
Just Checking v2.16 by MaTHieU serial key or number

Just Checking v2.16 by MaTHieU serial key or number
Keys of Heaven

The Keys of Heaven refers to the image of crossed keys used in ecclesiastical heraldry, to represent the metaphorical keys of the office of Saint Peter, the keys of heaven, or the keys of the kingdom of Heaven.
In Catholicism[edit]
According to Catholic teaching,[1]Jesus promised the keys to heaven to Saint Peter, empowering him to take binding actions.[2] In the Gospel of Matthew16:19, Jesus says to Peter, "I will give you the keys of the kingdom of heaven, and whatever you bind on Earth shall be bound in heaven, and whatever you loose on Earth shall be loosed in heaven." Saint Peter is often depicted in Catholic and Eastern Orthodox paintings and other artwork as holding a key or a set of keys.
The keys of heaven or keys of Saint Peter are seen as a symbol of papal authority and are seen on papal coats of arms (those of individual popes) and those of the Holy See and Vatican City State: "Behold he [Peter] received the keys of the kingdom of heaven, the power of binding and loosing is committed to him, the care of the whole Church and its government is given to him [cura ei totius Ecclesiae et principatus committitur (Epist., lib. V, ep. xx, in P.L., LXXVII, 745)]".[3]
Biblical sources[edit]
Bible verses associated with Peter[4][5] and his position of authority: Is. 22:20-23; Matt. 10:2; Matt. 16:18-19; Luke 22:32; John 21:17; Acts 2:14; Acts 10:46; Gal. 1:18.
Bible verses associated with the transfer of powers from Pope to Pope: Acts 1:20; 6:6; 13:3; 8:18; 9:17; 1 Tim. 4:14; 5:22; 2 Tim. 1:6.
Symbols depicting the Keys of Heaven[edit]
In Catholicism[edit]
Elsewhere[edit]
See also[edit]
References[edit]
External links[edit]
GnuPG 2.0.28 released (2015-06-02)
GnuPG 2.0.27 released (2015-02-18)
GnuPG 2.0.26 released (2014-08-12)
GnuPG 2.0.25 released (2014-06-30)
GnuPG 2.0.24 released (2014-06-24)
GnuPG 2.0.23 released (2014-06-03)
GnuPG 2.0.22 released (2013-10-04)
GnuPG 2.0.21 released (2013-08-19)
GnuPG 2.0.20 released (2013-05-10)
GnuPG 2.0.19 released (2012-03-27)
GnuPG 2.0.18 released (2011-08-04)
GnuPG 2.0.17 released (2011-01-13)
GnuPG 2.0.16 released (2010-07-19)
GnuPG 2.0.15 released (2010-03-09)
GnuPG 2.0.14 released (2009-12-21)
GnuPG 2.0.13 released (2009-09-04)
- GPG now generates 2048 bit RSA keys by default. The default hash algorithm preferences has changed to prefer SHA-256 over SHA-1. 2048 bit DSA keys are now generated to use a 256 bit hash algorithm
- The envvars XMODIFIERS, GTK_IM_MODULE and QT_IM_MODULE are now passed to the Pinentry to make SCIM work.
- The GPGSM command –gen-key features a –batch mode and implements all features of gpgsm-gencert.sh in standard mode.
- New option –re-import for GPGSM's IMPORT server command.
- Enhanced writing of existing keys to OpenPGP v2 cards.
- Add hack to the internal CCID driver to allow the use of some Omnikey based card readers with 2048 bit keys.
- GPG now repeatly asks the user to insert the requested OpenPGP card. This can be disabled with –limit-card-insert-tries=1.
- Minor bug fixes.
GnuPG 2.0.12 released (2009-06-17)
- GPGSM now always lists ephemeral certificates if specified by fingerprint or keygrip.
- New command "KEYINFO" for GPG_AGENT. GPGSM now also returns information about smartcards.
- Made sure not to leak file descriptors if running gpg-agent with a command. Restore the signal mask to solve a problem in Mono.
- Changed order of the confirmation questions for root certificates and store negative answers in trustlist.txt.
- Better synchronization of concurrent smartcard sessions.
- Support 2048 bit OpenPGP cards.
- Support Telesec Netkey 3 cards.
- The gpg-protect-tool now uses gpg-agent via libassuan. Under Windows the Pinentry will now be put into the foreground.
- Changed code to avoid a possible Mac OS X system freeze.
GnuPG 2.0.11 released (2009-03-03)
- Fixed a problem in SCDAEMON which caused unexpected card resets.
- SCDAEMON is now aware of the Geldkarte.
- The SCDAEMON option –allow-admin is now used by default.
- GPGCONF now restarts SCdaemon if necessary.
- The default cipher algorithm in GPGSM is now again 3DES. This is due to interoperability problems with Outlook 2003 which still can't cope with AES.
GnuPG 2.0.10 released (2009-01-12)
- [gpg] New keyserver helper gpg2keys_kdns as generic DNS CERT lookup. Run with –help for a short description. Requires the ADNS library.
- [gpg] New mechanisms "local" and "nodefault" for –auto-key-locate. Fixed a few problems with this option.
- [gpg] New command –locate-keys.
- [gpg] New options –with-sig-list and –with-sig-check.
- [gpg] The option "-sat" is no longer an alias for –clearsign.
- [gpg] The option –fixed-list-mode is now implicitly used and obsolete.
- [gpg] New control statement %ask-passphrase for the unattended key generation.
- [gpg] The algorithm to compute the SIG_ID status has been changed.
- [gpgsm] Now uses AES by default.
- [gpgsm] Made –output option work with –export-secret-key-p12.
- [gpg-agent] Terminate process if the own listening socket is not anymore served by ourself.
- [scdaemon] Made it more robust on W32.
- [gpg-connect-agent] Accept commands given as command line arguments.
- [w32] Initialized the socket subsystem for all keyserver helpers.
- [w32] The sysconf directory has been moved from a subdirectory of the installation directory to %CSIDL_COMMON_APPDATA%/GNU/etc/gnupg.
- [w32] The gnupg2.nls directory is not anymore used. The standard locale directory is now used.
- [w32] Fixed a race condition between gpg and gpgsm in the use of temporary file names.
- The gpg-preset-passphrase mechanism works again. An arbitrary string may now be used for a custom cache ID.
- Admin PINs are cached again (bug in 2.0.9).
- Support for version 2 OpenPGP cards.
- Libgcrypt 1.4 is now required.
GnuPG 2.0.9 released (2008-03-26)
- Gpgsm always tries to locate missing certificates from a running Dirmngr's cache.
- Tweaks for Windows.
- The Admin PIN for OpenPGP cards may now be entered with the pinpad.
- Improved certificate chain construction.
- Extended the PKITS framework.
- Fixed a bug in the ambigious name detection.
- Fixed possible memory corruption while importing OpenPGP keys (bug introduced with 2.0.8). [CVE-2008-1530]
- Minor bug fixes.
GnuPG 2.0.8 released (2007-12-20)
- Enhanced gpg-connect-agent with a small scripting language.
- New option –list-config for gpgconf.
- Fixed a crash in gpgconf.
- Gpg-agent now supports the passphrase quality bar of the latest Pinentry.
- The envvars XAUTHORITY and PINENTRY_USER_DATA are now passed to the Pinentry.
- Fixed the auto creation of the key stub for smartcards.
- Fixed a rare bug in decryption using the OpenPGP card.
- Creating DSA2 keys is now possible.
- New option –extra-digest-algo for gpgsm to allow verification of broken signatures.
- Allow encryption with legacy Elgamal sign+encrypt keys with option –rfc2440.
- Windows is now a supported platform.
- Made sure that under Windows the file permissions of the socket are taken into account. This required a change of our socket emulation code and changed the IPC protocol under Windows.
GnuPG 2.0.7 released (2007-09-10)
- Fixed encryption problem if duplicate certificates are in the keybox.
- Made it work on Windows Vista. Note that the entire Windows port is still considered Beta.
- Add new options min-passphrase-nonalpha, check-passphrase-pattern, enforce-passphrase-constraints and max-passphrase-days to gpg-agent.
- Add command –check-components to gpgconf. Gpgconf now uses the installed versions of the programs and does not anymore search via PATH for them.
GnuPG 2.0.6 released (2007-08-16)
- GPGSM does now grok –default-key.
- GPGCONF is now aware of –default-key and –encrypt-to.
- GPGSM does again correctly print the serial number as well the the various keyids. This was broken since 2.0.4.
- New option –validation-model and support for the chain-model.
- Improved Windows support.
GnuPG 2.0.5 released (2007-07-05)
- Switched license to GPLv3.
- Basic support for Windows. Run "./autogen.sh –build-w32" to build it. As usual the mingw cross compiling toolchain is required.
- Fixed bug when using the –p12-charset without –armor.
- The command –gen-key may now be used instead of the gpgsm-gencert.sh script.
- Changed key generation to reveal less information about the machine. Bug fixes for gpg2's card key generation.
GnuPG 2.0.4 released (2007-05-09)
- The server mode key listing commands are now also working for systems without the funopen/fopencookie API.
- PKCS#12 import now tries several encodings in case the passphrase was not utf-8 encoded. New option –p12-charset for gpgsm.
- Improved the libgcrypt logging support in all modules.
GnuPG 2.0.3 released (2007-03-08)
- By default, do not allow processing multiple plaintexts in a single stream. Many programs that called GnuPG were assuming that GnuPG did not permit this, and were thus not using the plaintext boundary status tags that GnuPG provides. This change makes GnuPG reject such messages by default which makes those programs safe again. –allow-multiple-messages returns to the old behavior. [CVE-2007-1263].
- New –verify-option show-primary-uid-only.
- gpgconf may now reads a global configuration file to select which options are changeable by a frontend. The new applygnupgdefaults tool may be used by an admin to set default options for all users.
- The PIN pad of the Cherry XX44 keyboard is now supported. The DINSIG and the NKS applications are now also aware of PIN pads.
GnuPG 2.0.2 released (2007-01-31)
- Fixed a serious and exploitable bug in processing encrypted packages. [CVE-2006-6235].
- Added –passphrase-repeat to set the number of times GPG will prompt for a new passphrase to be repeated. This is useful to help memorize a new passphrase. The default is 1 repetition.
- Using a PIN pad does now also work for the signing key.
- A warning is displayed by gpg-agent if a new passphrase is too short. New option –min-passphrase-len defaults to 8.
- The status code BEGIN_SIGNING now shows the used hash algorithms.
GnuPG 2.0.1 released (2006-11-28)
- Experimental support for the PIN pads of the SPR 532 and the Kaan Advanced card readers. Add "disable-keypad" scdaemon.conf if you don't want it. Does currently only work for the OpenPGP card and its authentication and decrypt keys.
- Fixed build problems on some some platforms and crashes on amd64.
- Fixed a buffer overflow in gpg2. [bug#728,CVE-2006-6169]
GnuPG 2.0.0 released (2006-11-11)
- First stable version of a GnuPG integrating OpenPGP and S/MIME.
GnuPG 1.9.95 released (2006-11-06)
GnuPG 1.9.94 released (2006-10-24)
- Keys for gpgsm may now be specified using a keygrip. A keygrip is indicated by a prefixing it with an ampersand.
- gpgconf now supports switching the CMS cipher algo (e.g. to AES).
- New command –gpgconf-test for all major tools. This may be used to check whether the configuration file is sane.
GnuPG 1.9.93 released (2006-10-18)
- In –with-validation mode gpgsm will now also ask whether a root certificate should be trusted.
- Link to Pth only if really necessary.
- Fixed a pubring corruption bug in gpg2 occurring when importing signatures or keys with insane lengths.
- Fixed v3 keyID calculation bug in gpg2.
- More tweaks for certificates without extensions.
GnuPG 1.9.92 released (2006-10-11)
GnuPG 1.9.91 released (2006-10-04)
- New "relax" flag for trustlist.txt to allow root CA certificates without BasicContraints.
- [gpg2] Removed the -k PGP 2 compatibility hack. -k is now an alias for –list-keys.
- [gpg2] Print a warning if "-sat" is used instead of "–clearsign".
GnuPG 1.9.90 released (2006-09-25)
- Made readline work for gpg.
- Cleanups und minor bug fixes.
- Included translations from gnupg 1.4.5.
GnuPG 1.9.23 released (2006-09-18)
- Regular man pages for most tools are now build directly from the Texinfo source.
- The gpg code from 1.4.5 has been fully merged into this release. The configure option –enable-gpg is still required to build this gpg part. For production use of OpenPGP the gpg version 1.4.5 is still recommended. Note, that gpg will be installed under the name gpg2 to allow coexisting with an 1.4.x gpg.
- API change in gpg-agent's pkdecrypt command. Thus an older gpgsm may not be used with the current gpg-agent.
- The scdaemon will now call a script on reader status changes.
- gpgsm now allows file descriptor passing for "INPUT", "OUTPUT" and "MESSAGE".
- The gpgsm server may now output a key listing to the output file handle. This needs to be enabled using "OPTION list-to-output=1".
- The –output option of gpgsm has now an effect on list-keys.
- New gpgsm commands –dump-chain and list-chain.
- gpg-connect-agent has new options to utilize descriptor passing.
- A global trustlist may now be used. See doc/examples/trustlist.txt.
- When creating a new pubring.kbx keybox common certificates are imported.
GnuPG 1.9.22 released (2006-07-27)
- Enhanced pkcs#12 support to allow import from simple keyBags.
- Exporting to pkcs#12 now create bag attributes so that Mozilla is able to import the files.
- Fixed uploading of certain keys to the smart card.
GnuPG 1.9.21 released (2006-06-20)
- New command APDU for scdaemon to allow using it for general card access. Might be used through gpg-connect-agent by using the SCD prefix command.
- Support for the CardMan 4040 PCMCIA reader (Linux 2.6.15 required).
- Scdaemon does not anymore reset cards at the end of a connection.
- Kludge to allow use of Bundesnetzagentur issued X.509 certificates.
- Added –hash=xxx option to scdaemon's PKSIGN command.
- Pkcs#12 files are now created with a MAC. This is for better interoperability.
- Collected bug fixes and minor other changes.
GnuPG 1.9.20 released (2005-12-20)
- Importing pkcs#12 files created be recent versions of Mozilla works again.
- Basic support for qualified signatures.
- New debug tool gpgparsemail.
GnuPG 1.9.19 released (2005-09-12)
- The Belgian eID card is now supported for signatures and ssh. Other pkcs#15 cards should work as well.
- Fixed bug in –export-secret-key-p12 so that certificates are again included.
GnuPG 1.9.18 released (2005-08-01)
- [gpgsm] Now allows for more than one email address as well as URIs and dnsNames in certificate request generation. A keygrip may be given to create a request from an existing key.
- A couple of minor bug fixes.
GnuPG 1.9.17 released (2005-06-20)
- gpg-connect-agent has now features to handle Assuan INQUIRE commands.
- Internal changes for OpenPGP cards. New Assuan command WRITEKEY.
- GNU Pth is now a hard requirement.
- [scdaemon] Support for OpenSC has been removed. Instead a new and straightforward pkcs#15 modules has been written. As of now it does allows only signing using TCOS cards but we are going to enhance it to match all the old capabilities.
- [gpg-agent] New option –write-env-file and Assuan command UPDATESTARTUPTTY.
- [gpg-agent] New option –default-cache-ttl-ssh to set the TTL for SSH passphrase caching independent from the other passphrases.
GnuPG 1.9.16 released (2005-04-21)
- gpg-agent does now support the ssh-agent protocol and thus allows to use the pinentry as well as the OpenPGP smartcard with ssh.
- New tool gpg-connect-agent as a general client for the gpg-agent.
- New tool symcryptrun as a wrapper for certain encryption tools.
- The gpg tool is not anymore build by default because those gpg versions available in the gnupg 1.4 series are far more matured.
GnuPG 1.9.15 released (2005-01-13)
- Fixed passphrase caching bug.
- Better support for CCID readers; the reader from Cherry RS 6700 USB does now work.
GnuPG 1.9.14 released (2004-12-22)
- [gpg-agent] New option –use-standard-socket to allow the use of a fixed socket. gpgsm falls back to this socket if GPG_AGENT_INFO has not been set.
- Ported to MS Windows with some functional limitations.
- New tool gpg-preset-passphrase.
GnuPG 1.9.13 released (2004-12-03)
- [gpgsm] New option –prefer-system-dirmngr.
- Minor cleanups and debugging aids.
GnuPG 1.9.12 released (2004-10-22)
- [scdaemon] Partly rewrote the PC/SC code.
- Removed the sc-investigate tool. It is now in a separate package available at ftp://ftp.g10code.com/g10code/gscutils/ .
- [gpg-agent] Fixed logging problem.
GnuPG 1.9.11 released (2004-10-01)
- When using –import along with –with-validation, the imported certificates are validated and only imported if they are fully valid.
- [gpg-agent] New option –max-cache-ttl.
- [gpg-agent] When used without –daemon or –server, gpg-agent now check whether a agent is already running and usable.
- Fixed some i18n problems.
GnuPG 1.9.10 released (2004-07-22)
- Fixed a serious bug in the checking of trusted root certificates.
- New configure option –enable-agent-pnly allows to build and install just the agent.
- Fixed a problem with the log file handling.
GnuPG 1.9.9 released (2004-06-08)
- [gpg-agent] The new option –allow-mark-trusted is now required to allow gpg-agent to add a key to the trustlist.txt after user confirmation.
- Creating PKCS#10 requests does now honor the key usage.
GnuPG 1.9.8 released (2004-04-29)
- [scdaemon] Overhauled the internal CCID driver.
- [scdaemon] Status files named ~/.gnupg/reader_<n>.status are now written when using the internal CCID driver.
- [gpgsm] New commands –dump-{,secret,external}-keys to show a very detailed view of the certificates.
- The keybox gets now compressed after 3 hours and ephemeral stored certificates are deleted after about a day.
- [gpg] Usability fixes for –card-edit. Note, that this has already been ported back to gnupg-1.3
GnuPG 1.9.7 released (2004-04-06)
- Instrumented the modules for gpgconf.
- Added support for DINSIG card applications.
- Include the smimeCapabilities attribute with signed messages.
- Now uses the gettext domain "gnupg2" to avoid conflicts with gnupg versions < 1.9.
GnuPG 1.9.6 released (2004-03-06)
- Code cleanups and bug fixes.
GnuPG 1.9.5 released (2004-02-21)
- gpg-protect-tool gets now installed into libexec as it ought to be. Cleaned up the build system to better comply with the coding standards.
- [gpgsm] The –import command is now able to autodetect pkcs#12 files and import secret and private keys from this file format. A new command –export-secret-key-p12 is provided to allow exporting of secret keys in PKCS\#12 format.
- [gpgsm] The pinentry will now present a description of the key for whom the passphrase is requested.
- [gpgsm] New option –with-validation to check the validity of key while listing it.
- New option –debug-level={none,basic,advanced,expert,guru} to map the debug flags to sensitive levels on a per program base.
GnuPG 1.9.4 released (2004-01-30)
- Added support for the Telesec NKS 2.0 card application.
- Added simple tool addgnupghome to create .gnupg directories from etc/skel.gnupg.
- Various minor bug fixes and cleanups; mainly gpgsm and gpg-agent related.
GnuPG 1.9.3 released (2003-12-23)
- New gpgsm options –{enable,disable}-ocsp to validate keys using OCSP. This option requires a not yet released DirMngr version. Default is disabled.
- The –log-file option may now be used to print logs to a socket. Prefix the socket name with "socket://" to enable this. This does not work on all systems and falls back to stderr if there is a problem with the socket.
- The options –encrypt-to and –no-encrypt-to now work the same in gpgsm as in gpg. Note, they are also used in server mode.
- Duplicated recipients are now silently removed in gpgsm.
GnuPG 1.9.2 released (2003-11-17)
- On card key generation is no longer done using the –gen-key command but from the menu provided by the new –card-edit command.
- PINs are now properly cached and there are only 2 PINs visible. The 3rd PIN (CHV2) is internally syncronized with the regular PIN.
- All kind of other internal stuff.
GnuPG 1.9.1 released (2003-09-06)
- Support for OpenSC is back. scdaemon supports a –disable-opensc to disable OpenSC use at runtime, so that PC/SC or ct-API can still be used directly.
- Rudimentary support for the SCR335 smartcard reader using an internal driver. Requires current libusb from CVS.
- Bug fixes.
GnuPG 1.9.0 released (2003-08-05)
- gpg has been renamed to gpg2 and gpgv to gpgv2. This is a temporary change to allow co-existing with stable gpg versions.
- ~/.gnupg/gpg.conf-1.9.0 is fist tried as config file before the usual gpg.conf.
- Removed the -k, -kv and -kvv commands. -k is now an alias to –list-keys. New command -K as alias for –list-secret-keys.
- Removed –run-as-shm-coprocess feature.
- gpg does now also use libgcrypt, libgpg-error is required.
- New gpgsm commands –call-dirmngr and –call-protect-tool.
- Changing a passphrase is now possible using "gpgsm –passwd"
- The content-type attribute is now recognized and created.
- The agent does now reread certain options on receiving a HUP.
- The pinentry is now forked for each request so that clients with different environments are supported. When running in daemon mode and –keep-display is not used the DISPLAY variable is ignored.
- Merged stuff from the newpg branch and started this new development branch.
GnuPG 1.4.19 released (2015-02-27)
GnuPG 1.4.18 released (2014-06-30)
GnuPG 1.4.17 released (2014-06-23)
GnuPG 1.4.16 released (2013-12-18)
GnuPG 1.4.15 released (2013-10-04)
GnuPG 1.4.14 released (2013-07-25)
GnuPG 1.4.13 released (2012-12-20)
GnuPG 1.4.12 released (2012-01-30)
GnuPG 1.4.11 released (2010-10-18)
GnuPG 1.4.10 released (2009-09-02)
GnuPG 1.4.9 released (2008-03-26)
GnuPG 1.4.8 released (2007-12-20)
GnuPG 1.4.7 released (2007-03-05)
GnuPG 1.4.6 released (2006-12-06)
GnuPG 1.4.5 released (2006-08-01)
GnuPG 1.4.4 released (2006-06-25)
GnuPG 1.4.3 released (2006-04-03)
GnuPG 1.4.2 released (2005-07-26)
GnuPG 1.4.1 released (2005-03-15)
GnuPG 1.4.0 released (2004-12-16)
GnuPG 1.3.2 released (2003-05-27)
- New "–gnupg" option (set by default) that disables –openpgp, and the various –pgpX emulation options. This replaces –no-openpgp, and –no-pgpX, and also means that GnuPG has finally grown a –gnupg option to make GnuPG act like GnuPG.
- A bug in key validation has been fixed. This bug only affects keys with more than one user ID (photo IDs do not count here), and results in all user IDs on a given key being treated with the validity of the most-valid user ID on that key.
- Notation names that do not contain a '@' are no longer allowed unless –expert is set. This is to help prevent pollution of the (as yet unused) IETF notation namespace.
- Multiple trust models are now supported via the –trust-model option. The options are "pgp" (web-of-trust plus trust signatures), "classic" (web-of-trust only), and "always" (identical to the –always-trust option).
- The –personal-{cipher|digest|compression}-preferences are now consulted to get default algorithms before resorting to the last-ditch defaults of –s2k-cipher-algo, SHA1, and ZIP respectively. This allows a user to set algorithms to use in a safe manner so they are used when legal to do so, without forcing them on for all messages.
- New –primary-keyring option to designate the keyring that the user wants new keys imported into.
- –s2k-digest-algo is now used for all password mangling. Earlier versions used both –s2k-digest-algo and –digest-algo for passphrase mangling.
- Handling of –hidden-recipient or –throw-keyid messages is now easier - the user only needs to give their passphrase once, and GnuPG will try it against all of the available secret keys.
- Care is taken to prevent compiler optimization from removing memory wiping code.
- New option –no-mangle-dos-filenames so that filenames are not truncated in the W32 version.
- A "convert-from-106" script has been added. This is a simple script that automates the conversion from a 1.0.6 or earlier version of GnuPG to a 1.0.7 or later version.
- Disabled keys are now skipped when selecting keys for encryption. If you are using the –with-colons key listings to detect disabled keys, please see doc/DETAILS for a minor format change in this release.
- Minor trustdb changes to make the trust calculations match common usage.
- New command "revuid" in the –edit-key menu to revoke a user ID. This is a simpler interface to the old method (which still works) of revoking the user ID self-signature.
- Status VALIDSIG does now also print the primary key's fingerprint, as well as the signature version, pubkey algorithm, hash algorithm, and signature class.
- Add read-only support for the SHA-256 hash, and optional read-only support for the SHA-384 and SHA-512 hashes.
- New option –enable-progress-filter for use with frontends.
- DNS SRV records are used in HKP keyserver lookups to allow administrators to load balance and select keyserver ports automatically. This is as specified in draft-shaw-openpgp-hkp-00.txt.
- When using the "keyid!" syntax during a key export, only that specified key is exported. If the key in question is a subkey, the primary key plus only that subkey is exported.
- configure –disable-xxx options to disable individual algorithms at build time. This can be used to build a smaller gpg binary for embedded uses where space is tight. See the README file for the algorithms that can be used with this option, or use –enable-minimal to build the smallest gpg possible (disables all optional algorithms, disables keyserver access, and disables photo IDs).
- The keyserver no-modify flag on a key can now be displayed and modified.
- Note that the TIGER/192 digest algorithm is in the process of being dropped from the OpenPGP standard. While this release of GnuPG still contains it, it is disabled by default. To ensure you will still be able to use your messages with future versions of GnuPG and other OpenPGP programs, please do not use this algorithm.
GnuPG 1.3.1 released (2002-11-12)
- Trust signature support. This is based on the Maurer trust model where a user can specify the trust level along with the signature with multiple levels so users can delegate certification ability to other users, possibly restricted by a regular expression on the user ID. Note that full trust signature support requires a regular expression parsing library. The regexp code from glibc 2.3.1 is included for those platforms that don't have working regexp functions available. The configure option –disable-regex may be used to disable any regular expression code, which will make GnuPG ignore any trust signature with a regular expression included.
- Two new commands –hidden-recipient (-R) and –hidden-encrypt-to encrypt to a user, but hide the identity of that user. This is the same functionality as –throw-keyid, but can be used on a per-user basis.
- Full algorithm names (e.g. "3DES", "SHA1", "ZIP") can now be used interchangeably with the short algorithm names (e.g. "S2", "H2", "Z1") anywhere algorithm names are used in GnuPG.
GnuPG 1.3.0 released (2002-10-18)
- The last piece of internal keyserver support has been removed, and now all keyserver access is done via the keyserver plugins. There is also a newer keyserver protocol used between GnuPG and the plugins, so plugins from earlier versions of GnuPG may not work properly.
- The HKP keyserver plugin supports the new machine-readable key listing format for those keyservers that provide it.
- When using a HKP keyserver with multiple DNS records (such as wwwkeys.pgp.net which has the addresses of multiple servers around the world), try all records until one succeeds. Note that it depends on the LDAP library used whether the LDAP keyserver plugin does this as well.
- The library dependencies for OpenLDAP seem to change fairly frequently, and GnuPG's configure script cannot guess all the combinations. Use ./configure LDAPLIBS="-L libdir -l libs" to override the script and use the libraries selected.
- Secret keys generated with –export-secret-subkeys are now indicated in key listings with a '#' after the "sec", and in –with-colons listings by showing no capabilities (no lowercase characters).
- –trusted-key has been un-obsoleted, as it is useful for adding ultimately trusted keys from the config file. It is identical to using –edit and "trust" to change a key to ultimately trusted.
- Translations other than de are no longer distributed with the development branch. This is due to the frequent text changes during development, which cause the translations to rapidly go out of date.
GnuPG 1.2.8 released (2006-12-07)
GnuPG 1.2.7 released (2004-12-27
Источник: [https://torrent-igruha.org/3551-portal.html]Surprising Patterns in the Square Numbers (1, 4, 9, 16…)
A quick puzzle for you — look at the first few square numbers:
And now find the difference between consecutive squares:
1 to 4 = 3 4 to 9 = 5 9 to 16 = 7 16 to 25 = 9 25 to 36 = 11 …Huh? The odd numbers are sandwiched between the squares?
Strange, but true. Take some time to figure out why — even better, find a reason that would work on a nine-year-old. Go on, I’ll be here.
Exploring Patterns
We can explain this pattern in a few ways. But the goal is to find a convincing explanation, where we slap our forehands with “ah, that’s why!”. Let’s jump into three explanations, starting with the most intuitive, and see how they help explain the others.
Geometer’s Delight
It’s easy to forget that square numbers are, well… square! Try drawing them with pebbles
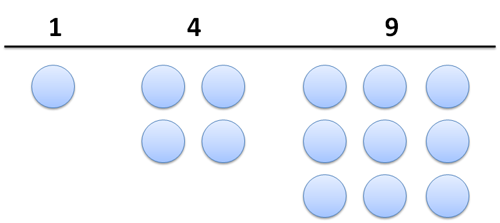
Notice anything? How do we get from one square number to the next? Well, we pull out each side (right and bottom) and fill in the corner:
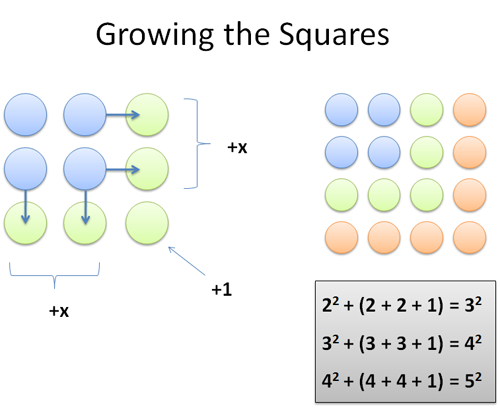
While at 4 (2×2), we can jump to 9 (3×3) with an extension: we add 2 (right) + 2 (bottom) + 1 (corner) = 5. And yep, 2×2 + 5 = 3×3. And when we’re at 3, we get to the next square by pulling out the sides and filling in the corner: Indeed, 3×3 + 3 + 3 + 1 = 16.
Each time, the change is 2 more than before, since we have another side in each direction (right and bottom).
Another neat property: the jump to the next square is always odd since we change by “2n + 1″ (2n must be even, so 2n + 1 is odd). Because the change is odd, it means the squares must cycle even, odd, even, odd…
And wait! That makes sense because the integers themselves cycle even, odd, even odd… after all, a square keeps the “evenness” of the root number (even * even = even, odd * odd = odd).
Funny how much insight is hiding inside a simple pattern. (I call this technique “geometry” but that’s probably not correct — it’s just visualizing numbers).
An Algebraist’s Epiphany
Drawing squares with pebbles? What is this, ancient Greece? No, the modern student might argue this:
- We have two consecutive numbers, n and (n+1)
- Their squares are n2 and (n+1)2
- The difference is (n+1)2 – n2 = (n2+ 2n + 1) – n2 = 2n + 1
For example, if n=2, then n2=4. And the difference to the next square is thus (2n + 1) = 5.
Indeed, we found the same geometric formula. But is an algebraic manipulation satisfying? To me, it’s a bit sterile and doesn’t have that same “aha!” forehead slap. But, it’s another tool, and when we combine it with the geometry the insight gets deeper.
Calculus Madness
Calculus students may think: “Dear fellows, we’re examining the curious sequence of the squares, f(x) = x^2. The derivative shall reveal the difference between successive elements”.
And deriving f(x) = x^2 we get:
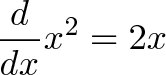
Close, but not quite! Where is the missing +1?
Let’s step back. Calculus explores smooth, continuous changes — not the “jumpy” sequence we’ve taken from 22 to 32 (how’d we skip from 2 to 3 without visiting 2.5 or 2.00001 first?).
But don’t lose hope. Calculus has algebraic roots, and the +1 is hidden. Let’s dust off the definition of the derivative:
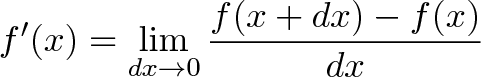
Forget about the limits for now — focus on what it means (the feeling, the love, the connection!). The derivative is telling us “compare the before and after, and divide by the change you put in”. If we compare the “before and after” for f(x) = x^2, and call our change “dx” we get:
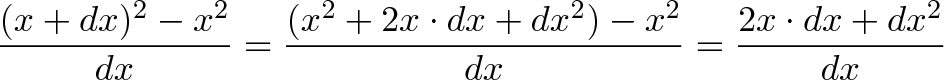
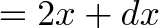
Now we’re getting somewhere. The derivative is deep, but focus on the big picture — it’s telling us the “bang for the buck” when we change our position from “x” to “x + dx”. For each unit of “dx” we go, our result will change by 2x + dx.
For example, if we pick a “dx” of 1 (like moving from 3 to 4), the derivative says “Ok, for every unit you go, the output changes by 2x + dx (2x + 1, in this case), where x is your original starting position and dx is the total amount you moved”. Let’s try it out:
Going from 32 to 42 would mean:
- x = 3, dx = 1
- change per unit input: 2x + dx = 6 + 1 = 7
- amount of change: dx = 1
- expected change: 7 * 1 = 7
- actual change: 42 – 32 = 16 – 9 = 7
We predicted a change of 7, and got a change of 7 — it worked! And we can change “dx” as much as we like. Let’s jump from 32 to 52:
- x = 3, dx = 2
- change per unit input: 2x + dx = 6 + 2 = 8
- number of changes: dx = 2
- total expected change: 8 * 2 = 16
- actual change: 52 – 32 = 25 – 9 = 16
Whoa! The equation worked (I was surprised too). Not only can we jump a boring “+1″ from 32 to 42, we could even go from 32 to 102 if we wanted!
Sure, we could have figured that out with algebra — but with our calculus hat, we started thinking about arbitrary amounts of change, not just +1. We took our rate and scaled it out, just like distance = rate * time (going 50mph doesn’t mean you can only travel for 1 hour, right? Why should 2x + dx only apply for one interval?).
My pedant-o-meter is buzzing, so remember the giant caveat: Calculus is about the micro scale. The derivative “wants” us to explore changes that happen over tiny intervals (we went from 3 to 4 without visiting 3.000000001 first!). But don’t be bullied — we got the idea of exploring an arbitrary interval “dx”, and dagnabbit, we ran with it. We’ll save tiny increments for another day.
Lessons Learned
Exploring the squares gave me several insights:
- Seemingly simple patterns (1, 4, 9, 16…) can be examined with several tools, to get new insights for each. I had completely forgotten that the ideas behind calculus (x going to x + dx) could help investigate discrete sequences.
- It’s all too easy to sandbox a mathematical tool, like geometry, and think it can’t shed light into higher levels (the geometric pictures really help the algebra, especially the +1, pop). Even with calculus, we’re used to relegating it to tiny changes — why not let dx stay large?
- Analogies work on multiple levels. It’s clear that the squares and the odds are intertwined — starting with one set, you can figure out the other. Calculus expands this relationship, letting us jump back and forth between the integral and derivative.
As we learn new techniques, don’t forget to apply them to the lessons of old. Happy math.
Appendix: The Cubes!
I can’t help myself: we studied the squares, now how about the cubes?
1, 8, 27, 64…
How do they change? Imagine growing a cube (made of pebbles!) to a larger and larger size — how does the volume change?
Join Over 450k Monthly Readers
Enjoy the article? There's plenty more to help you build a lasting, intuitive understanding of math. Join the newsletter for bonus content and the latest updates.
Other Posts In This Series
- Techniques for Adding the Numbers 1 to 100
- Rethinking Arithmetic: A Visual Guide
- Quick Insight: Intuitive Meaning of Division
- Quick Insight: Subtracting Negative Numbers
- Surprising Patterns in the Square Numbers (1, 4, 9, 16…)
- Fun With Modular Arithmetic
- Learning How to Count (Avoiding The Fencepost Problem)
- A Quirky Introduction To Number Systems
- Another Look at Prime Numbers
- Intuition For The Golden Ratio
- Different Interpretations for the Number Zero
What’s New in the Just Checking v2.16 by MaTHieU serial key or number?
Screen Shot

System Requirements for Just Checking v2.16 by MaTHieU serial key or number
- First, download the Just Checking v2.16 by MaTHieU serial key or number
-
You can download its setup from given links:


