
4D Engine 6.0.x serial key or number

4D Engine 6.0.x serial key or number
Node.js v14.12.0 Documentation
Source Code:lib/tls.js
The module provides an implementation of the Transport Layer Security (TLS) and Secure Socket Layer (SSL) protocols that is built on top of OpenSSL. The module can be accessed using:
TLS/SSL concepts#
The TLS/SSL is a public/private key infrastructure (PKI). For most common cases, each client and server must have a private key.
Private keys can be generated in multiple ways. The example below illustrates use of the OpenSSL command-line interface to generate a 2048-bit RSA private key:
With TLS/SSL, all servers (and some clients) must have a certificate. Certificates are public keys that correspond to a private key, and that are digitally signed either by a Certificate Authority or by the owner of the private key (such certificates are referred to as "self-signed"). The first step to obtaining a certificate is to create a Certificate Signing Request (CSR) file.
The OpenSSL command-line interface can be used to generate a CSR for a private key:
Once the CSR file is generated, it can either be sent to a Certificate Authority for signing or used to generate a self-signed certificate.
Creating a self-signed certificate using the OpenSSL command-line interface is illustrated in the example below:
Once the certificate is generated, it can be used to generate a or file:
Where:
- : is the signed certificate
- : is the associated private key
- : is a concatenation of all Certificate Authority (CA) certs into a single file, e.g.
Perfect forward secrecy#
The term forward secrecy or perfect forward secrecy describes a feature of key-agreement (i.e., key-exchange) methods. That is, the server and client keys are used to negotiate new temporary keys that are used specifically and only for the current communication session. Practically, this means that even if the server's private key is compromised, communication can only be decrypted by eavesdroppers if the attacker manages to obtain the key-pair specifically generated for the session.
Perfect forward secrecy is achieved by randomly generating a key pair for key-agreement on every TLS/SSL handshake (in contrast to using the same key for all sessions). Methods implementing this technique are called "ephemeral".
Currently two methods are commonly used to achieve perfect forward secrecy (note the character "E" appended to the traditional abbreviations):
- DHE: An ephemeral version of the Diffie-Hellman key-agreement protocol.
- ECDHE: An ephemeral version of the Elliptic Curve Diffie-Hellman key-agreement protocol.
Ephemeral methods may have some performance drawbacks, because key generation is expensive.
To use perfect forward secrecy using with the module, it is required to generate Diffie-Hellman parameters and specify them with the option to . The following illustrates the use of the OpenSSL command-line interface to generate such parameters:
If using perfect forward secrecy using , Diffie-Hellman parameters are not required and a default ECDHE curve will be used. The property can be used when creating a TLS Server to specify the list of names of supported curves to use, see for more info.
Perfect forward secrecy was optional up to TLSv1.2, but it is not optional for TLSv1.3, because all TLSv1.3 cipher suites use ECDHE.
ALPN and SNI#
ALPN (Application-Layer Protocol Negotiation Extension) and SNI (Server Name Indication) are TLS handshake extensions:
- ALPN: Allows the use of one TLS server for multiple protocols (HTTP, HTTP/2)
- SNI: Allows the use of one TLS server for multiple hostnames with different SSL certificates.
Pre-shared keys#
TLS-PSK support is available as an alternative to normal certificate-based authentication. It uses a pre-shared key instead of certificates to authenticate a TLS connection, providing mutual authentication. TLS-PSK and public key infrastructure are not mutually exclusive. Clients and servers can accommodate both, choosing either of them during the normal cipher negotiation step.
TLS-PSK is only a good choice where means exist to securely share a key with every connecting machine, so it does not replace PKI (Public Key Infrastructure) for the majority of TLS uses. The TLS-PSK implementation in OpenSSL has seen many security flaws in recent years, mostly because it is used only by a minority of applications. Please consider all alternative solutions before switching to PSK ciphers. Upon generating PSK it is of critical importance to use sufficient entropy as discussed in RFC 4086. Deriving a shared secret from a password or other low-entropy sources is not secure.
PSK ciphers are disabled by default, and using TLS-PSK thus requires explicitly specifying a cipher suite with the option. The list of available ciphers can be retrieved via . All TLS 1.3 ciphers are eligible for PSK but currently only those that use SHA256 digest are supported they can be retrieved via .
According to the RFC 4279, PSK identities up to 128 bytes in length and PSKs up to 64 bytes in length must be supported. As of OpenSSL 1.1.0 maximum identity size is 128 bytes, and maximum PSK length is 256 bytes.
The current implementation doesn't support asynchronous PSK callbacks due to the limitations of the underlying OpenSSL API.
Client-initiated renegotiation attack mitigation#
The TLS protocol allows clients to renegotiate certain aspects of the TLS session. Unfortunately, session renegotiation requires a disproportionate amount of server-side resources, making it a potential vector for denial-of-service attacks.
To mitigate the risk, renegotiation is limited to three times every ten minutes. An event is emitted on the instance when this threshold is exceeded. The limits are configurable:
- <number> Specifies the number of renegotiation requests. Default:.
- <number> Specifies the time renegotiation window in seconds. Default: (10 minutes).
The default renegotiation limits should not be modified without a full understanding of the implications and risks.
TLSv1.3 does not support renegotiation.
Session resumption#
Establishing a TLS session can be relatively slow. The process can be sped up by saving and later reusing the session state. There are several mechanisms to do so, discussed here from oldest to newest (and preferred).
Session identifiers#
Servers generate a unique ID for new connections and send it to the client. Clients and servers save the session state. When reconnecting, clients send the ID of their saved session state and if the server also has the state for that ID, it can agree to use it. Otherwise, the server will create a new session. See RFC 2246 for more information, page 23 and 30.
Resumption using session identifiers is supported by most web browsers when making HTTPS requests.
For Node.js, clients wait for the event to get the session data, and provide the data to the option of a subsequent to reuse the session. Servers must implement handlers for the and events to save and restore the session data using the session ID as the lookup key to reuse sessions. To reuse sessions across load balancers or cluster workers, servers must use a shared session cache (such as Redis) in their session handlers.
Session tickets#
The servers encrypt the entire session state and send it to the client as a "ticket". When reconnecting, the state is sent to the server in the initial connection. This mechanism avoids the need for server-side session cache. If the server doesn't use the ticket, for any reason (failure to decrypt it, it's too old, etc.), it will create a new session and send a new ticket. See RFC 5077 for more information.
Resumption using session tickets is becoming commonly supported by many web browsers when making HTTPS requests.
For Node.js, clients use the same APIs for resumption with session identifiers as for resumption with session tickets. For debugging, if returns a value, the session data contains a ticket, otherwise it contains client-side session state.
With TLSv1.3, be aware that multiple tickets may be sent by the server, resulting in multiple events, see for more information.
Single process servers need no specific implementation to use session tickets. To use session tickets across server restarts or load balancers, servers must all have the same ticket keys. There are three 16-byte keys internally, but the tls API exposes them as a single 48-byte buffer for convenience.
Its possible to get the ticket keys by calling on one server instance and then distribute them, but it is more reasonable to securely generate 48 bytes of secure random data and set them with the option of . The keys should be regularly regenerated and server's keys can be reset with .
Session ticket keys are cryptographic keys, and they must be stored securely. With TLS 1.2 and below, if they are compromised all sessions that used tickets encrypted with them can be decrypted. They should not be stored on disk, and they should be regenerated regularly.
If clients advertise support for tickets, the server will send them. The server can disable tickets by supplying in .
Both session identifiers and session tickets timeout, causing the server to create new sessions. The timeout can be configured with the option of .
For all the mechanisms, when resumption fails, servers will create new sessions. Since failing to resume the session does not cause TLS/HTTPS connection failures, it is easy to not notice unnecessarily poor TLS performance. The OpenSSL CLI can be used to verify that servers are resuming sessions. Use the option to , for example:
Read through the debug output. The first connection should say "New", for example:
Subsequent connections should say "Reused", for example:
Modifying the default TLS cipher suite#
Node.js is built with a default suite of enabled and disabled TLS ciphers. This default cipher list can be configured when building Node.js to allow distributions to provide their own default list.
The following command can be used to show the default cipher suite:
This default can be replaced entirely using the command-line switch (directly, or via the environment variable). For instance, the following makes the default TLS cipher suite:
The default can also be replaced on a per client or server basis using the option from , which is also available in , , and when creating new s.
The ciphers list can contain a mixture of TLSv1.3 cipher suite names, the ones that start with , and specifications for TLSv1.2 and below cipher suites. The TLSv1.2 ciphers support a legacy specification format, consult the OpenSSL cipher list format documentation for details, but those specifications do not apply to TLSv1.3 ciphers. The TLSv1.3 suites can only be enabled by including their full name in the cipher list. They cannot, for example, be enabled or disabled by using the legacy TLSv1.2 or specification.
Despite the relative order of TLSv1.3 and TLSv1.2 cipher suites, the TLSv1.3 protocol is significantly more secure than TLSv1.2, and will always be chosen over TLSv1.2 if the handshake indicates it is supported, and if any TLSv1.3 cipher suites are enabled.
The default cipher suite included within Node.js has been carefully selected to reflect current security best practices and risk mitigation. Changing the default cipher suite can have a significant impact on the security of an application. The switch and option should by used only if absolutely necessary.
The default cipher suite prefers GCM ciphers for Chrome's 'modern cryptography' setting and also prefers ECDHE and DHE ciphers for perfect forward secrecy, while offering some backward compatibility.
128 bit AES is preferred over 192 and 256 bit AES in light of specific attacks affecting larger AES key sizes.
Old clients that rely on insecure and deprecated RC4 or DES-based ciphers (like Internet Explorer 6) cannot complete the handshaking process with the default configuration. If these clients must be supported, the TLS recommendations may offer a compatible cipher suite. For more details on the format, see the OpenSSL cipher list format documentation.
There are only 5 TLSv1.3 cipher suites:
The first 3 are enabled by default. The last 2 -based suites are supported by TLSv1.3 because they may be more performant on constrained systems, but they are not enabled by default since they offer less security.
Class: #
The class represents a stream of encrypted data. This class is deprecated and should no longer be used.
#
The property returns the total number of bytes written to the underlying socket including the bytes required for the implementation of the TLS protocol.
Class: #
Returned by .
Event: #
The event is emitted by the object once a secure connection has been established.
As with checking for the server event, should be inspected to confirm whether the certificate used is properly authorized.
Class: #
Accepts encrypted connections using TLS or SSL.
Event: #
This event is emitted when a new TCP stream is established, before the TLS handshake begins. is typically an object of type . Usually users will not want to access this event.
This event can also be explicitly emitted by users to inject connections into the TLS server. In that case, any stream can be passed.
Event: #
The event is emitted when key material is generated or received by a connection to this server (typically before handshake has completed, but not necessarily). This keying material can be stored for debugging, as it allows captured TLS traffic to be decrypted. It may be emitted multiple times for each socket.
A typical use case is to append received lines to a common text file, which is later used by software (such as Wireshark) to decrypt the traffic:
Event: #
The event is emitted upon creation of a new TLS session. This may be used to store sessions in external storage. The data should be provided to the callback.
The listener callback is passed three arguments when called:
- <Buffer> The TLS session identifier
- <Buffer> The TLS session data
- <Function> A callback function taking no arguments that must be invoked in order for data to be sent or received over the secure connection.
Listening for this event will have an effect only on connections established after the addition of the event listener.
Event: #
The event is emitted when the client sends a certificate status request. The listener callback is passed three arguments when called:
The server's current certificate can be parsed to obtain the OCSP URL and certificate ID; after obtaining an OCSP response, is then invoked, where is a instance containing the OCSP response. Both and are DER-representations of the primary and issuer's certificates. These can be used to obtain the OCSP certificate ID and OCSP endpoint URL.
Alternatively, may be called, indicating that there was no OCSP response.
Calling will result in a call.
The typical flow of an OCSP Request is as follows:
- Client connects to the server and sends an (via the status info extension in ClientHello).
- Server receives the request and emits the event, calling the listener if registered.
- Server extracts the OCSP URL from either the or and performs an OCSP request to the CA.
- Server receives from the CA and sends it back to the client via the argument
- Client validates the response and either destroys the socket or performs a handshake.
The can be if the certificate is either self-signed or the issuer is not in the root certificates list. (An issuer may be provided via the option when establishing the TLS connection.)
Listening for this event will have an effect only on connections established after the addition of the event listener.
An npm module like asn1.js may be used to parse the certificates.
Event: #
The event is emitted when the client requests to resume a previous TLS session. The listener callback is passed two arguments when called:
The event listener should perform a lookup in external storage for the saved by the event handler using the given . If found, call to resume the session. If not found, the session cannot be resumed. must be called without so that the handshake can continue and a new session can be created. It is possible to call to terminate the incoming connection and destroy the socket.
Listening for this event will have an effect only on connections established after the addition of the event listener.
The following illustrates resuming a TLS session:
Event: #
The event is emitted after the handshaking process for a new connection has successfully completed. The listener callback is passed a single argument when called:
The property is a indicating whether the client has been verified by one of the supplied Certificate Authorities for the server. If is , then is set to describe how authorization failed. Depending on the settings of the TLS server, unauthorized connections may still be accepted.
The property is a string that contains the selected ALPN protocol. When ALPN has no selected protocol, equals .
The property is a string containing the server name requested via SNI.
Event: #
The event is emitted when an error occurs before a secure connection is established. The listener callback is passed two arguments when called:
#
The method adds a secure context that will be used if the client request's SNI name matches the supplied (or wildcard).
#
Returns the bound address, the address family name, and port of the server as reported by the operating system. See for more information.
#
The method stops the server from accepting new connections.
This function operates asynchronously. The event will be emitted when the server has no more open connections.
#
Returns the current number of concurrent connections on the server.
#
- Returns: <Buffer> A 48-byte buffer containing the session ticket keys.
Returns the session ticket keys.
See Session Resumption for more information.
#
Starts the server listening for encrypted connections. This method is identical to from .
#
The method replaces the secure context of an existing server. Existing connections to the server are not interrupted.
#
- <Buffer> A 48-byte buffer containing the session ticket keys.
Sets the session ticket keys.
Changes to the ticket keys are effective only for future server connections. Existing or currently pending server connections will use the previous keys.
See Session Resumption for more information.
Class: #
Performs transparent encryption of written data and all required TLS negotiation.
Instances of implement the duplex Stream interface.
Methods that return TLS connection metadata (e.g. will only return data while the connection is open.
#
- <net.Socket> | <stream.Duplex> On the server side, any stream. On the client side, any instance of (for generic stream support on the client side, must be used).
<Object>
- : See
- : The SSL/TLS protocol is asymmetrical, TLSSockets must know if they are to behave as a server or a client. If the TLS socket will be instantiated as a server. Default:.
- <net.Server> A instance.
- : Whether to authenticate the remote peer by requesting a certificate. Clients always request a server certificate. Servers ( is true) may set to true to request a client certificate.
- : See
- : See
- : See
- <Buffer> A instance containing a TLS session.
- <boolean> If , specifies that the OCSP status request extension will be added to the client hello and an event will be emitted on the socket before establishing a secure communication
- : TLS context object created with . If a is not provided, one will be created by passing the entire object to .
- ...: options that are used if the option is missing. Otherwise, they are ignored.
Construct a new object from an existing TCP socket.
Event: #
- <Buffer> Line of ASCII text, in NSS format.
The event is emitted on a when key material is generated or received by the socket. This keying material can be stored for debugging, as it allows captured TLS traffic to be decrypted. It may be emitted multiple times, before or after the handshake completes.
A typical use case is to append received lines to a common text file, which is later used by software (such as Wireshark) to decrypt the traffic:
Event: #
The event is emitted if the option was set when the was created and an OCSP response has been received. The listener callback is passed a single argument when called:
Typically, the is a digitally signed object from the server's CA that contains information about server's certificate revocation status.
Event: #
The event is emitted after the handshaking process for a new connection has successfully completed. The listener callback will be called regardless of whether or not the server's certificate has been authorized. It is the client's responsibility to check the property to determine if the server certificate was signed by one of the specified CAs. If , then the error can be found by examining the property. If ALPN was used, the property can be checked to determine the negotiated protocol.
Event: #
The event is emitted on a client when a new session or TLS ticket is available. This may or may not be before the handshake is complete, depending on the TLS protocol version that was negotiated. The event is not emitted on the server, or if a new session was not created, for example, when the connection was resumed. For some TLS protocol versions the event may be emitted multiple times, in which case all the sessions can be used for resumption.
On the client, the can be provided to the option of to resume the connection.
See Session Resumption for more information.
For TLSv1.2 and below, can be called once the handshake is complete. For TLSv1.3, only ticket-based resumption is allowed by the protocol, multiple tickets are sent, and the tickets aren't sent until after the handshake completes. So it is necessary to wait for the event to get a resumable session. Applications should use the event instead of to ensure they will work for all TLS versions. Applications that only expect to get or use one session should listen for this event only once:
#
Returns the bound , the address name, and of the underlying socket as reported by the operating system: .
#
Returns the reason why the peer's certificate was not been verified. This property is set only when .
#
Returns if the peer certificate was signed by one of the CAs specified when creating the instance, otherwise .
#
Disables TLS renegotiation for this instance. Once called, attempts to renegotiate will trigger an event on the .
#
When enabled, TLS packet trace information is written to . This can be used to debug TLS connection problems.
Note: The format of the output is identical to the output of or . While it is produced by OpenSSL's function, the format is undocumented, can change without notice, and should not be relied on.
#
Always returns . This may be used to distinguish TLS sockets from regular instances.
#
Returns an object representing the local certificate. The returned object has some properties corresponding to the fields of the certificate.
See for an example of the certificate structure.
If there is no local certificate, an empty object will be returned. If the socket has been destroyed, will be returned.
#
Returns an object containing information on the negotiated cipher suite.
For example:
See SSL_CIPHER_get_name for more information.
#
Returns an object representing the type, name, and size of parameter of an ephemeral key exchange in perfect forward secrecy on a client connection. It returns an empty object when the key exchange is not ephemeral. As this is only supported on a client socket; is returned if called on a server socket. The supported types are and . The property is available only when type is .
For example: .
#
- Returns: <Buffer> | <undefined> The latest message that has been sent to the socket as part of a SSL/TLS handshake, or if no message has been sent yet.
As the messages are message digests of the complete handshake (with a total of 192 bits for TLS 1.0 and more for SSL 3.0), they can be used for external authentication procedures when the authentication provided by SSL/TLS is not desired or is not enough.
Corresponds to the routine in OpenSSL and may be used to implement the channel binding from RFC 5929.
#
- <boolean> Include the full certificate chain if , otherwise include just the peer's certificate.
- Returns: <Object> A certificate object.
Returns an object representing the peer's certificate. If the peer does not provide a certificate, an empty object will be returned. If the socket has been destroyed, will be returned.
If the full certificate chain was requested, each certificate will include an property containing an object representing its issuer's certificate.
Certificate object#
A certificate object has properties corresponding to the fields of the certificate.
- <Buffer> The DER encoded X.509 certificate data.
- <Object> The certificate subject, described in terms of Country (), StateOrProvince (), Locality (), Organization (), OrganizationalUnit (), and CommonName (). The CommonName is typically a DNS name with TLS certificates. Example: .
- <Object> The certificate issuer, described in the same terms as the .
- <string> The date-time the certificate is valid from.
- <string> The date-time the certificate is valid to.
- <string> The certificate serial number, as a hex string. Example: .
- <string> The SHA-1 digest of the DER encoded certificate. It is returned as a separated hexadecimal string. Example: .
- <string> The SHA-256 digest of the DER encoded certificate. It is returned as a separated hexadecimal string. Example: .
- <Array> (Optional) The extended key usage, a set of OIDs.
- <string> (Optional) A string containing concatenated names for the subject, an alternative to the names.
- <Array> (Optional) An array describing the AuthorityInfoAccess, used with OCSP.
- <Object> (Optional) The issuer certificate object. For self-signed certificates, this may be a circular reference.
The certificate may contain information about the public key, depending on the key type.
For RSA keys, the following properties may be defined:
- <number> The RSA bit size. Example: .
- <string> The RSA exponent, as a string in hexadecimal number notation. Example: .
- <string> The RSA modulus, as a hexadecimal string. Example: .
- <Buffer> The public key.
For EC keys, the following properties may be defined:
- <Buffer> The public key.
- <number> The key size in bits. Example: .
- <string> (Optional) The ASN.1 name of the OID of the elliptic curve. Well-known curves are identified by an OID. While it is unusual, it is possible that the curve is identified by its mathematical properties, in which case it will not have an OID. Example: .
- <string> (Optional) The NIST name for the elliptic curve, if it has one (not all well-known curves have been assigned names by NIST). Example: .
Example certificate:
#
- Returns: <Buffer> | <undefined> The latest message that is expected or has actually been received from the socket as part of a SSL/TLS handshake, or if there is no message so far.
As the messages are message digests of the complete handshake (with a total of 192 bits for TLS 1.0 and more for SSL 3.0), they can be used for external authentication procedures when the authentication provided by SSL/TLS is not desired or is not enough.
Corresponds to the routine in OpenSSL and may be used to implement the channel binding from RFC 5929.
#
Returns a string containing the negotiated SSL/TLS protocol version of the current connection. The value will be returned for connected sockets that have not completed the handshaking process. The value will be returned for server sockets or disconnected client sockets.
Protocol versions are:
See the OpenSSL documentation for more information.
#
Returns the TLS session data or if no session was negotiated. On the client, the data can be provided to the option of to resume the connection. On the server, it may be useful for debugging.
See Session Resumption for more information.
Note: works only for TLSv1.2 and below. For TLSv1.3, applications must use the event (it also works for TLSv1.2 and below).
#
- Returns: <Array> List of signature algorithms shared between the server and the client in the order of decreasing preference.
See SSL_get_shared_sigalgs for more information.
#
Keying material is used for validations to prevent different kind of attacks in network protocols, for example in the specifications of IEEE 802.1X.
Example
See the OpenSSL documentation for more information.
#
For a client, returns the TLS session ticket if one is available, or . For a server, always returns .
It may be useful for debugging.
See Session Resumption for more information.
#
- Returns: <boolean> if the session was reused, otherwise.
See Session Resumption for more information.
#
Returns the string representation of the local IP address.
#
Returns the numeric representation of the local port.
#
Returns the string representation of the remote IP address. For example, or .
#
Returns the string representation of the remote IP family. or .
#
Returns the numeric representation of the remote port. For example, .
#
<Object>
- <boolean> If not , the server certificate is verified against the list of supplied CAs. An event is emitted if verification fails; contains the OpenSSL error code. Default:.
<Function> If returned , callback is attached once to the event. If returned , will be called in the next tick with an error, unless the has been destroyed, in which case will not be called at all.
Returns: <boolean> if renegotiation was initiated, otherwise.
The method initiates a TLS renegotiation process. Upon completion, the function will be passed a single argument that is either an (if the request failed) or .
This method can be used to request a peer's certificate after the secure connection has been established.
When running as the server, the socket will be destroyed with an error after timeout.
For TLSv1.3, renegotiation cannot be initiated, it is not supported by the protocol.
#
The method sets the maximum TLS fragment size. Returns if setting the limit succeeded; otherwise.
Smaller fragment sizes decrease the buffering latency on the client: larger fragments are buffered by the TLS layer until the entire fragment is received and its integrity is verified; large fragments can span multiple roundtrips and their processing can be delayed due to packet loss or reordering. However, smaller fragments add extra TLS framing bytes and CPU overhead, which may decrease overall server throughput.
#
Verifies the certificate is issued to .
Returns <Error> object, populating it with , , and on failure. On success, returns <undefined>.
This function can be overwritten by providing alternative function as part of the option passed to . The overwriting function can call of course, to augment the checks done with additional verification.
This function is only called if the certificate passed all other checks, such as being issued by trusted CA ().
#
<Object>
- : See
- <string> Host the client should connect to. Default:.
- <number> Port the client should connect to.
- <string> Creates Unix socket connection to path. If this option is specified, and are ignored.
- <stream.Duplex> Establish secure connection on a given socket rather than creating a new socket. Typically, this is an instance of , but any stream is allowed. If this option is specified, , and are ignored, except for certificate validation. Usually, a socket is already connected when passed to , but it can be connected later. Connection/disconnection/destruction of is the user's responsibility; calling will not cause to be called.
- <boolean> If the option is missing, indicates whether or not to allow the internally created socket to be half-open, otherwise the option is ignored. See the option of for details. Default:.
- <boolean> If not , the server certificate is verified against the list of supplied CAs. An event is emitted if verification fails; contains the OpenSSL error code. Default:.
<Function>
- hint: <string> optional message sent from the server to help client decide which identity to use during negotiation. Always if TLS 1.3 is used.
- Returns: <Object> in the form or to stop the negotiation process. must be compatible with the selected cipher's digest. must use UTF-8 encoding. When negotiating TLS-PSK (pre-shared keys), this function is called with optional identity provided by the server or in case of TLS 1.3 where was removed. It will be necessary to provide a custom for the connection as the default one will try to check host name/IP of the server against the certificate but that's not applicable for PSK because there won't be a certificate present. More information can be found in the RFC 4279.
- : <string[]> | <Buffer[]> | <TypedArray[]> | <DataView[]> | <Buffer> | <TypedArray> | <DataView> An array of strings, s or s or s, or a single or or containing the supported ALPN protocols. s should have the format e.g. , where the byte is the length of the next protocol name. Passing an array is usually much simpler, e.g. . Protocols earlier in the list have higher preference than those later.
- : <string> Server name for the SNI (Server Name Indication) TLS extension. It is the name of the host being connected to, and must be a host name, and not an IP address. It can be used by a multi-homed server to choose the correct certificate to present to the client, see the
With the plugin updates 1.4 of Crossmap and Walls & Tiles we have introduced a new licensing system that allows for node-locked and floating licenses. Each license now requires ONLINE ACTIVATION and includes 2 activations with one serial number, so you can use each activated plugin (with one serial) on up to two machines, your workstation and laptop or two workstations. Rendernodes still don´t require activation and will not be limited in the number of nodes, so you can use as many render nodes as you want. Floating licenses can be extended with additional licenses, that can be purchased separately.
- Nodelocked and Floating Licenses
- Requires ONLINE Activation
- 2 activations per license / serial number
- 14 day full featured demo period
WHY A NEW COPY PROTECTION ?
Well, guess what, mainly because of illegal use! Our previous copy protection included a simple serial number but no online activation. Anyone was able to copy Walls & Tiles and use it with a cracked version of Crossmap. While we believe it should be easy for our loyal customers, we saw that the release of the cracks have increased the website traffic by 10 times, but decreased the sales significantly.
In order to continue the development and improve our software products, we saw no alternative to include a better protection. At the end, you our loyal customers, will benefit from this step, we hope.
The NEW serial number format has 6 x 5 digits with capital and small letters and numbers, e.g.
agr2R-12g0A-45G3A-RYf5H-AtzJW-9AJUz
They can be used for the following plugin versions:
Crossmap Version 1.4.0 and higher
Walls & Tiles Version 1.4.0 and higher
Mosaic Version 1.1.0 and higher
NOTE: If you bought plugins before the updated license system was integrated, you can find the new serial numbers in your MY ACCOUNT in the tab MY LICENSES.
The OLD serial number format had 12 digits with all capital letters and numbers, e.g.
0344QR51F2C16
They can be used for the following plugin versions:
Crossmap Version 1.0 – 1.3.11
Walls & Tiles Version 1.0 – 1.3.2
Mosaic Version 1.0
Color Extract Version 1.0 – 1.1.10
Automap Version 1.0 – 1.0.1
NOTE: Generally, when you buy a PLUGIN product, you will receive a confirmation email that includes the SERIAL NUMBER(s) for each product. In addition you will find the serial numbers in your VP ACCOUNT on the website under MY ACCOUNT – MY LICENSES.
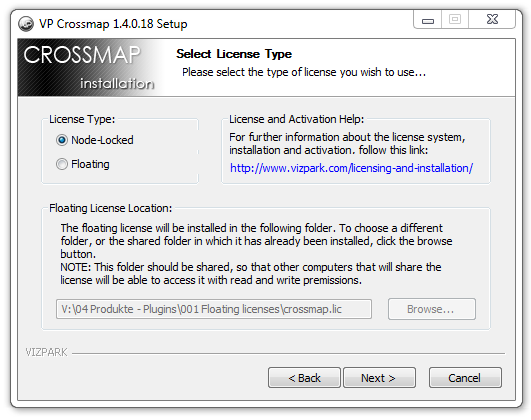
Each plugin comes with an installer that makes installation as simple as possible. During installation you will be asked to choose the license type, either NODE-LOCKED or FLOATING-LICENSE. It´s important to choose wisely, as the license type CANNOT be changed later!
NODE-LOCKED licenses are tied to the computer where the license was installed. So once installed on this computer, it cannot be removed and the license will be used on this computer only.
FLOATING LICENSES can be used in a network by different computers up to the number of licenses that are available. If you decide to use a floating licenses, please make sure that the installed license file can be accessed by all computers in a network with read and write access. Do NOT install the license file locally where other computers in your network cannot access the file.
NOTE: Please be aware that floating licenses will require more user maintenance and network knowledge on your side in terms of accessibility and their concurrent usage in a network environment.

Once the plugins are installed, you will either see an activation screen that pops up when you look for the material or map in the new materials / maps list or you can call the activation screen from the plugin header.
For Walls & Tiles, you need to
1. Activate CROSSMAP and
2. Activate WALLS & TILES.
So you need 2 different serial numbers, which are both provided during purchase. Only when both plugins are activated, you´ll have a permanent license, otherwise, you´ll have the demo period of 14 days after installation.
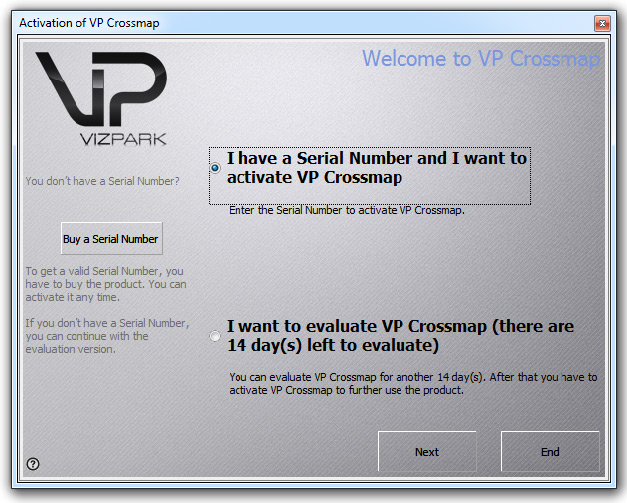
The activation screen has 3 options:
1. ACTIVATION “I have a serial number and I want to activate …” (Activation requires an online connection with the internet!)
2. DEMO “I want to evaluate …” (Which will give for a 14 day demo period of the full plugin, no Internet connection is required here)
3. BUY A SERIAL NUMBER (the button on the left side will lead you to the VIZPARK online shop, where you can purchase a serial number or further floating licenses)
Choose an option and click NEXT …
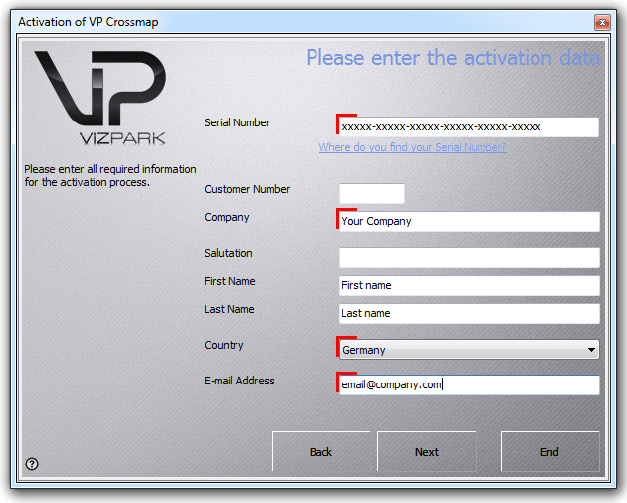
If you choose ACTIVATION, you will be asked to enter your SERIAL NUMBER (which can be found either in your order confirmation email or in your VP ACCOUNT under MY LICENSES), your name, company country and email address. These don´t have to be the same credentials that you have used in the VP online shop, we recommend to use the same though in order to help find your information faster if support is required.
Click NEXT …
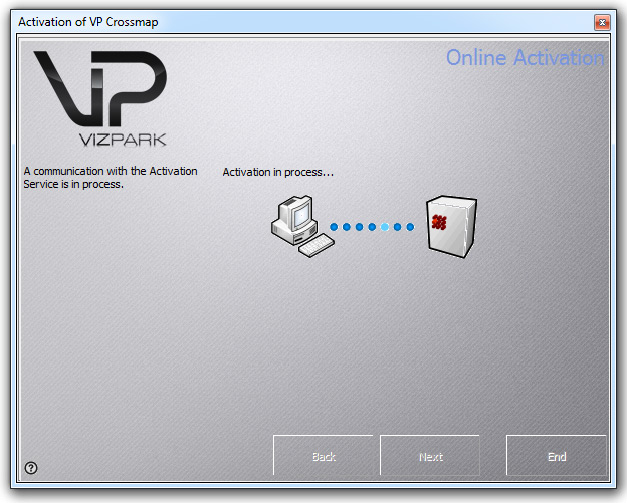
If your computer is connected to the internet and your serial is valid and does not exceed the activation limit (2 activations are allowed), your license will now be activated.
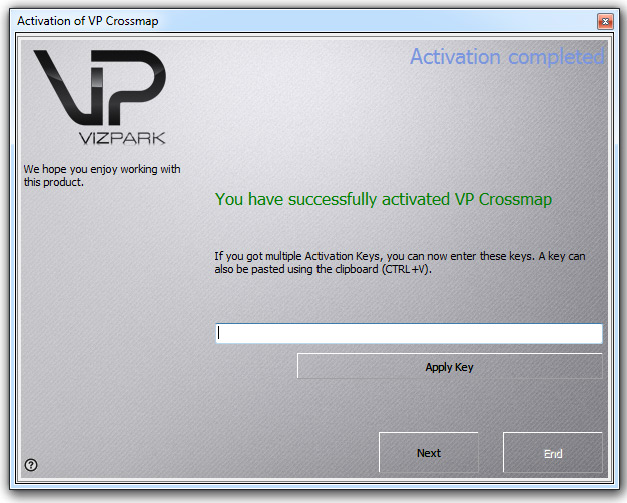
A successful activation will bring up this screen.
If you have bought additional floating licenses, you can enter the activation keys here now ( You can also add additional floating licenses later ).
Click NEXT to finish the activation process.
GREAT! You now have a permanent license!
If you started the activation from the PLUGIN user interface directly (and not while opening the new materials / maps list) then you need to re-load or re-initiate the plugin. Just create a new map or material and the demo note should disappear. With the SHOW LICENSE button(s) you can now open the LICENSE VIEWER.
With the successfully activated plugin, the demo note has disappeared and you have a permanent license. The buttons have changed, so that they open the LICENSE VIEWER.
The LICENSE VIEWER provides information about the demo period, activated licenses, floating licenses and more.
You can also add further floating licenses here. Just use the Activation Key button and add further ACTIVATION KEYS here.
NOTE: Activation keys are different from Serial numbers and you cannot just enter additional serial numbers here if you want to increase the number of floating licenses. ONLY ACTIVATION KEYS for further Floating licenses will work here.

If you have any problems activating the plugins, please send us a Support request, stating your order number, system setup and detailed description of the problem (ideally with screenshots).
Toyota Corolla (E170)
| Toyota Corolla (E170/E180) | |
|---|---|
 | |
| Overview | |
| Manufacturer | Toyota |
| Also called | Toyota Levin (China, GAC Toyota) |
| Production |
|
| Assembly | |
| Designer | Shinichi Yasui (2010, 2011)[2] |
| Body and chassis | |
| Class | Compact car |
| Body style | 4-door sedan |
| Layout | |
| Platform | Toyota New MC platform |
| Related | Toyota Auris (E180) |
| Powertrain | |
| Engine | |
| Transmission |
|
| Dimensions | |
| Wheelbase | 2,700 mm (106.3 in)[3] |
| Length |
|
| Width | 1,775 mm (69.9 in)[3] |
| Height | 1,455–1,460 mm (57.3–57.5 in)[3] |
| Curb weight |
|
| Chronology | |
| Predecessor | Toyota Corolla (E140/E150; wide-body) |
| Successor | Toyota Corolla (E210) |
The Toyota Corolla (E170/E180) is the eleventh generation of the Corolla that has been sold internationally since 2013. Two basic front and rear styling treatments are fitted to the E170—a North American version that debuted first—and a more conservative design for all other markets that debuted later in 2013. For the Japanese and Hong Kong markets, the smaller and unrelated Corolla (E160) is offered instead; the Japanese version remains compliant with Japanese government dimension regulations. The E170/E180 has an increased wheelbase of 100 mm longer than the previous generation. The E170/E180 derives from the Toyota New MC platform, unlike the E160 based on the B platform.


International version[edit]
Asia[edit]
- China
Toyota would sell two versions of the E170 Corolla in China, the international version, called the FAW-Toyota Corolla, which is similar in appearance to the Corolla Altis, and the Guangqi-Toyota Levin, which sports a design closer to the North American version, but is still a separate design (see below).[5] In October 2015, Toyota introduced the Corolla hybrid variant in China with locally produced hybrid systems.[6] Production for the Corolla E170 commenced in June 2014 for the 2015 model year. Engine and transmission choices available are the 1.6 litre 1ZR-FE and 1.8 litre 2ZR-FE paired with 5 speed manual or CVT gearboxes. The Toyota Levin also shares these engines and gearboxes.
In 2017, both versions of the Corolla in China received a facelift and a 1.2-litre 9NR-FTS turbocharged engine. The FAW-Toyota Corolla also had the old 1.6-litre engine as an option but the Levin dropped the 1.6-litre engine.
- India
The Corolla Altis was available in India from April 2014 in two engine forms, in petrol and diesel engines. The 1.8L 2ZR-FE is powered by petrol and the 1.4L (1364 cc) D-4D engine with variable Nozzle turbo and intercooler is powered by diesel.[7] It gets 60/40 reclining rear seats, rain-sensing wipers, eight-way power adjustable seat with lumbar support, LED headlamps and 16-inch alloys on the top-end GL and VL variants, with all variants receiving LED taillamps.[8][9]
It stopped production in March 2020 due to declining sales and did not engineered to meet the Bharat Stage 6 emission standards which came into effect in April. As such, the E210 model would not be introduced to India, making the E170 model as the last Corolla Altis model to be sold in the country.[10][11]
- Indonesia
Indonesia was the first ASEAN country to get the new Corolla Altis, released on 8 January 2014.[12] Unlike the previous generation, it was released with the 1.8 L Dual VVT-i engine only, the 2.0 L Dual VVT-i engine was withdrawn due to small sales.[13] Only 2 variants are offered, the 1.8 G manual transmission and the 1.8 V automatic transmission.
- Malaysia

In Malaysia, the Corolla Altis was launched in January 2014 and came in three variant forms, the baseline 1.8E, the 2.0G and the range-topping 2.0V. All three variants come with CVT transmission with seven-speed sports sequential shift.[14] In November 2014, the 2.0G was replaced with the 1.8G.[15] In December 2016, the facelift model was launched with seven airbags, ABS with EBD and brake assist, Vehicle Stability Control (VSC) and ISOFIX rear child seat anchors as standard equipment.[16] In September 2017, the range was updated with DVR dash cam, 360-degree Panoramic View Monitor and additional USB ports.[17]
| Model | Engine | Power | Torque |
|---|---|---|---|
| 1.8E | 1798 cc 2ZR-FE I4 | 103 kW (140 PS) at 6,400 rpm | 173 N⋅m (128 lb⋅ft) at 4,000 rpm |
| 1.8G | |||
| 2.0G | 1987 cc 3ZR-FE I4 | 107 kW (145 PS) at 6,200 rpm | 187 N⋅m (138 lb⋅ft) at 3,600 rpm |
| 2.0V |
- Pakistan
The eleventh generation Corolla was launched in July 2014 in Paksitan. As of September 2014[update], a total of five trim levels were being sold; XLi 1.3L Manual, GLi 1.3L (with option of both automatic and manual transmission), Altis 1.6L (automatic only), Altis 1.8L and Altis Grande 1.8L. Pakistan is among the few countries in which the 1.3L variant is offered.
Corolla XLi and GLi 1.3L (E170) are having 2NZ-FEVVT-i mated with either 5-speed manual or 4-speed automatic transmission, Corolla Altis 1.6L (E171) is having 1ZR-FEDual VVT-i engine with mated 4-speed automatic transmission, Corolla Altis 1.8L or Altis Grande 1.8L (E172) is having 2ZR-FEDual VVT-i with the choice of 6-speed manual or 7-speed CVT-i.
Toyota Pakistan have upgraded the features of whole Corolla's lineup in April 2016, with the most features being offered in the top spot variant known as Corolla Altis Grande. Some of the features of Altis Grande 1.8L are CVT-i, automatic air conditioning with climate control, immobilizer anti-theft system, jack knife key, WOW meter, sunroof, 16-inches Hyper Black alloy wheels, leather interior with bucket seats, 8-inch Android infotainment system, multimedia steering keys, driver + passenger SRS airbags, auto-fold outdoor rear view mirrors (ORVM), 6:4 rear reclining seats, body colored mud flaps, etc.[18] Toyota Pakistan introduced the facelifted version in August 2017.
- Philippines
The Corolla Altis was first released in the country in early 2014, with five trims available. The entry-level 1.6 E model only came with a six-speed manual transmission, four-beam halogen headlamps, fabric upholstery, and 16-inch alloy wheels. The mid-range 1.6 G variant adds TVSS and fog lights and is available in six-speed manual or seven-speed continuously-variable transmission. The 1.6 V variant features a push starter and cornering sensors, and the high-end 2.0 V adds LED headlamps with DRLs, paddle shifters, rain sensing wipers, leather seats, 17-inch alloy wheels, and sport body kit. A minor update for the Altis was later released in December 2016. All variants now received DRL and updated safety features such as 7 airbags, ABS and EBD. 1.6 variants are still equipped with 4 lamp halogen headlights, beige interior and while the 2.0 variant gets projected HID headlamps, wrap around bodykits and leather interior.
- Singapore

The new Corolla Altis was available from 10 January 2014 offering only with the 1.6L 1ZR-FE engine with Dual VVT-i mated to a 7-speed Sequential transmission with Super CVT-i. Initially offered as a single trim, the line up was split into Classic and Elegance variants with the former using multi-reflector headlamps and comes with 16-inch rims, the latter adds LED headlamps with DRLs, keyless entry with push button start, auto-dimming rear view mirror, Nanoe ionizer for the climate control and 17-inch alloy wheels. In mid 2017, the facelift model was launched, with Eco, Standard and Elegance trims. Safety features such as seven airbags, ABS with EBD and brake assist, Vehicle Stability Control (VSC) were standard across all trims. The Eco variant which had 15” alloy rims, leather seats and does without fog lamps was later removed from the lineup after a short period since the facelift introduction.
Japanese-market models (Axio and Fielder Wagon) were also available and sold by grey market importers.
- Taiwan
The new generation Corolla is marketed as the "Corolla Altis" (used in Southeast Asian markets and some parts of Asia). This generation has an overall redesigned look for the Asian market setting it apart from the American market. The Corolla Altis is only available with a 1.8 L Dual VVT-i2ZR-FE engine with variants such as the Classic, 1.8E Deluxe, Elegance and 1.8 Z.[19] In 2015, an additional sportier version was added to the lineup with the Corolla Altis X moniker. Designed and sold exclusively in Taiwan, the model featured a redesigned front bumper heavily influenced by the 2014 North American Camry facelift, a redesigned lower rear bumper, side skirts, clear tail lamps, and spoilers.In October 2016, the facelift model was launched, with Eco, Standard and Elegance trims. Safety features such as seven airbags, ABS with EBD and brake assist, Vehicle Stability Control (VSC) were standard across all trims.
On 21 September 2017, the updated Corolla Altis X was launched, with the similar front bumper design as the updated Chinese market Levin.[20]
- Thailand
The Corolla Altis introduced in Thailand, which currently manufactures the Corolla Altis, is offered a total of seven grades (J, E, G and V), as well as a special edition grade (E Sport). Thailand is currently the only country that offers all existing grades of the new Altis, whilst export markets are only given a fraction of the Thai range in varying combinations.
Unlike most markets in Southeast Asia, CNG powered grades are offered for the 1.6L variants of the Corolla Altis. A special edition grade (E Sport) is also offered only in Thailand which comes with an aerodynamic bodykit including a rear spoiler, sport seats and 17-inch multi-spoke alloys.[21]
Grades available for the Corolla Altis in Thailand varies from the basic 1.6J to the high spec 1.8V Navi variant.
| Model | Engine | Power | Torque |
|---|---|---|---|
| 1.6E CNG | 1598 cc 1ZR-FBE I4 | 92 kW (125 PS) at 6,000 rpm | 157 N⋅m (116 lb⋅ft) at 5,200 rpm |
| 1.6G | |||
| 1.8E / 1.8 Esport | 1798 cc 2ZR-FBE I4 | 104 kW (141 PS) at 6,000 rpm | 177 N⋅m (131 lb⋅ft) at 4,000 rpm |
| 1.8V / 1.8S |
Australia[edit]

Toyota in Australia and New Zealand launched the E170 series Corolla sedan in late February 2014. An equivalent hatchback model is also retailed under the Corolla nameplate, but this is actually a rebadged Auris released earlier in 2012. For the sedan version, which is imported from Thailand, there are three different variants: the base Ascent, the mid range SX model, and the flagship ZR. The Corolla sedan and hatchback (Auris) were together in 2014 the top selling car in Australia.[22]
South Africa (E180)[edit]
In South Africa, the E180 Corolla was launched on 7 February 2014 with a choice of three gasoline engines (1.3-, 1.6- and 1.8-liter) and a 1.4-liter D-4D diesel engine. All engines are mated to a standard six-speed manual transmission while a CVT is available for the 1.6- and 1.8-liter variants. Trim levels are the base Esteem, the mid-level Prestige, the sporty Sprinter and the top-of-the-line Exclusive.[23] The facelifted version of the E180 Corolla went on sale on 25 January 2017.[24] The facelifted E180 Corolla retained the pre-facelift model tail lamps for the Esteem trim and the Sprinter trim was discontinued. The E180 Corolla is still currently produced and sold in South Africa as the Corolla Quest, which was revealed on 31 January 2020 and released in March 2020.[25]
Europe[edit]
In February 2014, Toyota introduced the Corolla E180 in Germany, western Europe's largest national automobile market.[27] This marked the return of the "Corolla" badge to Germany after an absence of seven years[27] (although the previous Corolla E140 was sold in some smaller European markets, such as Belgium). The line-up includes a 1.4-litre D-4D turbodiesel and petrol engines ranging from a 1.33-litre Dual VVT-i engine, a 1.6-litre engine available with Dual VVT-i and Valvematic system, and a new 1.8-litre Dual VVT-i engine.
The 1.8-litre Dual VVT-i petrol engine is fitted as standard with a new Multidrive S automatic transmission. All other engines in the line-up are fitted with six-speed manual transmissions.
Facelift[edit]
The facelifted international version of the E170/E180 Corolla was unveiled on 24 March 2016.[28] It features sleeker LED headlamps with new LED light guides, thinner upper grille with a chrome garnish, a full width lower grille that houses the foglamps. At the rear the chrome strip is thinner and the tail lamps adopt new LED clusters.[29] The facelifted E170 Corolla Altis was launched in Thailand on 21 November 2016,[30] in the Philippines on 8 December 2016,[31] in Malaysia on 9 December 2016,[16] in Indonesia on 16 January 2017,[32] in Singapore in July 2017 and in Pakistan in August 2017.

Toyota Corolla Ascent sedan (Australia; facelift)

Toyota Corolla Ascent sedan (Australia; facelift)
North American version[edit]


The North American Corolla is very similar to the international version, except for offering revised front and rear styling. This design was adopted from the Furia concept. North American models were announced first on June 6, 2013; European models, announced the day after, differed mostly outside with their front-end treatment. The engines were closely related to the previous models, with only slight improvements in performance and emissions.
The eleventh generation Corolla falls under North America's compact car market segment, and it is offered in four grades, L, LE, LE Eco and S. The Corolla is a perennially top-selling model[33] in North America, and the world.[34] Many of the changes in the new model were inherited from Toyota's Furia concept car, with the most striking difference from the previous generation being mostly cosmetic. Toyota focused on fuel efficiency with this new design, while continuing the longstanding trend of increasing size and weight.
The Corolla manufactured in Cambridge, Ontario, Canada has about 25 percent of its parts coming from Japan.[35]
Two, four-cylinder engines are available, the 1.8-liter 2ZR-FE with 132 horsepower (98 kW), and a Valvematic equipped 2ZR-FAE offered on the new "Eco" trim, providing 140 horsepower (100 kW). The Corolla will be available with a four-speed automatic, six-speed manual, or Toyota's new CVTi-S Continuously-Variable Transmission.[36]
Stylistic elements of this generation of the Corolla were previewed in the Furia concept car shown at the January 2013 Detroit Auto Show. Hints of the swept windshield and sloped roofline suggest the brand will follow the industry trend toward raked rear ends and more aerodynamic body shapes. It is also likely that the elements such as the LED lighting seen on the concept will make it into the next Corolla's design.[37]
Many design cues were inherited from the Toyota Furia concept car;[38]
- Underbody and floor pan bracing help improve the Corolla platform's structural rigidity.[39]
- High-strength steel, extensive testing and computer simulation have helped produce a highly rigid unibody that provides superior safety for its occupants.[39]
- Efforts to reduce wind resistance have helped the new Corolla achieve a drag coefficient of Cd=0.28(LE Eco only[40]), which places it near the top of the compact-sedan class.[39]
- The LE Eco trim has improved aerodynamics.[3]
For the E170 Corolla model, the transmission uses an electric-power-steering system, offering improved directness and weight. The components of the tilt, telescopic-steering structure help improve steering rigidity and reduce vibration. Its steering turns lock-to-lock measures 3.19 turns total.
The brakes are a 275 mm (10.8 in) ventilated front disc, and a 229 mm (9.0 in) rear drum with the option of a 259 mm (10.2 in) solid rear disc on the S trim. It will feature Toyota's Star Safety System standard including Vehicle Stability Control (VSC), Traction Control (TRAC), Anti-lock Braking System (ABS), Electronic Brake-force Distribution (EBD) and Brake Assist. Smart Stop Technology brake-override system will also be included standard, as well as electronic tire pressure monitoring system.[39]
The standard wheels on the L and LE Eco grades are 15-inch covered steel, with 16-inch wheels on the LE and S. Different 16-inch aluminum alloy wheels are offered on the LE, and LE Eco, and 17-inch alloy wheels are offered on the S. The tire on the LE Eco are low rolling resistance 195/65R-15 rubber. The S 17-inch option offers 215/45R-17 rubber. For the LE, and on the alloy option for the LE Eco model, a 205/55R-16 tire is used.
- longer wheelbase of 2,700 mm (106.3 in)[3]
- 15-, 16-, 17-inch steel and alloy wheels[3]
Toyota's new Corolla offers two engine selections, both all aluminium, 1.8-liter inline four cylinder engines. With the exception of the LE Eco trim, the 1.8-liter engine is equipped with dual Intelligent VVT-i variable valve timing, producing 98 kW (132 hp). The LE Eco model has a 104 kW (140 hp) engine featuring Toyota's Valvematic option, which improves the Eco model's fuel efficiency. Valvematic offers a broader range of continuously variable valve timing (lift and phasing) over VVT-i, providing more optimal intake valve (not on exhaust side) operation relative to engine demands conferring a five-percent improvement in fuel economy and engine output.[3][39] The Eco model's engine also has an increased compression ratio of 10.6:1.[41]
The base model Corolla L is offered with a four-speed automatic transmission or a six-speed manual transmission. The six-speed manual is also available in the Corolla S.
- A six-speed manual transmission is available on the Corolla L and S grades. Drive modes that offer re-calibrated throttle, transmission and steering responses are available on the Corolla LE Eco and Corolla S. For ECO drive mode on the LE Eco, the initial throttle inputs are less sensitive to help encourage more fuel-efficient driving and eliminate sudden starts. On the S grade, the SPORT mode software helps make the accelerator pedal feel more responsive to input along with CVTi-S shifting logic that enhances acceleration feel. In sport mode, Corolla's electronic power steering is programmed to offer a more positive steering feel.[3]
- The unibody makes extensive use of lightweight, high-strength steel to help keep vehicle weight below 2,900 pounds in the interest of fuel economy. In addition to improved collision performance, such construction also gives the Corolla's structure increased rigidity to optimize chassis and suspension performance, giving the new car a more responsive and engaging driving experience.[3]
Toyota is offering a new Continuously Variable Transmission on the LE, LE Eco and S trims, which they claim is more smooth, and improves fuel efficiency, named the CVTi-S (Continuously Variable Transmission intelligent-shift). The diameter ratio between small and large internal pulleys has been increased without increasing the unit's case size achieving a ratio range of 6.3, improving fuel efficiency and acceleration.[39] Its forward gear ratio range is from 0.396 to 2.480 and it has a 4.761 final drive ratio. A transmission fluid warmer was added, reducing warm-up time, and lower viscosity CVT fluid improves efficiency. Its new fluid pump reduces parasitic loss at high speeds. The transmission's software creates discrete sequential shift points to emulate traditional transmissions while accelerating. The S trim offers a manual-mode shift gate in the console shifter, or paddle shifters on the steering wheel allowing sequential "shifts" through 7 speeds, addressing complaints that earlier pulley-type CVTs had a "rubber band" feel when accelerating because of the lag as the transmission entered its power band.[3]
Typical CVT designs require a high level of hydraulic pressure for operation, and CVT hydraulic-fluid pumps are typically driven at the same rate as engine speed, leading to pumps wasting considerable effort, lowering transmission efficiency at higher engine speeds as the pump moves more fluid than necessary to lubricate and sandwich the CVT's belt. Hydraulic pressure was reduced to an optimal point to protect against belt slippage, while conserving drive effort to limit excess pumping losses in the new design; also, the oil pump features a coaxial 2-port design that enables a 25-percent reduction in pump drive torque, lowering its parasitic draw on the engine.[3][39]
On the LE Eco, the transmission has an ECO driving mode. The ECO driving mode makes accelerator control become non-linear to suppress the vehicle's response to choppy driving and contain acceleration from standing start to reduce fuel consumption. The accelerator pedal's communication is the same as Normal mode after 50-percent throttle. The air conditioning operation is also controlled, with compressor power reduced, and the utilization of recirculation mode, as well as increasing the time to reach a desired temperature.[3][39]


The S trim offers a SPORT mode with software tuning that alters shift points along with unique electric power steering programming, helping create a sportier driving sensation during normal road and freeway driving. S trim models with CVTi-S have steering wheel mounted paddle shifters, while the console shifter also offers a manual gate (M-position) that also allows drivers to make brisk upshifts or downshifts using the shift lever. An appropriate shift will automatically be engaged if the engine revolutions become high enough or down shifted if they become low enough.[3][39]
The front suspension uses Macpherson struts with a new, more rigid control-arm design, while the rear uses a torsion beam arrangement. The spring rates on Corolla are relaxed, but the S model equipped with 17-inch wheels includes unique coil, damper, and bushing tuning to offering stiffer handling. The rear torsion beam's attachments points are now fastened to the body at a slanted, diagonal angle for its bushings, a departure from the traditional straight attachment orientation; the new layout contributes improves grip, and stability.
The unibody has been made more rigid, featuring additional unibody bracing (tunnel brace and rear floor brace) to complement suspension tuning. It makes extensive use of high-strength steel to improve the rigidity of the structure, keeping vehicle curb weight under 2,900 pounds for all grades. High tensile-strength steel allows for reduced thickness and optimized shape of structural panels and increases strength to improve collision performance. Corolla is expected to perform very well in collision safety ratings test.[3][39]
- First compact car with standard LED lowbeam headlamps[3]
- Vehicle under covers help reduce turbulent airflow; the rear spare wheel well has an under cover with fins.[39]
- Both the LE Eco grade and S grade offer strategically placed vehicle under covers located below the bumper fascia, engine, front floor, rear floor, and fuel tank to help manage airflow under the vehicle for improved efficiency.[39]
- Additional leg-room was gained by adopting a slim front seat back. The rear passenger floor was also made flatter by re-routing exhaust pipes beneath the vehicle to offer better middle position foot room. Rear seat comfort is also enhanced with the use of denser urethane pads and foam inserts within the seats.[39]
- All models are standard equipped with eight airbags, and Bluetooth hand-free phone and audio-streaming connectivity. The Corolla will be available in four trim levels (L, LE, LE Eco, and S) that offer a wide range of popular features to help distinguish each trim level.
Special Edition[edit]
In 2014, for the 2015 model year, Toyota released the Special Edition Corolla based on the S model. It has gloss black-painted 17-inch alloy wheels, red stitching on its black steering wheel, shift knob, door trim, and seats, Special Edition floor mats and trunk emblem. In Canada, this model is called the 50th Anniversary Limited Edition. Absolutely Red, Super White, and Black Sand Pearl are the only exterior colors offered.[42][43]
Facelift[edit]


In 2016 for the 2017 model year, Toyota released the facelift version of the E170 Corolla with new aerodynamic scoops, (only for 50th anniversary edition) restyled front facia, including new headlight design; redesigned taillights also featured. The interior added a new seven-inch touch screen and four-inch multi-information display. The updated Corolla features the new SE, and XSE grades, and new exterior colors.[44][45]
Toyota Levin (China)[edit]
In addition to the FAW-Toyota Corolla sold in China that is based on the Corolla Altis, in 2014 Toyota China released the Guangqi-Toyota Levin (Japanese: トヨタ・レビン, Toyota Rebin).[46] In October 2015, Toyota introduced the Corolla hybrid variant in China with locally produced hybrid systems.[6]
The Levin has different frontal styling compared to both the North American Corolla and the international version. The grille is a slim piece dominated by chrome strip along the top that continues above the headlamps (that have been designed as a cross between the North American Corolla's lights and the international Corolla's wrap-around units). The lower intake is trapezoidal-shaped like the regular (non-sport) grade North American Corolla, but for China features a chrome surround. At the rear, the Levin's lights are based on the North American Corolla—the rear three-quarter panels and bumper are the identical. However, the reshaped trunk lid has the Toyota logo moved upwards to make way for the dominating chrome strip that bridges the tail lamps. The outer portions of the Levin's tail-lamps are the same shape as the Corolla for North America. However, the inner portion that sit upon the trunk lid are resigned. Also, the North American Corolla's tailpipe pokes straight out from underneath the rear bumper; the Levin's tailpipe curves downwards.[47]
The Levin received an update at the April 2017 Auto Shanghai, with the similar front bumper design as the updated Taiwanese market Corolla Altis X.[48]
References[edit]
- ^"國瑞汽車股份有限公司 KUOZUI MOTORS, LTD". Kuozui.com.tw. Retrieved 1 October 2013.
- ^"Shinichi Yasui, Chief Engineer for the 10th and 11th generation Corolla" (Press release). Toyota. 27 October 2016. Retrieved 20 November 2018.
- ^ abcdefghijklmnopqrs"Toyota Elevates Expectations with the Surprising 2014 Corolla" (Press release). US: Toyota. 6 June 2013. Retrieved 9 July 2013.
- ^"The all-new Corolla Altis – heart pounding"(PDF). Toyota Motor Philippines. Archived from the original(PDF) on 29 June 2016.
- ^Tan, Jonathan James (21 April 2014). "Toyota Corolla, Levin hybrids to be made in China". Paultan.org. Retrieved 5 May 2014.
- ^ ab"Worldwide Sales of Toyota Hybrids Surpass 9 Million Units" (Press release). Japan: Toyota. 20 May 2016. Retrieved 22 May 2016.
- ^"2014 Toyota Corolla Altis to arrive in India; details inside". cardekho. Retrieved 14 April 2014.
- ^Prabhakar, Halley (16 May 2014). "2014 Toyota Corolla Altis India first drive". India: Overdrive. Retrieved 8 September 2016.
- ^"Toyota Corolla Altis brochure"(PDF). India: Toyota Kirloskar Motor. May 2014. Archived from the original(PDF) on 2 June 2014.
- ^https://www.news18.com/news/auto/toyota-corolla-was-the-best-selling-car-in-the-world-in-2019-2584913.html
- ^https://paultan.org/2020/04/14/toyota-stops-sale-of-corolla-altis-etios-in-india-to-make-way-for-new-models-advanced-tech-report/
- ^Aszhari, Arief (8 January 2014). "Kesempurnaan All New Corolla Altis". Okezone Autos (in Indonesian). Retrieved 8 January 2014.
- ^Aszhari, Arief (8 January 2014). "Alasan Toyota Tak Bawa Altis 2,0 Liter". Okezone Autos (in Indonesian). Retrieved 8 January 2014.
- ^Lim, Anthony (20 January 2014). "2014 Toyota Corolla Altis officially launched". paultan.org. Retrieved 2 February 2014.
- ^"Toyota Corolla Altis 1.8G new variant introduction" (Press release). Toyota Malaysia. 7 November 2014. Archived from the original on 2 April 2015. Retrieved 1 April 2015.
- ^ abLee, Jonathan (9 December 2016). "Toyota Corolla Altis facelift now on sale, from RM121k". paultan.org. Retrieved 22 January 2017.
- ^"Toyota Corolla Altis gets new options - DVR dash cam, 360-degree Panoramic View Monitor, USB chargers". Paul Tan's Automotive News. 5 September 2017. Retrieved 25 January 2018.
- ^"All New Toyota Corolla | Facebook". www.facebook.com. Retrieved 20 August 2016.
- ^"Taiwan – 2014 Toyota Corolla Altis debuts in Asia; Sporty 'Z' variant introduced". indianautosblog. Retrieved 15 April 2014.
- ^"「X」正夯 TOYOTA Corolla Altis X售價77.9萬" ["X" is ramming TOYOTA Corolla Altis X price of 779,000]. UDN Autos (in Chinese). 21 September 2017. Retrieved 22 September 2017.
- ^"Bangkok Live – Toyota Corolla Altis ESport, Altis TRD Edition". indianautosblog. Retrieved 15 April 2014.
- ^O'Brien, Tim (18 February 2014). "2014 Toyota Corolla Sedan Review". The Motor Report. Retrieved 22 February 2014.
- ^"2014 Toyota Corolla Launched in SA". Cars.co.za. 7 February 2014. Retrieved 5 February 2020.
What’s New in the 4D Engine 6.0.x serial key or number?
Screen Shot

System Requirements for 4D Engine 6.0.x serial key or number
- First, download the 4D Engine 6.0.x serial key or number
-
You can download its setup from given links:




