software to permanently protect offline computer without the need for signature updates, but other antivirus software should update signature database regularly, and they cannot effectively protect offline computer. This light and easy to use solution is 100% compatible with all software and doesn't slow down your computer at all. You pay USB Disk Security once and get it all, however, other antivirus products should be paid for updates every year.
[Download]
CLICK HERE TO DOWNLOAD USB SECURITY
Zone Alarm Security Suite 7.1 Vista Compatible
Complete and unmatched security
Industry leading antivirus and anti-spywareBanish viruses and spyware from your PC for good. ZoneAlarm Internet Security Suite not only eradicates threats but also prevents them from ever entering in the first place. It also stops identity thieves, phishers, and spammers cold, so it's no wonder we've been rated the best in the business.
ncludes operating system firewall, network and program firewall, antivirus, anti-spyware, identity theft protection, game mode, IM protection, parental control and much more.
KEY BENEFITS OF ZONEALARM INTERNET SECURITY SUITE
This comprehensive, all-in-one suite is a tightly integrated set of advanced security layers that, together, create the most secure protection in the industry. Uniquely engineered to prevent threats from getting on a PC in the first place, it has won more major awards than any other security software on the market. The suite combines the robust security features computer experts demand with automatic functions that make it simple enough for novices to use.
Network and Program Firewall:
Delivers proactive firewall protection with multiple layers of security that stop inbound, outbound, and program attacks while remaining completely invisible to hackers.
Operating System Firewall (OSFirewall):
This additional layer of security prevents hard-to-remove malicious programs from getting onto your PC and causing damage.
Antivirus:
Continually searches for, finds, and removes viruses and other malicious software in a single powerful operation.
Identity Theft Protection:
While ZoneAlarm continues to secure your identity information on your PC, these new Identity Theft Protection services also prevent identity theft over the Internet and even in the physical world.
Anti-Spyware:
Always runs full-strength to catch and eliminate spyware before it gets onto your PC.
Spy Site Blocking:
Prevents spyware from getting on your PC by blocking its primary source: spyware distribution websites.
Privacy Protection:
Manages and blocks pop-up ads, online profiling, cookies, cache, and scripts so you can surf in peace.
Anti-Spam & Anti-Phishing
IM Protection:
Protects your instant messages - even those sent between different services - so they can't be monitored.
Game Mode:
One-click control temporarily suppresses most security alerts and prevents them from interrupting your fun while maintaining maximum protection for your PC.
Essential Email Security:
Quarantines suspicious attachments to help defend against unknown viruses; automatically halts outbound messages to keep you from accidentally infecting others.
Wireless PC Protection:
Automatically detects wireless networks and secures your PC from hackers and other Internet threats wherever you're connected - at home or on the road.
[Download]
CLICK HERE TO DOWNLOAD ZONE ALARAM SECURITY
STEGANOS Anonymous Surfing
Each visit to the Internet discloses your identity to Web providers ? often, without you noticing or wanting this. And also your Internet provider can exactly see which Web sites you visit and what kind of data you upload or download. When you use a WLAN (Wireless Local Area Network) or a hot spot to access the Internet wirelessly, for example at a train station, an airport, or in an Internet caf?, it won?t be a problem for anyone to spy on you.
It just takes the corresponding software to turn you into a transparent user. All your movements on the Web can then be exactly traced ? whether you send private e-mails, carry out online purchases, or enter your personal access data. Even when you dial in to online applications, you are unprotected: Someone could ?stow away? and use your access data unnoticed in order to manipulate and even delete important data!
Operating systems:
* Windows 2000
* Windows XP Home Edition
* Windows XP Professional
* Windows Vista (32bit)
* Mac OS X
System requirements:
* Internet access
* Screen resolution of at least 1024x768 pixels
* High color (16 Bit)
* At least 32 MB of free memory
* At least Pentium or comparable CPU
* A mouse or another Windows-compatible pointing device
[Download]
CLICK HERE TO DOWNLOAD STEGANOS
PROGRAM PROTECTOR v3.1
Program Protector is the world's number one tool for password protecting programs. You can easily password protect any Windows application. program Protector is very easy to use and does not require any special computer knowledge. You can password protect programs with a few clicks.
Why does Program Protector work when competitors fail?
Program Protector is unique - because it works with any Windows program, and unlike other protection software, it is safe against circumvention. Malicious users can not disable protection by renaming the protected program file or simply uninstalling Program Protector.
Key features and benefits:
Password protect any Windows application
Drag and drop program files and shortcuts to protect them
Browse the list of protected programs
Password protect the Program Protector itself
Customize password prompt
View protected program activity log
100% protection, can't be bypassed
Compatible with all programs, including Internet Explorer and Outlook Express
Very easy to use
[Download]
CLICK HERE TO DOWNLOAD PROGRAM PROTECTOR
SPYBOT- Search & Destroy 1.5.2 Final
Spybot - Search & Destroy can detect and remove spyware of different kinds from your computer. Spyware is a relatively new kind of threat that common anti-virus applications do not yet cover. If you see new toolbars in your Internet Explorer that you didn't intentionally install, if your browser crashes, or if you browser start page has changed without your knowing, you most probably have spyware. But even if you don't see anything, you may be infected, because more and more spyware is emerging that is silently tracking your surfing behaviour to create a marketing profile of you that will be sold to advertisement companies.
[Download]
CLICK HERE TO DOWNLOAD SPYBOT FINAL
[Mirror]
CLICK HERE TO DOWNLOAD SPYBOT FINAL MIRROR
PORTABLE SPYBOT - Search & Destroy 1.6.0.30 - Final + Multilanguage
Spybot - Search & Destroy can detect and remove spyware of different kinds from your computer. Spyware is a relatively new kind of threat that common anti-virus applications do not yet cover. If you see new toolbars in your Internet Explorer that you didn't intentionally install, if your browser crashes, or if you browser start page has changed without your knowing, you most probably have spyware. But even if you don't see anything, you may be infected, because more and more spyware is emerging that is silently tracking your surfing behaviour to create a marketing profile of you that will be sold to advertisement companies.
Spybot-S&D can also clean usage tracks, an interesting function if you share your computer with other users and don't want them to see what you worked on. And for professional users, it allows to fix some registry inconsistencies and extended reports.
Spybot-S&D can start in two modes: Easy mode for new users who want just the basic features, and Advanced mode for professional users and those who want more control. Both modes are available in the free version.
Spybot - Search & Destroy now officially "Works with Vista"
[Download]
CLICK HERE TO DOWNLOAD SPYBOT
AD-AWARE 2008 Pro v7.1.0.10
Ad-Aware 2008 is the latest version of Lavasoft’s industry leading anti-spyware solutions. Ad-Aware 2008 allows you to combat the growing threats and latest advancements of malicious spyware and malware.
Ad-Aware 2008 protects you from spyware that secretly takes control of your computer, resulting in aggressive advertising pop-ups, sluggish computer activity and even identity theft through stolen private information. We give you the tools to detect hazardous content on your computer, clearly identify their threat level, and then give you the control to remove unwanted content, so that your private information remains right where it should - under your control.
[Download]
CLICK HERE TO DOWNLOAD AD-AWARE
[Mirror]
CLICK HERE TO DOWNLOAD AD-AWARE MIRROR
SUPERANTISPYWARE Professional v4.1.1046 WinAll Incl. Keygen and Patch
SUPERAntiSpyware is the most thorough AntiSpyware scanner on the market. Our Multi-Dimensional Scanning and Process Interrogation Technology will detect spyware that other products miss! SUPERAntiSpyware will remove ALL the Spyware, NOT just the easy ones!
[Download]
CLICK HERE TO DOWNLOAD SUPERANTISPYWARE
SPY EMEERGENCY 2008 5.0.205
Spy Emergency is the anti spyware, anti malware, anti spam solution that fast and secure removes spyware, malware, spam and other internet threats from your computer. Spy Emergency protects you against thousands of various infections and potencially unwanted software, including spyware, adware, spam, virus, trojans, worms, homepage hijackers, remote administration tools, activex components, dialers, scumware, keyloggers, data mining software, toolbars, tracking cookies, browser, hijackers/BHO's.
[Download]
CLICK HERE TO DOWNLOAD SPY EMERGENCY
NORMAN MALWARE Cleaner: Built 2008/04/23
Norman Malware Cleaner is a Norman program utility that may be used to detect and remove specific malicious software (malware).
Note that it should not be used as a substitute for running normal proactive antivirus protection, but rather as a reactive tool to handle systems that are already infected.
[Download]
CLICK HERE TO DOWNLOAD NORMAN MALWARE
PORATABLE MALWAREBYTES Anti-Malware 1.11
Perform a quick scan or a full system scan on your computer to detect and quarantine/remove the malware found on your PC.
Malwarebytes is a site dedicated to fighting malware. Malwarebytes has developed a variety of tools that can identify and remove malicious software from your computer. When your computer becomes infected, Malwarebytes can provide the needed assistance to remove the infection and restore the machine back to optimum performance.
Have you ever considered what makes an anti-malware application effective? We at Malwarebytes have created an easy-to-use, simple, and effective anti-malware application.
[Download]
CLICK HERE TO DOWNLOAD MALWARE BYTES
PORTABLE Panterasoft Flash File Recovery 2.4
A data recovery tool for various flash cards (SmartMedia , CompactFlash, Memory Stick etc)Flash File Recovery - do you need a sure solution for recovering lost, corrupted or accidentally deleted photographs? Flash File Recovery is a 100% risk-free application that salvages images from digital cameras or flash memory cards.
Features:
lost your weekend digital photos?
recover your images with our photo recovery software!
format the flash card?
Flash File Recovery will helps you to undelete images!
flash card corrupted?
photo camera or computer shutdown while writing flash card?
bad blocks on the flash card?
compact flash recovery
try Flash File Recovery for free to recover your digital images and video!
photo recovery service at home!
Common Image files - JPEG, TIFF, PNG, others
Proffesional RAW Image files - Canon CRW, Nikon NEF, Konica-Minolta MRW, Kodak DCR, others
Video files - AVI, MOV, MPG/MPEG, others
[Download]
CLICK HERE TO DOWNLOAD PANTERASOFT
SPYWARE NUKER XT v4.9.02.1815
Spyware and Adware are files that can be installed on your computer even though you don't want them!
Most antivirus software does not detect them, because they are not technically considered a virus.
* It scans your memory (for active memory ad components, which are not stored on your hard drive and last only as long as the computer is powered up), Registry, and Drives for known spyware components and lets you remove them safely, even ad component DLLs.
* This tool hunts down spyware and adware programs hogging resources and causing conflicts on your computer.
* It also features SpyWatch, a real-time monitor watching your memory and Registry for spyware that tries to install on or change your system.
[Download]
CLICK HERE TO DOWNLOAD SPYWARE NUKER
PC TOOLS Firewall Plus 3.0.1.14
PC Tools Firewall Plus is a powerful free personal firewall for Windows® that protects your computer by preventing unauthorized users from gaining access to your computer through the Internet or a network. By monitoring applications that connect to the network Firewall Plus can stop Trojans, backdoors, keyloggers and other malware from damaging your computer and stealing your private information.
PC Tools Firewall Plus is advanced technology designed especially for people, not just experts. Powerful prevention against attacks and known exploits is activated by default while experienced users can optionally create their own advanced packet filtering rules, including IPv6 support, to customize the network defenses. All you need to do is install it for immediate and automatic ongoing protection.
That's how PC Tools Firewall Plus provides world-leading protection, backed by regular Smart Updates, real-time protection and comprehensive network shielding to ensure your PC remains safe and hacker free. PC Tools products are trusted and used by millions of people every day to protect their home and business computers against online threats.
We recommend you use PC Tools Firewall Plus in combination with Spyware Doctor for comprehensive system protection against spyware, adware and other threats.
[Download]
CLICK HERE TO DOWNLOAD PC TOOLS
PC-CILLIN Internet Security 2008 16 Build
PC-Cillin Internet Security 2008 16.0 Build
Stay Connected. Be Protected. Everyday, everywhere. Trend Micro Internet Security 2008 makes it easy to protect your home network, personal identity, and online activity. It guards against present viruses, spyware, and identity theft as well as the web threats of tomorrow. Confidently e-mail, shop, bank, or share photos online, knowing your privacy and files are well protected.
Trend Micro™ PC-cillin™ Internet Security is the first personal Internet security solution specifically designed to extend desktop security to your home and wireless networks. Trend Micro PC-cillin Internet Security combines award-winning antivirus security and a personal firewall-for comprehensive protection against viruses, worms, Trojans, and hackers. It also detects and removes spyware and blocks spam. It even guards against identity theft by blocking phishing and pharming attacks. Plus, PC-cillin protects your wireless network with Wi-Fi Intrusion Detection, an innovative security feature that alerts you when an intruder uses your Wi-Fi connection.
Easy to install, configure, and manage, Trend Micro Internet Security 2008 automatically updates and immunizes your PC and removes malicious threats buried deep inside your computer. With features for home network protection, URL filtering, data theft and online fraud protection, unauthorized change prevention, and much more, this superior suite goes far beyond the basics.
Automatic Protection. Once installed, Trend Micro Internet Security 2008 protects you by automatically performing the following tasks:
• Checks for and downloads any new update every three hours
• Helps prevent spyware from monitoring your computer, as well as unauthorized changes to your computer’s settings
• Searches for risks every time you open, copy, move, or save a file
• Stops you from downloading risky files, and blocks attempts to visit sites that pose a security threat
• Helps protect your computer from hackers and network viruses
For greater protection, enable the optional Parental Controls, Spam Email Filter, Data Theft Prevention, and Wireless Home Network Monitor features.
PC-Cillin Internet Security contains:
• Anti-virus
• Anti-spyware
• Email safety scan
• Protection against rootkits
• Proactive intrusion blocking
• Anti-spam
• Two-way firewall
• Home network protection
• Website authentication
• Parental controls
• Data theft prevention
What’s New:
• A sophisticated monitoring system intercepts and blocks unauthor changes to your computer’s operating system and applications.
• A single integrated scan now checks for computer viruses, spywar operating system security flaws.
• Security activity reports let you see at a glance how Trend Micro I Security 2008 has protected you recently.
• New Trend Micro Data Network controls offer more protection.
• A streamlined installation process sets up the software quickly and
• Image spam filtering catches unwanted messages containing only advertising graphics used to bypass text-based scanning systems.
This release is working on the following systems:
* Windows Vista Home or Business (32 or 64 bit)
* Windows Vista Ultimate (32 or 64 bit)
* Windows XP Home or Pro with SP1 or SP2(32 bit)
* Windows XP Media Center 2004/2005 SP1 or SP2 (32 bit)
* Windows XP Tablet PC 2004/2005 SP1 or SP2 (32 bit)
* Windows 2000 Pro with SP4
[Download]
CLICK HERE TO DOWNLOAD PC CILLIN
CHECK POINT ZoneAlarm with Antivirus v7.1.248.000 Incl. Keymaker
Enhanced detection and removal capabilities stop even the latest and most aggressive viruses before they infect your PC. Includes antivirus, operating system firewall, network and program firewall, auto-learn, and much more.
Vista Compatible!
[Download]
CLICK HERE TO DOWNLOAD CHECK POINT
ANTI TROJAN Elite v3.9.3
Anti Trojan Elite provide a real-time malware firewall for user, once a trojan or keylogger would been loaded, the ATE can detect, block and then clean it in time before it starts. The ATE can detect more than 22000 trojans, worms and keyloggers currently, and the number of malware ATE could clean is growing up very quickly, we collect world-wide malwares, user can using our auto live update feature to get the power to clean these new malwares in time.
Anti Trojan Elite has some useful utilities especially. The network utility can been used to disconnect suspicious TCP connections; The process utility can been used to kill suspicious processes even the process has the system priviage, even it has the ability to unload suspicious modules in all processes; The registry repair utility can been used to repair registry altered by malware; The registry monitor utility can been used to repair any change of important registry keys and values with real time.
[Download]
CLICK HERE TO DOWNLOAD ANTI TROJAN
PERCEPTION SECURA Archiver v3.01
Secura Archiver is professional archiving software for use in personal or commercial environments that demand 128 bit encryption to meet and exceed today's security standards.
Features:
* 128 Bit Encryption (Security)
* Key Generator
* The Secura Key Generator allows you to generate 128 bit encryption keys using your own mouse movements.
* Self-Restoring Archives
* Self-restoring archives can be restored on any computer without installing any software. A trimmed down version of Secura Archiver is included as part of the archive and will allow you to quickly and easily restore any or all files from the archive.
* Data Compression
* No 2GB Backup Size Limit.
* Drag and Drop Interface
* Full Unicode Support (Japanese, Chinese, Arabic...)
Vista Compatible!
[Download]
CLICK HERE TO DOWNLOAD PERCEPTION SECURA
EVERSTRIKE Universal Shield v4.2
Universal Shield 4.2 by Everstrike Software is the ultimate protection tool for your computer — hide files, folders, and drives, and set access rules using flexible security combinations for your most precious data. A unique feature of Universal Shield is the perfect combination of data hiding and encrypting. The program has been especially designed to be the most flexible security tool on the market, suitable both for home use and in corporate environments. Password-protect your data, program start-up, or program uninstall. Secure your data not only from local users, but network and Internet users as well.
The new version also contains a wizard, which includes an option of restricting personal folders and settings, as well as files/folders/drives protection, a hiding expert, and a data encryption master.
[Download]
CLICK HERE TO DOWNLOAD EVERSTRIKE Universal
[More info]
CLCIK HERE FOR MORE INFORMATION
EVERSTRIKE USBSpy v2.0
USBSpy lets you capture, display, record and analyze data that's transferred between any USB device connected to PC and applications. This makes it a great tool for debugging software, working on device driver or hardware development and provides a powerful platform for effective coding, testing and optimization. USBSpy is one powerful tool that makes USB traffic readily accessible for analysis and debugging. Its filters and triggers cut the chase and present only required data. Its interface makes the communications easy to follow. Give it a try and see it for yourself.
[Download]
CLICK HERE TO DOWNLOAD EVERSTRIKE
[More info]
CLICK HERE FOR INFORMATION
TROJAN REMOVER 6.6.5 Build 2510
Trojan Remover aids in the removal of Malware - Trojan Horses, Worms, Adware, Spyware - when standard anti-virus software either fails to detect them or fails to effectively eliminate them. Standard antivirus programs are good at detecting this Malware, but not always so good at effectively removing it.
Trojan Remover is designed specifically to disable/remove Malware without the user having to manually edit system files or the Registry. The program also removes the additional system modifications some Malware carries out which are ignored by standard antivirus and trojan scanners.
[Download]
CLICK HERE TO DOWNLOAD TROJAN REMOVER
STEGANOS Safe 2008
Encrypt your private data. Create as many Safes as you wish with a capacity of up to 256 GB of containment each: for photos, documents, movies…Create secure Data Safes in a few clicks on your PC or use your iPod as a portable safe when you are on the go. The Steganos safe helps you to create highly secure passwords – and you have nothing to remember, simply use a USB-Stick for a key. You also have the possibility to open your safe by using a sequence of pictures. Includes the Steganos Shredder and Mail Client Safe for Outlook, Outlook Express and Windows Mail.
[Download]
CLICK HERE TO DOWNLOAD STEGANOS
TREND Micro Internet Security Pro 2008 v16.05.1015
[Download]
CLICK HERE TO DOWNLOAD TREND MICRO
SUPERAntiSpyware Professional v4.0.0.1126
SUPERAntiSpyware is the most thorough AntiSpyware scanner on the market. Our Multi-Dimensional Scanning and Process Interrogation Technology will detect spyware that other products miss! SUPERAntiSpyware will remove ALL the Spyware, NOT just the easy ones!
Features:
*Quick, Complete and Custom Scanning of Hard Drives, Removable Drives, Memory, Registry, Individual Folders and More! Includes Trusting Items and Excluding Folders for complete customization of scanning!
*Detect and Remove Spyware, Adware, Malware, Trojans, Dialers, Worms, KeyLoggers, HiJackers, Parasites, Rootkits and many other types of threats.
*Light on System Resources and won't slow down your computer like many other anti-spyware products. Won't conflict with your existing anti-spyware or anti-virus solution!
*Repair broken Internet Connections, Desktops, Registry Editing and more with our unique Repair System!
*Real-Time Blocking of threats! Prevent potentially harmful software from installing or re-installing!*
*Multi-Dimensional Scanning detects existing threats as well as threats of the future by analyzing threat characteristics in addition to code patterns.
*First Chance Prevention examines over 50 critical points of your system each time your system starts up and shuts down to eliminate threats before they have a chance to infect and infiltrate your system.
*Process Interrogation Technology allows threats to be detected no matter where they are hiding on your system.
*Schedule either Quick, Complete or Custom Scans Daily or Weekly to ensure your computer is free from harmful software.*
*Dedicated Threat Research Team scours the web for new threats and provides daily definition updates.*
* Denotes feature available only in SUPERAntiSpyware Professional Version
[Download]
CLICK HERE TO DOWNLOAD SUPERANTI SPYWARE
What’s New in the Trend Micro Internet Security Pro 2008.v16.05.1015 serial key or number?
Screen Shot

System Requirements for Trend Micro Internet Security Pro 2008.v16.05.1015 serial key or number
- First, download the Trend Micro Internet Security Pro 2008.v16.05.1015 serial key or number
-
You can download its setup from given links:


