
Code Red HTML Editor v1.3.4 serial key or number

Code Red HTML Editor v1.3.4 serial key or number
PROPOSED STANDARD
Errata Exist
Internet Engineering Task Force (IETF) E. Rescorla Request for Comments: 8446 Mozilla Obsoletes: 5077, 5246, 6961 August 2018 Updates: 5705, 6066 Category: Standards Track ISSN: 2070-1721 The Transport Layer Security (TLS) Protocol Version 1.3 Abstract This document specifies version 1.3 of the Transport Layer Security (TLS) protocol. TLS allows client/server applications to communicate over the Internet in a way that is designed to prevent eavesdropping, tampering, and message forgery. This document updates RFCs 5705 and 6066, and obsoletes RFCs 5077, 5246, and 6961. This document also specifies new requirements for TLS 1.2 implementations. Status of This Memo This is an Internet Standards Track document. This document is a product of the Internet Engineering Task Force (IETF). It represents the consensus of the IETF community. It has received public review and has been approved for publication by the Internet Engineering Steering Group (IESG). Further information on Internet Standards is available in Section 2 of RFC 7841. Information about the current status of this document, any errata, and how to provide feedback on it may be obtained at https://www.rfc-editor.org/info/rfc8446. Rescorla Standards Track [Page 1]
RFC 8446 TLS August 2018 Copyright Notice Copyright (c) 2018 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust's Legal Provisions Relating to IETF Documents (https://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents carefully, as they describe your rights and restrictions with respect to this document. Code Components extracted from this document must include Simplified BSD License text as described in Section 4.e of the Trust Legal Provisions and are provided without warranty as described in the Simplified BSD License. This document may contain material from IETF Documents or IETF Contributions published or made publicly available before November 10, 2008. The person(s) controlling the copyright in some of this material may not have granted the IETF Trust the right to allow modifications of such material outside the IETF Standards Process. Without obtaining an adequate license from the person(s) controlling the copyright in such materials, this document may not be modified outside the IETF Standards Process, and derivative works of it may not be created outside the IETF Standards Process, except to format it for publication as an RFC or to translate it into languages other than English. Rescorla Standards Track [Page 2]
RFC 8446 TLS August 2018 Table of Contents 1. Introduction ....................................................61.1. Conventions and Terminology ................................71.2. Major Differences from TLS 1.2 .............................81.3. Updates Affecting TLS 1.2 ..................................92. Protocol Overview ..............................................102.1. Incorrect DHE Share .......................................142.2. Resumption and Pre-Shared Key (PSK) .......................152.3. 0-RTT Data ................................................173. Presentation Language ..........................................193.1. Basic Block Size ..........................................193.2. Miscellaneous .............................................203.3. Numbers ...................................................203.4. Vectors ...................................................203.5. Enumerateds ...............................................213.6. Constructed Types .........................................223.7. Constants .................................................233.8. Variants ..................................................234. Handshake Protocol .............................................244.1. Key Exchange Messages .....................................254.1.1. Cryptographic Negotiation ..........................264.1.2. Client Hello .......................................274.1.3. Server Hello .......................................314.1.4. Hello Retry Request ................................334.2. Extensions ................................................354.2.1. Supported Versions .................................394.2.2. Cookie .............................................404.2.3. Signature Algorithms ...............................414.2.4. Certificate Authorities ............................454.2.5. OID Filters ........................................454.2.6. Post-Handshake Client Authentication ...............474.2.7. Supported Groups ...................................474.2.8. Key Share ..........................................484.2.9. Pre-Shared Key Exchange Modes ......................514.2.10. Early Data Indication .............................524.2.11. Pre-Shared Key Extension ..........................554.3. Server Parameters .........................................594.3.1. Encrypted Extensions ...............................604.3.2. Certificate Request ................................604.4. Authentication Messages ...................................614.4.1. The Transcript Hash ................................634.4.2. Certificate ........................................644.4.3. Certificate Verify .................................694.4.4. Finished ...........................................714.5. End of Early Data .........................................72Rescorla Standards Track [Page 3]
RFC 8446 TLS August 20184.6. Post-Handshake Messages ...................................734.6.1. New Session Ticket Message .........................734.6.2. Post-Handshake Authentication ......................754.6.3. Key and Initialization Vector Update ...............765. Record Protocol ................................................775.1. Record Layer ..............................................785.2. Record Payload Protection .................................805.3. Per-Record Nonce ..........................................825.4. Record Padding ............................................835.5. Limits on Key Usage .......................................846. Alert Protocol .................................................856.1. Closure Alerts ............................................876.2. Error Alerts ..............................................887. Cryptographic Computations .....................................907.1. Key Schedule ..............................................917.2. Updating Traffic Secrets ..................................947.3. Traffic Key Calculation ...................................957.4. (EC)DHE Shared Secret Calculation .........................957.4.1. Finite Field Diffie-Hellman ........................957.4.2. Elliptic Curve Diffie-Hellman ......................967.5. Exporters .................................................978. 0-RTT and Anti-Replay ..........................................988.1. Single-Use Tickets ........................................998.2. Client Hello Recording ....................................998.3. Freshness Checks .........................................1019. Compliance Requirements .......................................1029.1. Mandatory-to-Implement Cipher Suites .....................1029.2. Mandatory-to-Implement Extensions ........................1039.3. Protocol Invariants ......................................10410. Security Considerations ......................................10611. IANA Considerations ..........................................10612. References ...................................................10912.1. Normative References ....................................10912.2. Informative References ..................................112Appendix A. State Machine ........................................120A.1. Client ....................................................120A.2. Server ....................................................121Appendix B. Protocol Data Structures and Constant Values .........122B.1. Record Layer ..............................................122B.2. Alert Messages ............................................123B.3. Handshake Protocol ........................................124B.3.1. Key Exchange Messages .................................125B.3.2. Server Parameters Messages ............................131B.3.3. Authentication Messages ...............................132B.3.4. Ticket Establishment ..................................132B.3.5. Updating Keys .........................................133B.4. Cipher Suites .............................................133Rescorla Standards Track [Page 4]
RFC 8446 TLS August 2018Appendix C. Implementation Notes .................................134C.1. Random Number Generation and Seeding ......................134C.2. Certificates and Authentication ...........................135C.3. Implementation Pitfalls ...................................135C.4. Client Tracking Prevention ................................137C.5. Unauthenticated Operation .................................137Appendix D. Backward Compatibility ...............................138D.1. Negotiating with an Older Server ..........................139D.2. Negotiating with an Older Client ..........................139D.3. 0-RTT Backward Compatibility ..............................140D.4. Middlebox Compatibility Mode ..............................140D.5. Security Restrictions Related to Backward Compatibility ...141Appendix E. Overview of Security Properties ......................142E.1. Handshake .................................................142E.1.1. Key Derivation and HKDF ...............................145E.1.2. Client Authentication .................................146E.1.3. 0-RTT .................................................146E.1.4. Exporter Independence .................................146E.1.5. Post-Compromise Security ..............................146E.1.6. External References ...................................147E.2. Record Layer ..............................................147E.2.1. External References ...................................148E.3. Traffic Analysis ..........................................148E.4. Side-Channel Attacks ......................................149E.5. Replay Attacks on 0-RTT ...................................150E.5.1. Replay and Exporters ..................................151E.6. PSK Identity Exposure .....................................152E.7. Sharing PSKs ..............................................152E.8. Attacks on Static RSA .....................................152 Contributors .....................................................153 Author's Address .................................................160Rescorla Standards Track [Page 5]
RFC 8446 TLS August 20181. Introduction The primary goal of TLS is to provide a secure channel between two communicating peers; the only requirement from the underlying transport is a reliable, in-order data stream. Specifically, the secure channel should provide the following properties: - Authentication: The server side of the channel is always authenticated; the client side is optionally authenticated. Authentication can happen via asymmetric cryptography (e.g., RSA [RSA], the Elliptic Curve Digital Signature Algorithm (ECDSA) [ECDSA], or the Edwards-Curve Digital Signature Algorithm (EdDSA) [RFC8032]) or a symmetric pre-shared key (PSK). - Confidentiality: Data sent over the channel after establishment is only visible to the endpoints. TLS does not hide the length of the data it transmits, though endpoints are able to pad TLS records in order to obscure lengths and improve protection against traffic analysis techniques. - Integrity: Data sent over the channel after establishment cannot be modified by attackers without detection. These properties should be true even in the face of an attacker who has complete control of the network, as described in [RFC3552]. See Appendix E for a more complete statement of the relevant security properties. TLS consists of two primary components: - A handshake protocol (Section 4) that authenticates the communicating parties, negotiates cryptographic modes and parameters, and establishes shared keying material. The handshake protocol is designed to resist tampering; an active attacker should not be able to force the peers to negotiate different parameters than they would if the connection were not under attack. - A record protocol (Section 5) that uses the parameters established by the handshake protocol to protect traffic between the communicating peers. The record protocol divides traffic up into a series of records, each of which is independently protected using the traffic keys. Rescorla Standards Track [Page 6]
RFC 8446 TLS August 2018 TLS is application protocol independent; higher-level protocols can layer on top of TLS transparently. The TLS standard, however, does not specify how protocols add security with TLS; how to initiate TLS handshaking and how to interpret the authentication certificates exchanged are left to the judgment of the designers and implementors of protocols that run on top of TLS. This document defines TLS version 1.3. While TLS 1.3 is not directly compatible with previous versions, all versions of TLS incorporate a versioning mechanism which allows clients and servers to interoperably negotiate a common version if one is supported by both peers. This document supersedes and obsoletes previous versions of TLS, including version 1.2 [RFC5246]. It also obsoletes the TLS ticket mechanism defined in [RFC5077] and replaces it with the mechanism defined in Section 2.2. Because TLS 1.3 changes the way keys are derived, it updates [RFC5705] as described in Section 7.5. It also changes how Online Certificate Status Protocol (OCSP) messages are carried and therefore updates [RFC6066] and obsoletes [RFC6961] as described in Section 4.4.2.1. 1.1. Conventions and Terminology The key words "MUST", "MUST NOT", "REQUIRED", "SHALL", "SHALL NOT", "SHOULD", "SHOULD NOT", "RECOMMENDED", "NOT RECOMMENDED", "MAY", and "OPTIONAL" in this document are to be interpreted as described in BCP 14 [RFC2119] [RFC8174] when, and only when, they appear in all capitals, as shown here. The following terms are used: client: The endpoint initiating the TLS connection. connection: A transport-layer connection between two endpoints. endpoint: Either the client or server of the connection. handshake: An initial negotiation between client and server that establishes the parameters of their subsequent interactions within TLS. peer: An endpoint. When discussing a particular endpoint, "peer" refers to the endpoint that is not the primary subject of discussion. Rescorla Standards Track [Page 7]
RFC 8446 TLS August 2018 receiver: An endpoint that is receiving records. sender: An endpoint that is transmitting records. server: The endpoint that did not initiate the TLS connection. 1.2. Major Differences from TLS 1.2 The following is a list of the major functional differences between TLS 1.2 and TLS 1.3. It is not intended to be exhaustive, and there are many minor differences. - The list of supported symmetric encryption algorithms has been pruned of all algorithms that are considered legacy. Those that remain are all Authenticated Encryption with Associated Data (AEAD) algorithms. The cipher suite concept has been changed to separate the authentication and key exchange mechanisms from the record protection algorithm (including secret key length) and a hash to be used with both the key derivation function and handshake message authentication code (MAC). - A zero round-trip time (0-RTT) mode was added, saving a round trip at connection setup for some application data, at the cost of certain security properties. - Static RSA and Diffie-Hellman cipher suites have been removed; all public-key based key exchange mechanisms now provide forward secrecy. - All handshake messages after the ServerHello are now encrypted. The newly introduced EncryptedExtensions message allows various extensions previously sent in the clear in the ServerHello to also enjoy confidentiality protection. - The key derivation functions have been redesigned. The new design allows easier analysis by cryptographers due to their improved key separation properties. The HMAC-based Extract-and-Expand Key Derivation Function (HKDF) is used as an underlying primitive. - The handshake state machine has been significantly restructured to be more consistent and to remove superfluous messages such as ChangeCipherSpec (except when needed for middlebox compatibility). - Elliptic curve algorithms are now in the base spec, and new signature algorithms, such as EdDSA, are included. TLS 1.3 removed point format negotiation in favor of a single point format for each curve. Rescorla Standards Track [Page 8]
RFC 8446 TLS August 2018 - Other cryptographic improvements were made, including changing the RSA padding to use the RSA Probabilistic Signature Scheme (RSASSA-PSS), and the removal of compression, the Digital Signature Algorithm (DSA), and custom Ephemeral Diffie-Hellman (DHE) groups. - The TLS 1.2 version negotiation mechanism has been deprecated in favor of a version list in an extension. This increases compatibility with existing servers that incorrectly implemented version negotiation. - Session resumption with and without server-side state as well as the PSK-based cipher suites of earlier TLS versions have been replaced by a single new PSK exchange. - References have been updated to point to the updated versions of RFCs, as appropriate (e.g., RFC 5280 rather than RFC 3280). 1.3. Updates Affecting TLS 1.2 This document defines several changes that optionally affect implementations of TLS 1.2, including those which do not also support TLS 1.3: - A version downgrade protection mechanism is described in Section 4.1.3. - RSASSA-PSS signature schemes are defined in Section 4.2.3. - The "supported_versions" ClientHello extension can be used to negotiate the version of TLS to use, in preference to the legacy_version field of the ClientHello. - The "signature_algorithms_cert" extension allows a client to indicate which signature algorithms it can validate in X.509 certificates. Additionally, this document clarifies some compliance requirements for earlier versions of TLS; see Section 9.3. Rescorla Standards Track [Page 9]
RFC 8446 TLS August 20182. Protocol Overview The cryptographic parameters used by the secure channel are produced by the TLS handshake protocol. This sub-protocol of TLS is used by the client and server when first communicating with each other. The handshake protocol allows peers to negotiate a protocol version, select cryptographic algorithms, optionally authenticate each other, and establish shared secret keying material. Once the handshake is complete, the peers use the established keys to protect the application-layer traffic. A failure of the handshake or other protocol error triggers the termination of the connection, optionally preceded by an alert message (Section 6). TLS supports three basic key exchange modes: - (EC)DHE (Diffie-Hellman over either finite fields or elliptic curves) - PSK-only - PSK with (EC)DHE Rescorla Standards Track [Page 10]
RFC 8446 TLS August 2018* Indicates optional or situation-dependent messages/extensions that are not always sent. {} Indicates messages protected using keys derived from a [sender]_handshake_traffic_secret. [] Indicates messages protected using keys derived from [sender]_application_traffic_secret_N. Figure 1: Message Flow for Full TLS Handshake The handshake can be thought of as having three phases (indicated in the diagram above): - Key Exchange: Establish shared keying material and select the cryptographic parameters. Everything after this phase is encrypted. - Server Parameters: Establish other handshake parameters (whether the client is authenticated, application-layer protocol support, etc.). Rescorla Standards Track [Page 11]
RFC 8446 TLS August 2018 - Authentication: Authenticate the server (and, optionally, the client) and provide key confirmation and handshake integrity. In the Key Exchange phase, the client sends the ClientHello (Section 4.1.2) message, which contains a random nonce (ClientHello.random); its offered protocol versions; a list of symmetric cipher/HKDF hash pairs; either a set of Diffie-Hellman key shares (in the "key_share" (Section 4.2.8) extension), a set of pre-shared key labels (in the "pre_shared_key" (Section 4.2.11) extension), or both; and potentially additional extensions. Additional fields and/or messages may also be present for middlebox compatibility. The server processes the ClientHello and determines the appropriate cryptographic parameters for the connection. It then responds with its own ServerHello (Section 4.1.3), which indicates the negotiated connection parameters. The combination of the ClientHello and the ServerHello determines the shared keys. If (EC)DHE key establishment is in use, then the ServerHello contains a "key_share" extension with the server's ephemeral Diffie-Hellman share; the server's share MUST be in the same group as one of the client's shares. If PSK key establishment is in use, then the ServerHello contains a "pre_shared_key" extension indicating which of the client's offered PSKs was selected. Note that implementations can use (EC)DHE and PSK together, in which case both extensions will be supplied. The server then sends two messages to establish the Server Parameters: EncryptedExtensions: responses to ClientHello extensions that are not required to determine the cryptographic parameters, other than those that are specific to individual certificates. [Section 4.3.1] CertificateRequest: if certificate-based client authentication is desired, the desired parameters for that certificate. This message is omitted if client authentication is not desired. [Section 4.3.2] Rescorla Standards Track [Page 12]
RFC 8446 TLS August 2018 Finally, the client and server exchange Authentication messages. TLS uses the same set of messages every time that certificate-based authentication is needed. (PSK-based authentication happens as a side effect of key exchange.) Specifically: Certificate: The certificate of the endpoint and any per-certificate extensions. This message is omitted by the server if not authenticating with a certificate and by the client if the server did not send CertificateRequest (thus indicating that the client should not authenticate with a certificate). Note that if raw public keys [RFC7250] or the cached information extension [RFC7924] are in use, then this message will not contain a certificate but rather some other value corresponding to the server's long-term key. [Section 4.4.2] CertificateVerify: A signature over the entire handshake using the private key corresponding to the public key in the Certificate message. This message is omitted if the endpoint is not authenticating via a certificate. [Section 4.4.3] Finished: A MAC (Message Authentication Code) over the entire handshake. This message provides key confirmation, binds the endpoint's identity to the exchanged keys, and in PSK mode also authenticates the handshake. [Section 4.4.4] Upon receiving the server's messages, the client responds with its Authentication messages, namely Certificate and CertificateVerify (if requested), and Finished. At this point, the handshake is complete, and the client and server derive the keying material required by the record layer to exchange application-layer data protected through authenticated encryption. Application Data MUST NOT be sent prior to sending the Finished message, except as specified in Section 2.3. Note that while the server may send Application Data prior to receiving the client's Authentication messages, any data sent at that point is, of course, being sent to an unauthenticated peer. Rescorla Standards Track [Page 13]
RFC 8446 TLS August 20182.1. Incorrect DHE Share If the client has not provided a sufficient "key_share" extension (e.g., it includes only DHE or ECDHE groups unacceptable to or unsupported by the server), the server corrects the mismatch with a HelloRetryRequest and the client needs to restart the handshake with an appropriate "key_share" extension, as shown in Figure 2. If no common cryptographic parameters can be negotiated, the server MUST abort the handshake with an appropriate alert. TLS also allows several optimized variants of the basic handshake, as described in the following sections. Rescorla Standards Track [Page 14]
RFC 8446 TLS August 20182.2. Resumption and Pre-Shared Key (PSK) Although TLS PSKs can be established out of band, PSKs can also be established in a previous connection and then used to establish a new connection ("session resumption" or "resuming" with a PSK). Once a handshake has completed, the server can send the client a PSK identity that corresponds to a unique key derived from the initial handshake (see Section 4.6.1). The client can then use that PSK identity in future handshakes to negotiate the use of the associated PSK. If the server accepts the PSK, then the security context of the new connection is cryptographically tied to the original connection and the key derived from the initial handshake is used to bootstrap the cryptographic state instead of a full handshake. In TLS 1.2 and below, this functionality was provided by "session IDs" and "session tickets" [RFC5077]. Both mechanisms are obsoleted in TLS 1.3. PSKs can be used with (EC)DHE key exchange in order to provide forward secrecy in combination with shared keys, or can be used alone, at the cost of losing forward secrecy for the application data. Rescorla Standards Track [Page 15]
RFC 8446 TLS August 2018When a client offers resumption via a PSK, it SHOULD also supply a "key_share" extension to the server to allow the server to decline resumption and fall back to a full handshake, if needed. The server responds with a "pre_shared_key" extension to negotiate the use of PSK key establishment and can (as shown here) respond with a "key_share" extension to do (EC)DHE key establishment, thus providing forward secrecy. Rescorla Standards Track [Page 16]
RFC 8446 TLS August 2018 When PSKs are provisioned out of band, the PSK identity and the KDF hash algorithm to be used with the PSK MUST also be provisioned. Note: When using an out-of-band provisioned pre-shared secret, a critical consideration is using sufficient entropy during the key generation, as discussed in [RFC4086]. Deriving a shared secret from a password or other low-entropy sources is not secure. A low-entropy secret, or password, is subject to dictionary attacks based on the PSK binder. The specified PSK authentication is not a strong password-based authenticated key exchange even when used with Diffie-Hellman key establishment. Specifically, it does not prevent an attacker that can observe the handshake from performing a brute-force attack on the password/pre-shared key. 2.3. 0-RTT Data When clients and servers share a PSK (either obtained externally or via a previous handshake), TLS 1.3 allows clients to send data on the first flight ("early data"). The client uses the PSK to authenticate the server and to encrypt the early data. As shown in Figure 4, the 0-RTT data is just added to the 1-RTT handshake in the first flight. The rest of the handshake uses the same messages as for a 1-RTT handshake with PSK resumption. Rescorla Standards Track [Page 17]
RFC 8446 TLS August 2018 Client Server ClientHello + early_data + key_share* + psk_key_exchange_modes + pre_shared_key (Application Data*) --------> ServerHello + pre_shared_key + key_share* {EncryptedExtensions} + early_data* {Finished} <-------- [Application Data*] (EndOfEarlyData) {Finished} --------> [Application Data] <-------> [Application Data] + Indicates noteworthy extensions sent in the previously noted message. * Indicates optional or situation-dependent messages/extensions that are not always sent. () Indicates messages protected using keys derived from a client_early_traffic_secret. {} Indicates messages protected using keys derived from a [sender]_handshake_traffic_secret. [] Indicates messages protected using keys derived from [sender]_application_traffic_secret_N. Figure 4: Message Flow for a 0-RTT Handshake Rescorla Standards Track [Page 18]
RFC 8446 TLS August 2018 IMPORTANT NOTE: The security properties for 0-RTT data are weaker than those for other kinds of TLS data. Specifically: 1. This data is not forward secret, as it is encrypted solely under keys derived using the offered PSK. 2. There are no guarantees of non-replay between connections. Protection against replay for ordinary TLS 1.3 1-RTT data is provided via the server's Random value, but 0-RTT data does not depend on the ServerHello and therefore has weaker guarantees. This is especially relevant if the data is authenticated either with TLS client authentication or inside the application protocol. The same warnings apply to any use of the early_exporter_master_secret. 0-RTT data cannot be duplicated within a connection (i.e., the server will not process the same data twice for the same connection), and an attacker will not be able to make 0-RTT data appear to be 1-RTT data (because it is protected with different keys). Appendix E.5 contains a description of potential attacks, and Section 8 describes mechanisms which the server can use to limit the impact of replay. 3. Presentation Language This document deals with the formatting of data in an external representation. The following very basic and somewhat casually defined presentation syntax will be used. 3.1. Basic Block Size The representation of all data items is explicitly specified. The basic data block size is one byte (i.e., 8 bits). Multiple-byte data items are concatenations of bytes, from left to right, from top to bottom. From the byte stream, a multi-byte item (a numeric in the following example) is formed (using C notation) by: value = (byte[0] << 8*(n-1)) | (byte[1] << 8*(n-2)) | ... | byte[n-1]; This byte ordering for multi-byte values is the commonplace network byte order or big-endian format. Rescorla Standards Track [Page 19]
RFC 8446 TLS August 20183.2. Miscellaneous Comments begin with "/*" and end with "*/". Optional components are denoted by enclosing them in "[[ ]]" (double brackets). Single-byte entities containing uninterpreted data are of type opaque. A type alias T' for an existing type T is defined by: T T'; 3.3. Numbers The basic numeric data type is an unsigned byte (uint8). All larger numeric data types are constructed from a fixed-length series of bytes concatenated as described in Section 3.1 and are also unsigned. The following numeric types are predefined. uint8 uint16[2]; uint8 uint24[3]; uint8 uint32[4]; uint8 uint64[8]; All values, here and elsewhere in the specification, are transmitted in network byte (big-endian) order; the uint32 represented by the hex bytes 01 02 03 04 is equivalent to the decimal value 16909060. 3.4. Vectors A vector (single-dimensioned array) is a stream of homogeneous data elements. The size of the vector may be specified at documentation time or left unspecified until runtime. In either case, the length declares the number of bytes, not the number of elements, in the vector. The syntax for specifying a new type, T', that is a fixed- length vector of type T is T T'[n]; Here, T' occupies n bytes in the data stream, where n is a multiple of the size of T. The length of the vector is not included in the encoded stream. Rescorla Standards Track [Page 20]
RFC 8446 TLS August 2018 In the following example, Datum is defined to be three consecutive bytes that the protocol does not interpret, while Data is three consecutive Datum, consuming a total of nine bytes. opaque Datum[3]; /* three uninterpreted bytes */ Datum Data[9]; /* three consecutive 3-byte vectors */ Variable-length vectors are defined by specifying a subrange of legal lengths, inclusively, using the notation <floor..ceiling>. When these are encoded, the actual length precedes the vector's contents in the byte stream. The length will be in the form of a number consuming as many bytes as required to hold the vector's specified maximum (ceiling) length. A variable-length vector with an actual length field of zero is referred to as an empty vector. T T'<floor..ceiling>; In the following example, "mandatory" is a vector that must contain between 300 and 400 bytes of type opaque. It can never be empty. The actual length field consumes two bytes, a uint16, which is sufficient to represent the value 400 (see Section 3.3). Similarly, "longer" can represent up to 800 bytes of data, or 400 uint16 elements, and it may be empty. Its encoding will include a two-byte actual length field prepended to the vector. The length of an encoded vector must be an exact multiple of the length of a single element (e.g., a 17-byte vector of uint16 would be illegal). opaque mandatory<300..400>; /* length field is two bytes, cannot be empty */ uint16 longer<0..800>; /* zero to 400 16-bit unsigned integers */ 3.5. Enumerateds An additional sparse data type, called "enum" or "enumerated", is available. Each definition is a different type. Only enumerateds of the same type may be assigned or compared. Every element of an enumerated must be assigned a value, as demonstrated in the following example. Since the elements of the enumerated are not ordered, they can be assigned any unique value, in any order. enum { e1(v1), e2(v2), ... , en(vn) [[, (n)]] } Te; Future extensions or additions to the protocol may define new values. Implementations need to be able to parse and ignore unknown values unless the definition of the field states otherwise. Rescorla Standards Track [Page 21]
RFC 8446 TLS August 2018 An enumerated occupies as much space in the byte stream as would its maximal defined ordinal value. The following definition would cause one byte to be used to carry fields of type Color. enum { red(3), blue(5), white(7) } Color; One may optionally specify a value without its associated tag to force the width definition without defining a superfluous element. In the following example, Taste will consume two bytes in the data stream but can only assume the values 1, 2, or 4 in the current version of the protocol. enum { sweet(1), sour(2), bitter(4), (32000) } Taste; The names of the elements of an enumeration are scoped within the defined type. In the first example, a fully qualified reference to the second element of the enumeration would be Color.blue. Such qualification is not required if the target of the assignment is well specified. Color color = Color.blue; /* overspecified, legal */ Color color = blue; /* correct, type implicit */ The names assigned to enumerateds do not need to be unique. The numerical value can describe a range over which the same name applies. The value includes the minimum and maximum inclusive values in that range, separated by two period characters. This is principally useful for reserving regions of the space. enum { sad(0), meh(1..254), happy(255) } Mood; 3.6. Constructed Types Structure types may be constructed from primitive types for convenience. Each specification declares a new, unique type. The syntax used for definitions is much like that of C. struct { T1 f1; T2 f2; ... Tn fn; } T; Fixed- and variable-length vector fields are allowed using the standard vector syntax. Structures V1 and V2 in the variants example (Section 3.8) demonstrate this. Rescorla Standards Track [Page 22]
RFC 8446 TLS August 2018 The fields within a structure may be qualified using the type's name, with a syntax much like that available for enumerateds. For example, T.f2 refers to the second field of the previous declaration. 3.7. Constants Fields and variables may be assigned a fixed value using "=", as in: struct { T1 f1 = 8; /* T.f1 must always be 8 */ T2 f2; } T; 3.8. Variants Defined structures may have variants based on some knowledge that is available within the environment. The selector must be an enumerated type that defines the possible variants the structure defines. Each arm of the select (below) specifies the type of that variant's field and an optional field label. The mechanism by which the variant is selected at runtime is not prescribed by the presentation language. struct { T1 f1; T2 f2; .... Tn fn; select (E) { case e1: Te1 [[fe1]]; case e2: Te2 [[fe2]]; .... case en: Ten [[fen]]; }; } Tv; Rescorla Standards Track [Page 23]
RFC 8446 TLS August 2018 For example: enum { apple(0), orange(1) } VariantTag; struct { uint16 number; opaque string<0..10>; /* variable length */ } V1; struct { uint32 number; opaque string[10]; /* fixed length */ } V2; struct { VariantTag type; select (VariantRecord.type) { case apple: V1; case orange: V2; }; } VariantRecord; 4. Handshake Protocol The handshake protocol is used to negotiate the security parameters of a connection. Handshake messages are supplied to the TLS record layer, where they are encapsulated within one or more TLSPlaintext or TLSCiphertext structures which are processed and transmitted as specified by the current active connection state. Rescorla Standards Track [Page 24]
RFC 8446 TLS August 2018 enum { client_hello(1), server_hello(2), new_session_ticket(4), end_of_early_data(5), encrypted_extensions(8), certificate(11), certificate_request(13), certificate_verify(15), finished(20), key_update(24), message_hash(254), (255) } HandshakeType; struct { HandshakeType msg_type; /* handshake type */ uint24 length; /* remaining bytes in message */ select (Handshake.msg_type) { case client_hello: ClientHello; case server_hello: ServerHello; case end_of_early_data: EndOfEarlyData; case encrypted_extensions: EncryptedExtensions; case certificate_request: CertificateRequest; case certificate: Certificate; case certificate_verify: CertificateVerify; case finished: Finished; case new_session_ticket: NewSessionTicket; case key_update: KeyUpdate; }; } Handshake; Protocol messages MUST be sent in the order defined in Section 4.4.1 and shown in the diagrams in Section 2. A peer which receives a handshake message in an unexpected order MUST abort the handshake with an "unexpected_message" alert. New handshake message types are assigned by IANA as described in Section 11. 4.1. Key Exchange Messages The key exchange messages are used to determine the security capabilities of the client and the server and to establish shared secrets, including the traffic keys used to protect the rest of the handshake and the data. Rescorla Standards Track [Page 25]
RFC 8446 TLS August 20184.1.1. Cryptographic Negotiation In TLS, the cryptographic negotiation proceeds by the client offering the following four sets of options in its ClientHello: - A list of cipher suites which indicates the AEAD algorithm/HKDF hash pairs which the client supports. - A "supported_groups" (Section 4.2.7) extension which indicates the (EC)DHE groups which the client supports and a "key_share" (Section 4.2.8) extension which contains (EC)DHE shares for some or all of these groups. - A "signature_algorithms" (Section 4.2.3) extension which indicates the signature algorithms which the client can accept. A "signature_algorithms_cert" extension (Section 4.2.3) may also be added to indicate certificate-specific signature algorithms. - A "pre_shared_key" (Section 4.2.11) extension which contains a list of symmetric key identities known to the client and a "psk_key_exchange_modes" (Section 4.2.9) extension which indicates the key exchange modes that may be used with PSKs. If the server does not select a PSK, then the first three of these options are entirely orthogonal: the server independently selects a cipher suite, an (EC)DHE group and key share for key establishment, and a signature algorithm/certificate pair to authenticate itself to the client. If there is no overlap between the received "supported_groups" and the groups supported by the server, then the server MUST abort the handshake with a "handshake_failure" or an "insufficient_security" alert. If the server selects a PSK, then it MUST also select a key establishment mode from the set indicated by the client's "psk_key_exchange_modes" extension (at present, PSK alone or with (EC)DHE). Note that if the PSK can be used without (EC)DHE, then non-overlap in the "supported_groups" parameters need not be fatal, as it is in the non-PSK case discussed in the previous paragraph. If the server selects an (EC)DHE group and the client did not offer a compatible "key_share" extension in the initial ClientHello, the server MUST respond with a HelloRetryRequest (Section 4.1.4) message. Rescorla Standards Track [Page 26]
RFC 8446 TLS August 2018 If the server successfully selects parameters and does not require a HelloRetryRequest, it indicates the selected parameters in the ServerHello as follows: - If PSK is being used, then the server will send a "pre_shared_key" extension indicating the selected key. - When (EC)DHE is in use, the server will also provide a "key_share" extension. If PSK is not being used, then (EC)DHE and certificate-based authentication are always used. - When authenticating via a certificate, the server will send the Certificate (Section 4.4.2) and CertificateVerify (Section 4.4.3) messages. In TLS 1.3 as defined by this document, either a PSK or a certificate is always used, but not both. Future documents may define how to use them together. If the server is unable to negotiate a supported set of parameters (i.e., there is no overlap between the client and server parameters), it MUST abort the handshake with either a "handshake_failure" or "insufficient_security" fatal alert (see Section 6). 4.1.2. Client Hello When a client first connects to a server, it is REQUIRED to send the ClientHello as its first TLS message. The client will also send a ClientHello when the server has responded to its ClientHello with a HelloRetryRequest. In that case, the client MUST send the same ClientHello without modification, except as follows: - If a "key_share" extension was supplied in the HelloRetryRequest, replacing the list of shares with a list containing a single KeyShareEntry from the indicated group. - Removing the "early_data" extension (Section 4.2.10) if one was present. Early data is not permitted after a HelloRetryRequest. - Including a "cookie" extension if one was provided in the HelloRetryRequest. Rescorla Standards Track [Page 27]
RFC 8446 TLS August 2018 - Updating the "pre_shared_key" extension if present by recomputing the "obfuscated_ticket_age" and binder values and (optionally) removing any PSKs which are incompatible with the server's indicated cipher suite. - Optionally adding, removing, or changing the length of the "padding" extension [RFC7685]. - Other modifications that may be allowed by an extension defined in the future and present in the HelloRetryRequest. Because TLS 1.3 forbids renegotiation, if a server has negotiated TLS 1.3 and receives a ClientHello at any other time, it MUST terminate the connection with an "unexpected_message" alert. If a server established a TLS connection with a previous version of TLS and receives a TLS 1.3 ClientHello in a renegotiation, it MUST retain the previous protocol version. In particular, it MUST NOT negotiate TLS 1.3. Structure of this message: uint16 ProtocolVersion; opaque Random[32]; uint8 CipherSuite[2]; /* Cryptographic suite selector */ struct { ProtocolVersion legacy_version = 0x0303; /* TLS v1.2 */ Random random; opaque legacy_session_id<0..32>; CipherSuite cipher_suites<2..2^16-2>; opaque legacy_compression_methods<1..2^8-1>; Extension extensions<8..2^16-1>; } ClientHello; Rescorla Standards Track [Page 28]
RFC 8446 TLS August 2018 legacy_version: In previous versions of TLS, this field was used for version negotiation and represented the highest version number supported by the client. Experience has shown that many servers do not properly implement version negotiation, leading to "version intolerance" in which the server rejects an otherwise acceptable ClientHello with a version number higher than it supports. In TLS 1.3, the client indicates its version preferences in the "supported_versions" extension (Section 4.2.1) and the legacy_version field MUST be set to 0x0303, which is the version number for TLS 1.2. TLS 1.3 ClientHellos are identified as having a legacy_version of 0x0303 and a supported_versions extension present with 0x0304 as the highest version indicated therein. (See Appendix D for details about backward compatibility.) random: 32 bytes generated by a secure random number generator. See Appendix C for additional information. legacy_session_id: Versions of TLS before TLS 1.3 supported a "session resumption" feature which has been merged with pre-shared keys in this version (see Section 2.2). A client which has a cached session ID set by a pre-TLS 1.3 server SHOULD set this field to that value. In compatibility mode (see Appendix D.4), this field MUST be non-empty, so a client not offering a pre-TLS 1.3 session MUST generate a new 32-byte value. This value need not be random but SHOULD be unpredictable to avoid implementations fixating on a specific value (also known as ossification). Otherwise, it MUST be set as a zero-length vector (i.e., a zero-valued single byte length field). cipher_suites: A list of the symmetric cipher options supported by the client, specifically the record protection algorithm (including secret key length) and a hash to be used with HKDF, in descending order of client preference. Values are defined in Appendix B.4. If the list contains cipher suites that the server does not recognize, support, or wish to use, the server MUST ignore those cipher suites and process the remaining ones as usual. If the client is attempting a PSK key establishment, it SHOULD advertise at least one cipher suite indicating a Hash associated with the PSK. Rescorla Standards Track [Page 29]
RFC 8446 TLS August 2018 legacy_compression_methods: Versions of TLS before 1.3 supported compression with the list of supported compression methods being sent in this field. For every TLS 1.3 ClientHello, this vector MUST contain exactly one byte, set to zero, which corresponds to the "null" compression method in prior versions of TLS. If a TLS 1.3 ClientHello is received with any other value in this field, the server MUST abort the handshake with an "illegal_parameter" alert. Note that TLS 1.3 servers might receive TLS 1.2 or prior ClientHellos which contain other compression methods and (if negotiating such a prior version) MUST follow the procedures for the appropriate prior version of TLS. extensions: Clients request extended functionality from servers by sending data in the extensions field. The actual "Extension" format is defined in Section 4.2. In TLS 1.3, the use of certain extensions is mandatory, as functionality has moved into extensions to preserve ClientHello compatibility with previous versions of TLS. Servers MUST ignore unrecognized extensions. All versions of TLS allow an extensions field to optionally follow the compression_methods field. TLS 1.3 ClientHello messages always contain extensions (minimally "supported_versions", otherwise, they will be interpreted as TLS 1.2 ClientHello messages). However, TLS 1.3 servers might receive ClientHello messages without an extensions field from prior versions of TLS. The presence of extensions can be detected by determining whether there are bytes following the compression_methods field at the end of the ClientHello. Note that this method of detecting optional data differs from the normal TLS method of having a variable-length field, but it is used for compatibility with TLS before extensions were defined. TLS 1.3 servers will need to perform this check first and only attempt to negotiate TLS 1.3 if the "supported_versions" extension is present. If negotiating a version of TLS prior to 1.3, a server MUST check that the message either contains no data after legacy_compression_methods or that it contains a valid extensions block with no data following. If not, then it MUST abort the handshake with a "decode_error" alert. In the event that a client requests additional functionality using extensions and this functionality is not supplied by the server, the client MAY abort the handshake. After sending the ClientHello message, the client waits for a ServerHello or HelloRetryRequest message. If early data is in use, the client may transmit early Application Data (Section 2.3) while waiting for the next handshake message. Rescorla Standards Track [Page 30]
RFC 8446 TLS August 20184.1.3. Server Hello The server will send this message in response to a ClientHello message to proceed with the handshake if it is able to negotiate an acceptable set of handshake parameters based on the ClientHello. Structure of this message: struct { ProtocolVersion legacy_version = 0x0303; /* TLS v1.2 */ Random random; opaque legacy_session_id_echo<0..32>; CipherSuite cipher_suite; uint8 legacy_compression_method = 0; Extension extensions<6..2^16-1>; } ServerHello; legacy_version: In previous versions of TLS, this field was used for version negotiation and represented the selected version number for the connection. Unfortunately, some middleboxes fail when presented with new values. In TLS 1.3, the TLS server indicates its version using the "supported_versions" extension (Section 4.2.1), and the legacy_version field MUST be set to 0x0303, which is the version number for TLS 1.2. (See Appendix D for details about backward compatibility.) random: 32 bytes generated by a secure random number generator. See Appendix C for additional information. The last 8 bytes MUST be overwritten as described below if negotiating TLS 1.2 or TLS 1.1, but the remaining bytes MUST be random. This structure is generated by the server and MUST be generated independently of the ClientHello.random. legacy_session_id_echo: The contents of the client's legacy_session_id field. Note that this field is echoed even if the client's value corresponded to a cached pre-TLS 1.3 session which the server has chosen not to resume. A client which receives a legacy_session_id_echo field that does not match what it sent in the ClientHello MUST abort the handshake with an "illegal_parameter" alert. cipher_suite: The single cipher suite selected by the server from the list in ClientHello.cipher_suites. A client which receives a cipher suite that was not offered MUST abort the handshake with an "illegal_parameter" alert. legacy_compression_method: A single byte which MUST have the value 0. Rescorla Standards Track [Page 31]
RFC 8446 TLS August 2018 extensions: A list of extensions. The ServerHello MUST only include extensions which are required to establish the cryptographic context and negotiate the protocol version. All TLS 1.3 ServerHello messages MUST contain the "supported_versions" extension. Current ServerHello messages additionally contain either the "pre_shared_key" extension or the "key_share" extension, or both (when using a PSK with (EC)DHE key establishment). Other extensions (see Section 4.2) are sent separately in the EncryptedExtensions message. For reasons of backward compatibility with middleboxes (see Appendix D.4), the HelloRetryRequest message uses the same structure as the ServerHello, but with Random set to the special value of the SHA-256 of "HelloRetryRequest": CF 21 AD 74 E5 9A 61 11 BE 1D 8C 02 1E 65 B8 91 C2 A2 11 16 7A BB 8C 5E 07 9E 09 E2 C8 A8 33 9C Upon receiving a message with type server_hello, implementations MUST first examine the Random value and, if it matches this value, process it as described in Section 4.1.4). TLS 1.3 has a downgrade protection mechanism embedded in the server's random value. TLS 1.3 servers which negotiate TLS 1.2 or below in response to a ClientHello MUST set the last 8 bytes of their Random value specially in their ServerHello. If negotiating TLS 1.2, TLS 1.3 servers MUST set the last 8 bytes of their Random value to the bytes: 44 4F 57 4E 47 52 44 01 If negotiating TLS 1.1 or below, TLS 1.3 servers MUST, and TLS 1.2 servers SHOULD, set the last 8 bytes of their ServerHello.Random value to the bytes: 44 4F 57 4E 47 52 44 00 TLS 1.3 clients receiving a ServerHello indicating TLS 1.2 or below MUST check that the last 8 bytes are not equal to either of these values. TLS 1.2 clients SHOULD also check that the last 8 bytes are not equal to the second value if the ServerHello indicates TLS 1.1 or below. If a match is found, the client MUST abort the handshake with an "illegal_parameter" alert. This mechanism provides limited protection against downgrade attacks over and above what is provided by the Finished exchange: because the ServerKeyExchange, a message present in TLS 1.2 and below, includes a signature over both random values, it is not possible for an active attacker to modify the Rescorla Standards Track [Page 32]
RFC 8446 TLS August 2018 random values without detection as long as ephemeral ciphers are used. It does not provide downgrade protection when static RSA is used. Note: This is a change from [RFC5246], so in practice many TLS 1.2 clients and servers will not behave as specified above. A legacy TLS client performing renegotiation with TLS 1.2 or prior and which receives a TLS 1.3 ServerHello during renegotiation MUST abort the handshake with a "protocol_version" alert. Note that renegotiation is not possible when TLS 1.3 has been negotiated. 4.1.4. Hello Retry Request The server will send this message in response to a ClientHello message if it is able to find an acceptable set of parameters but the ClientHello does not contain sufficient information to proceed with the handshake. As discussed in Section 4.1.3, the HelloRetryRequest has the same format as a ServerHello message, and the legacy_version, legacy_session_id_echo, cipher_suite, and legacy_compression_method fields have the same meaning. However, for convenience we discuss "HelloRetryRequest" throughout this document as if it were a distinct message. The server's extensions MUST contain "supported_versions". Additionally, it SHOULD contain the minimal set of extensions necessary for the client to generate a correct ClientHello pair. As with the ServerHello, a HelloRetryRequest MUST NOT contain any extensions that were not first offered by the client in its ClientHello, with the exception of optionally the "cookie" (see Section 4.2.2) extension. Upon receipt of a HelloRetryRequest, the client MUST check the legacy_version, legacy_session_id_echo, cipher_suite, and legacy_compression_method as specified in Section 4.1.3 and then process the extensions, starting with determining the version using "supported_versions". Clients MUST abort the handshake with an "illegal_parameter" alert if the HelloRetryRequest would not result in any change in the ClientHello. If a client receives a second HelloRetryRequest in the same connection (i.e., where the ClientHello was itself in response to a HelloRetryRequest), it MUST abort the handshake with an "unexpected_message" alert. Rescorla Standards Track [Page 33]
RFC 8446 TLS August 2018 Otherwise, the client MUST process all extensions in the HelloRetryRequest and send a second updated ClientHello. The HelloRetryRequest extensions defined in this specification are: - supported_versions (see Section 4.2.1) - cookie (see Section 4.2.2) - key_share (see Section 4.2.8) A client which receives a cipher suite that was not offered MUST abort the handshake. Servers MUST ensure that they negotiate the same cipher suite when receiving a conformant updated ClientHello (if the server selects the cipher suite as the first step in the negotiation, then this will happen automatically). Upon receiving the ServerHello, clients MUST check that the cipher suite supplied in the ServerHello is the same as that in the HelloRetryRequest and otherwise abort the handshake with an "illegal_parameter" alert. In addition, in its updated ClientHello, the client SHOULD NOT offer any pre-shared keys associated with a hash other than that of the selected cipher suite. This allows the client to avoid having to compute partial hash transcripts for multiple hashes in the second ClientHello. The value of selected_version in the HelloRetryRequest "supported_versions" extension MUST be retained in the ServerHello, and a client MUST abort the handshake with an "illegal_parameter" alert if the value changes. Rescorla Standards Track [Page 34]
RFC 8446 TLS August 20184.2. Extensions A number of TLS messages contain tag-length-value encoded extensions structures. struct { ExtensionType extension_type; opaque extension_data<0..2^16-1>; } Extension; enum { server_name(0), /* RFC 6066 */ max_fragment_length(1), /* RFC 6066 */ status_request(5), /* RFC 6066 */ supported_groups(10), /* RFC 8422, 7919 */ signature_algorithms(13), /* RFC 8446 */ use_srtp(14), /* RFC 5764 */ heartbeat(15), /* RFC 6520 */ application_layer_protocol_negotiation(16), /* RFC 7301 */ signed_certificate_timestamp(18), /* RFC 6962 */ client_certificate_type(19), /* RFC 7250 */ server_certificate_type(20), /* RFC 7250 */ padding(21), /* RFC 7685 */ pre_shared_key(41), /* RFC 8446 */ early_data(42), /* RFC 8446 */ supported_versions(43), /* RFC 8446 */ cookie(44), /* RFC 8446 */ psk_key_exchange_modes(45), /* RFC 8446 */ certificate_authorities(47), /* RFC 8446 */ oid_filters(48), /* RFC 8446 */ post_handshake_auth(49), /* RFC 8446 */ signature_algorithms_cert(50), /* RFC 8446 */ key_share(51), /* RFC 8446 */ (65535) } ExtensionType; Rescorla Standards Track [Page 35]
RFC 8446 TLS August 2018 Here: - "extension_type" identifies the particular extension type. - "extension_data" contains information specific to the particular extension type. The list of extension types is maintained by IANA as described in Section 11. Extensions are generally structured in a request/response fashion, though some extensions are just indications with no corresponding response. The client sends its extension requests in the ClientHello message, and the server sends its extension responses in the ServerHello, EncryptedExtensions, HelloRetryRequest, and Certificate messages. The server sends extension requests in the CertificateRequest message which a client MAY respond to with a Certificate message. The server MAY also send unsolicited extensions in the NewSessionTicket, though the client does not respond directly to these. Implementations MUST NOT send extension responses if the remote endpoint did not send the corresponding extension requests, with the exception of the "cookie" extension in the HelloRetryRequest. Upon receiving such an extension, an endpoint MUST abort the handshake with an "unsupported_extension" alert. The table below indicates the messages where a given extension may appear, using the following notation: CH (ClientHello), SH (ServerHello), EE (EncryptedExtensions), CT (Certificate), CR (CertificateRequest), NST (NewSessionTicket), and HRR (HelloRetryRequest). If an implementation receives an extension which it recognizes and which is not specified for the message in which it appears, it MUST abort the handshake with an "illegal_parameter" alert. Rescorla Standards Track [Page 36]
RFC 8446 TLS August 2018 +--------------------------------------------------+-------------+ | Extension | TLS 1.3 | +--------------------------------------------------+-------------+ | server_name [RFC6066] | CH, EE | | | | | max_fragment_length [RFC6066] | CH, EE | | | | | status_request [RFC6066] | CH, CR, CT | | | | | supported_groups [RFC7919] | CH, EE | | | | | signature_algorithms (RFC 8446) | CH, CR | | | | | use_srtp [RFC5764] | CH, EE | | | | | heartbeat [RFC6520] | CH, EE | | | | | application_layer_protocol_negotiation [RFC7301] | CH, EE | | | | | signed_certificate_timestamp [RFC6962] | CH, CR, CT | | | | | client_certificate_type [RFC7250] | CH, EE | | | | | server_certificate_type [RFC7250] | CH, EE | | | | | padding [RFC7685] | CH | | | | | key_share (RFC 8446) | CH, SH, HRR | | | | | pre_shared_key (RFC 8446) | CH, SH | | | | | psk_key_exchange_modes (RFC 8446) | CH | | | | | early_data (RFC 8446) | CH, EE, NST | | | | | cookie (RFC 8446) | CH, HRR | | | | | supported_versions (RFC 8446) | CH, SH, HRR | | | | | certificate_authorities (RFC 8446) | CH, CR | | | | | oid_filters (RFC 8446) | CR | | | | | post_handshake_auth (RFC 8446
Known issues with Android Studio and Android Gradle Plugin
This page tracks known issues with Android Studio 4.0 and Android Gradle plugin 4.0. If you experience an issue not already included here, please report a bug.
Upgrade to preview: Each release of Android Studio and the Android Gradle plugin aims to improve stability and performance, and add new features. To experience the benefits of upcoming releases now, download and install Android Studio Preview.
Known Issues with Android Studio
This section describes known issues that exist in the latest stable version of Android Studio.
Restart to apply memory settings from previous version of IDE
After updating Android Studio, you need to restart Android Studio to apply any memory settings migrated from an earlier version of the IDE.
We've discovered in testing that the first time you run Studio after updating, it will not yet be running with any custom configured memory settings, which for some users will result in significantly slower performance. To work around this issue, just restart Studio once you've upgraded and before you begin using the IDE. We have fixed this bug in Android Studio 4.1 and later.
Missing Run, Debug, and Profile toolbar buttons
If you have customized the Run/Debug group of action buttons—for example, by modifying options under Appearance & Behavior > Menus and Toolbars in the Settings or Preferences window—those action buttons might disappear from the toolbar after you restart the IDE. This is a known issue in the version of IntelliJ that Android Studio 4.0 is built on (see issue IDEA-228450).
To resolve this issue, revert any customizations you have made to those buttons as follows:
- Select File > Settings (or Android Studio > Preferences on macOS).
- On the left of the window, navigate to Appearance & Behavior > Menus and Toolbars.
- On the right side of the window, navigate to Main Toolbar > Toolbar Run Actions and select Run/Debug.
- Near the top of the window, click Revert.
 and select Restore Run/Debug.
and select Restore Run/Debug. - Click OK. You should now see the missing buttons in the toolbar.
Key mapping conflicts on Linux
On Linux, certain keyboard shortcuts conflict with default Linux keyboard shortcuts and those of popular window managers, such as KDE and GNOME. These conflicting keyboard shortcuts may not work as expected in Android Studio.
More information about this issue (including potential workarounds) can be found in IntelliJ's bug tracker.
Small UI text on Chrome OS
On Chrome OS, text might appear much smaller than in previous releases. To work around this issue, do the following:
- Open the Settings window by clicking File > Settings
- Navigate to Appearance & Behavior > Appearance.
- Select Use custom font.
- Increase the font size.
- In the Settings window, navigate to Editor > Font.
- Increase the font size.
- Click OK.
Code editing
This section describes known issues related to the code editor.
Frozen keyboard input - "iBus" problems on Linux
There are some known interactions between the iBus daemon on Linux and Android Studio. In some scenarios, the IDE stops responding to keyboard input or starts inputting random characters. This bug is triggered by some missing synchronization between iBus and XLib + AWT, and has already been reported upstream to JetBrains and iBus. There are three current workarounds for this issue:
- Workaround 1: Force iBus into synchronous mode. Before starting Android Studio, run the following on the command line: $ IBUS_ENABLE_SYNC_MODE=1 ibus-daemon -xrd
- Workaround 2: Disable iBus input in Android Studio. To disable iBus input for Android Studio only, run the following on the command line: $ XMODIFIERS= ./bin/studio.sh This workaround only disables input methods for Android Studio, not any other applications you may be running. Note that if you restart the daemon while Android Studio is running (for example, by running ), you effectively disable the input methods for all other applications and may also crash Android Studio's JVM with a segmentation fault.
- Workaround 3: Double-check the shortcut bindings to make sure that the Next input shortcut is not set to Control+Space, since this is also the code completion shortcut in Android Studio. Ubuntu 14.04 (Trusty) makes Super+Space the default shortcut, but settings from previous versions may still be around. To check your shortcut bindings, run on the command line to open the IBus Preferences window. Under Keyboard Shortcuts, check the Next input method. If it is set to Control+Space, change it to Super+Space, or another shortcut of your choice.
Project configuration
This section describes known issues related to project configuration and Gradle sync.
Gradle Sync Failed: Broken Pipe
The issue is that the Gradle daemon is trying to use IPv4 instead of IPv6.
- Workaround 1: On Linux, put the following in your or :
- Workaround 2: in Android Studio's vmoptions file, change the line to For more information, see the Networking IPv6 User Guide.
"peer not authenticated" errors from Gradle sync or SDK Manager
The root cause of these errors is a missing certificate in . To resolve these errors, proceed as follows:
- If you're behind a proxy, try to connect directly. If the direct connection works, then in order to connect via the proxy you may need to use to add the proxy server's certificate to the cacerts file.
- Re-install a supported, unmodified JDK. There's a known issue affecting Ubuntu users, which results in an empty . To work around this issue, execute the following on the command line: sudo /var/lib/dpkg/info/ca-certificates-java.postinst configure
Deploying
This section describes known issues related to deploying your app to a connected device.
Android Emulator HAXM on macOS High Sierra
The Android Emulator on macOS High Sierra (10.13) requires HAXM 6.2.1+ for best compatibility and stability with macOS. However, macOS 10.13 has a more involved process to install kernel extensions such as HAXM. You need to manually allow the kernel extension itself to be installed as follows:
- First, attempt to install the latest version of HAXM from the SDK Manager.
- In MacOS, go to System Preferences > Security and Privacy.
If you see an alert that System software from developer "Intel Corporation Apps" was blocked from loading, click Allow:
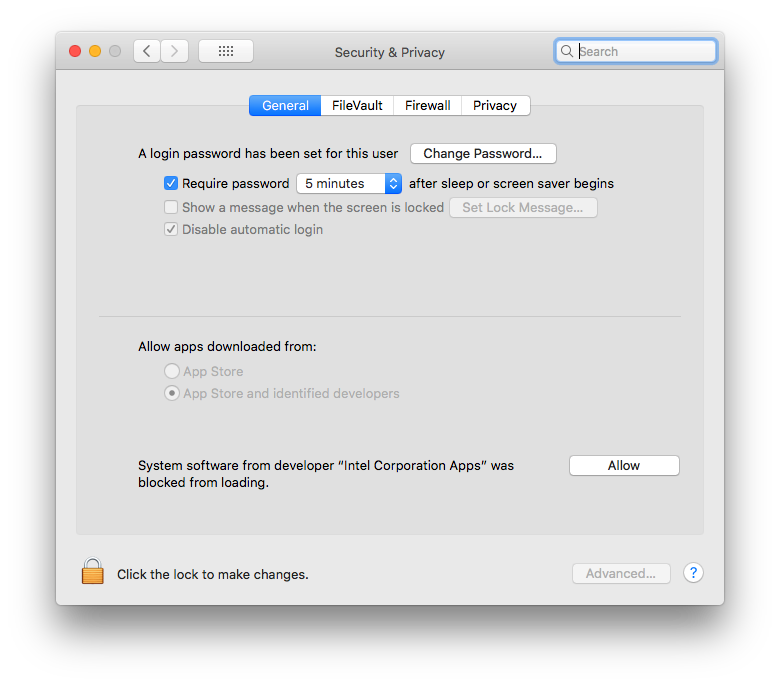
For more information and workarounds, see this Apple webpage and issue 62395878.
Apply Changes
This section describes known issues that are related to Apply Changes.
New app name not applied
If you rename your app and then try to apply that change, the updated name might not be reflected. To work around this issue, click Run to re-deploy your app and see your changes.
to re-deploy your app and see your changes.
Issue in Android Runtime throws error
If you're using a device that runs Android 8.0 or 8.1, you might encounter "VERIFICATION_ERROR" messages when trying to apply certain types of changes (especially if you're using Kotlin). This message is caused by an issue with the Android Runtime that is fixed in Android 9.0 and higher. Although the issue causes Apply Changes to fail, you can still Run your app again to see your changes. However, we recommend that you upgrade the device to Android 9.0 or greater.
your app again to see your changes. However, we recommend that you upgrade the device to Android 9.0 or greater.
Apply Changes fails with ShellCommandUnresponsiveException
When using Apply Changes in Android Studio 4.1 and lower, it is possible for a device to get stuck in a state that prevents any changes from being applied to that device. When this issue occurs, Apply Changes fails with a .
To work around this issue, run the following ADB command:
adb shell rm -fr /data/local/tmp/.studio Note: This issue is fixed in Android Studio 4.2 Canary 10 and higher. If you have Android Studio set to receive updates on the Canary or Dev channel, you can get the latest version by choosing Help > Check for Updates (Android Studio > Check for Updates on macOS). Otherwise, you can download it from the Android Studio preview page.Cannot apply changes when using android:sharedUserId
If you try to make changes to a class that hasn't yet been deployed to your running app, Apply Changes will fail if your app is configured in either of the following ways:
When Apply Changes fails due to this issue, Android Studio displays the following message:
To work around this issue in Android Studio 3.5, click Run to re-deploy your app and see your changes.
to re-deploy your app and see your changes.
Debugging and testing
This section describes known issues related to debugging and testing your app.
JUnit tests missing resources in classpath when run from Android Studio
If you have specific resource folders in your Java modules, then those resources won't be found when running tests from the IDE. Running tests using Gradle from the command line will work. Executing the Gradle task from the IDE will also work. See issue 64887 for more details.
This issue occurs because as of IntelliJ 13, which requires that you only have a single folder as the classpath. IntelliJ's builder copies all resources into that build folder, but Gradle doesn't copy over the resources.
- Workaround 1: Run the Gradle task from the IDE rather than running a unit test.
- Workaround 2: Update your build script to manually copy resources into the build folder. See comment #13 for more information.
Running JUnit tests may compile the code twice
When creating a new project, the template JUnit configuration might be created with two "Before launch" steps: Make and Gradle-aware Make. This configuration is then propagated to all created JUnit run configurations.
- To fix the issue for the current project, click Run > Edit Configurations and change the default JUnit configuration to only include the Gradle-aware Make step.
- To fix the issue for all future projects, click File > Close Project. You should see the welcome screen. Then click Configure > Project Defaults > Run Configurations and change the JUnit configuration to only include the Gradle-aware Make step.
Some test run configurations don't work
Not all run configurations that are available when right-clicking a test method are valid. Specifically, the following configurations are not valid:
- Gradle run configurations (which have a Gradle logo as the icon) don't work.
- JUnit run configurations (which have an icon without the green Android) don't apply to instrumentation tests, which cannot be run on the local JVM.
Adding Java breakpoints while debugging native code
While your app is paused at a breakpoint in your native code, the Auto and Dual debuggers may not immediately recognize new Java breakpoints that you set. To avoid this issue, add Java breakpoints either before starting a debug session or while the app is paused on a Java breakpoint. For more information, see issue 229949.
Stepping out of the native debugger
While using the Auto or Dual debugger to debug Java and native code, if you step into a native function from your Java code (for example, the debugger pauses execution at a line in your Java code that calls a native function and you click Step Into ) and you want to return to your Java code, click Resume Program
) and you want to return to your Java code, click Resume Program (instead of Step Out
(instead of Step Out or Step Over
or Step Over ). Your app process will still be paused, so click Resume Program
). Your app process will still be paused, so click Resume Program in the -java tab to resume it. For more information, see issue 224385.
in the -java tab to resume it. For more information, see issue 224385.
Profilers
This section describes known issues with the Profilers.
Timeout errors in CPU Profiler
You may experience "Recording failed to stop" errors in the Android Studio CPU Profiler when you select the Sample Java Methods or Trace Java Methods configurations. These are often timeout errors, especially if you see the following error message in the file:
The timeout errors tend to affect traced methods more than sampled methods and longer recordings more than shorter recordings. As a temporary workaround, it may be helpful to try shorter recordings to see if the error disappears.
If you experience timeout issues with the Profiler, please file a bug that includes the make/model of your device(s) and any relevant entries from and logcat.
ADB exception when debugging or profiling
When using Platform Tools 29.0.3, native debugging and the Android Studio Profilers might not work properly, and you might see either "AdbCommandRejectedException" or "Failed to connect port" in the file when you select Help > Show Log. Upgrading the Platform Tools to 29.0.4 or higher fixes both issues.
To upgrade the Platform Tools, do the following:
- Open the SDK Manager from Android Studio by clicking Tools > SDK Manager or click SDK Manager
 in the toolbar.
in the toolbar. - Click the checkbox next to Android SDK Platform-Tools so it shows a checkmark. A download icon
 should appear in the left column.
should appear in the left column. - Click Apply or OK.
Known issues with the Android Gradle Plugin
This section describes known issues that exist in the latest stable version of the Android Gradle plugin.
Missing Manifest class
If your app defines custom permissions in its manifest, the Android Gradle plugin typically generates a class that includes your custom permissions as String constants. The plugin packages this class with your app, so you can more easily reference those permissions at runtime.
Generating the manifest class is currently broken in Android Gradle plugin 3.6.0 and higher. If you build your app with this version of the plugin, and it references the manifest class, you might see a exception. To resolve this issue, do one of the following:
- Reference your custom permissions by their fully-qualified name. For example, .
Define your own constants, as shown below:
Signing file named with Carriage Return (CR) characters
JAR signing (v1 scheme) does not support file names containing Carriage Return (CR) characters. (See issue #63885809).
API changes
Android Gradle Plugin 3.0.0 and higher introduce API changes that remove certain functionalities and may break your existing builds. Later versions of the plugin may introduce new public APIs that replace broken functionalities.
Modifying variant outputs at build time may not work
Using the Variant API to manipulate variant outputs is broken with the new plugin. It still works for simple tasks, such as changing the APK name during build time, as shown below:
// If you use each() to iterate through the variant objects, // you need to start using all(). That's because each() iterates // through only the objects that already exist during configuration time— // but those object don't exist at configuration time with the new model. // However, all() adapts to the new model by picking up object as they are // added during execution. android.applicationVariants.all { variant -> variant.outputs.all { outputFileName = "${variant.name}-${variant.versionName}.apk" } }However, more complicated tasks that involve accessing objects no longer work. That's because variant-specific tasks are no longer created during the configuration stage. This results in the plugin not knowing all of its outputs up front, but it also means faster configuration times.
manifestOutputFile is no longer available
The method is no longer available, and you get the following error when you call it:
A problem occurred configuring project ':myapp'. Could not get unknown property 'manifestOutputFile' for task ':myapp:processDebugManifest' of type com.android.build.gradle.tasks.ProcessManifest.Instead of calling to get the manifest file for each variant, you can call to return the path of the directory that contains all generated manifests. You can then locate a manifest and apply your logic to it. The sample below dynamically changes the version code in the manifest:
android.applicationVariants.all { variant -> variant.outputs.all { output -> output.processManifest.doLast { // Stores the path to the maifest. String manifestPath = "$manifestOutputDirectory/AndroidManifest.xml" // Stores the contents of the manifest. def manifestContent = file(manifestPath).getText() // Changes the version code in the stored text. manifestContent = manifestContent.replace('android:versionCode="1"', String.format('android:versionCode="%s"', generatedCode)) // Overwrites the manifest with the new text. file(manifestPath).write(manifestContent) } } }Fixed known issues
This section describes known issues that have been fixed in a recent release. If you are experiencing any of these issues, you should update Android Studio to the latest stable or preview version.
Fixed in Android Studio 3.6
APK installation error on LineageOS: Deploying your app to devices running certain versions of LineageOS or CyanogenMod might fail and throw an exception.
On Android Studio 3.6 Beta 1 and higher, the IDE handles this exception by performing a full app install when you deploy your app to LineageOS or CyanogenMod devices, which might result in longer deploy times.
Fixed in Android Studio 3.5.2
- Broken XML code style: When editing XML code, the IDE applied an incorrect code style when you selected Code > Reformat Code from the menu bar.
Fixed in Android Studio 3.3.1
Out of memory errors when scanning C++-based projects: When Gradle scans a project that has C++ code in more than one location on the same drive, the scan includes all directories below the first common directory. Scanning a large number of directories and files may lead to out of memory errors.
For more information on this issue, read the bug associated with the issue.


Stores default configuration settings. Changes to this object are reflected in all editor instances, if not specified otherwise for a particular instance.
Read more about setting CKEditor configuration in the documentation.
Config options
since 4.1.0
The following values are accepted:
In all cases filter configuration may be extended by extraAllowedContent. This option may be especially useful when you want to use the default value along with some additional rules.
It is also possible to disallow some already allowed content. It is especially useful when you want to "trim down" the content allowed by default by editor features. To do that, use the disallowedContent option.
Read more in the documentation and see the example.
Defaults to
Specifies the widget to use to automatically embed a link. The default value of this option defines that either the Media Embed or Semantic Media Embed widgets will be used, depending on which is enabled.
The general behavior:
- If a string (widget names separated by commas) is provided, then the first of the listed widgets which is registered will be used. For example, if is set and widgets and are registered, then will be used.
- If a callback is specified, then it will be executed with the URL to be embedded and it should return the name of the widget to be used. It allows to use different embed widgets for different URLs.
Example:
Using with custom embed widgets:
Note: Plugin names are always lower case, while widget names are not, so widget names do not have to equal plugin names. For example, there is the plugin and the widget.
Read more in the documentation and see the example.
Defaults to
Extra vertical space to be added between the content and the editor bottom bar when adjusting editor height to content by using the Auto Grow feature. This option accepts a value in pixels, without the unit (for example: ).
Read more in the documentation and see the example.
Defaults to
The maximum height that the editor can assume when adjusting to content by using the Auto Grow feature. This option accepts a value in pixels, without the unit (for example: ). Zero () means that the maximum height is not limited and the editor will expand infinitely.
Read more in the documentation and see the example.
Defaults to
The minimum height that the editor can assume when adjusting to content by using the Auto Grow feature. This option accepts a value in pixels, without the unit (for example: ).
Read more in the documentation and see the example.
Defaults to
Whether automatic editor height adjustment brought by the Auto Grow feature should happen on editor creation.
Read more in the documentation and see the example.
Defaults to
since 3.6.0deprecated
Whether to automatically create wrapping blocks around inline content inside the document body. This helps to ensure the integrity of the block Enter mode.
Note: This option is deprecated. Changing the default value might introduce unpredictable usability issues and is highly unrecommended.
Defaults to
Whether the element replaced by the editor (usually a ) is to be updated automatically when posting the form containing the editor.
The autocomplete keystrokes used to finish autocompletion with the selected view item. This setting will set completing keystrokes for each autocomplete plugin respectively.
To change completing keystrokes individually use the CKEDITOR.plugins.autocomplete.commitKeystrokes plugin property.
Commit keystroke can also be disabled by setting it to an empty array.
Defaults to
Commit keystrokes can be also disabled by setting it to an empty array.
Defaults to
Defaults to
Defaults to
The base Z-index for floating dialog windows and popups.
Defaults to
The base href URL used to resolve relative and absolute URLs in the editor content.
Defaults to
Whether to escape basic HTML entities in the document, including:
Note: This option should not be changed unless when outputting a non-HTML data format like BBCode.
Defaults to
The keystrokes that are blocked by default as the browser implementation is buggy. These default keystrokes are handled by the editor.
Defaults to
since 3.1.0
Sets the attribute to be used on the element of the editing area. This can be useful when you intend to reuse the original CSS file you are using on your live website and want to assign the editor the same class as the section that will include the contents. In this way class-specific CSS rules will be enabled.
Note: The editor needs to load stylesheets containing contents styles. You can either copy them to the file that the editor loads by default or set the contentsCss option.
Note: This setting only applies to classic editor (the one that uses ).
Defaults to
since 3.1.0
Sets the attribute to be used on the element of the editing area. This can be useful when you intend to reuse the original CSS file you are using on your live website and want to assign the editor the same ID as the section that will include the contents. In this way ID-specific CSS rules will be enabled.
Defaults to
since 3.0.2
Whether to show the browser native context menu when the or (Mac) key is pressed on opening the context menu with the right mouse button click or the key.
Defaults to
since 4.0.0
The default content type that is used when pasted data cannot be clearly recognized as HTML or text.
For example: may come from a plain text editor or a website. It is not possible to recognize the content type in this case, so the default type will be used. At the same time it is clear that is HTML and its origin is a web page, email or another rich text editor.
Note: If content type is text, then styles of the paste context are preserved.
See also the CKEDITOR.editor.paste event and read more about the integration with clipboard in the Clipboard Deep Dive guide.
Defaults to
Duration of the notification displayed after pasting was blocked by the browser.
The URL to the security token endpoint in your application. The role of this endpoint is to securely authorize the end users of your application to use CKEditor Cloud Services, only if they should have access e.g. to upload files with Easy Image.
You can find more information about token endpoints in the Easy Image - Quick Start and Cloud Services - Creating token endpoint documentation.
Without a properly working token endpoint (token URL) CKEditor plugins will not be able to connect to CKEditor Cloud Services.
Defaults to
The upload URL is unique for each customer and can be found in the CKEditor Ecosystem dashboard after subscribing to the Easy Image service. To learn how to start using Easy Image, refer to the Easy Image Integration documentation.
Note: Make sure to also set the cloudServices_tokenUrl configuration option.
Defaults to
Sets GeSHi URL which, once queried with Ajax, will return highlighted code.
Check the Code Snippet GeSHi documentation for more information.
Defaults to
Restricts languages available in the "Code Snippet" dialog window. An empty value is always added to the list.
Note: If using a custom highlighter library (the default is highlight.js), you may need to refer to external documentation to set properly.
Read more in the documentation and see the example.
Defaults to
Note: This will only work with the default highlighter (highlight.js).
Read more in the documentation and see the example.
Defaults to
Stores the style definition that applies the text background color.
Note: Advanced Content Filter (ACF) is not updated automatically by a custom style definition. You may need to add additional ACF rules, so the customized style element is not removed. Learn more how to configure ACF with Advanced Content Filter guide.
Read more in the documentation and see the example.
Since 4.15.0: Added property, which can be used instead of a property to customize background style. For example to add custom class:
Defaults to
Defines the colors to be displayed in the color selectors. This is a string containing hexadecimal notation for HTML colors, without the prefix.
Since 3.3: A color name may optionally be defined by prefixing the entries with a name and the slash character. For example, will be displayed as the color in the selector, but will be output as . This behaviour was altered in version 4.12.0.
Since 4.6.2: The default color palette has changed. It contains fewer colors in more pastel shades than the previous one.
Since 4.12.0: Defining colors with names works in a different way. Colors names can be defined by . The color name is only used in the tooltip. The output will now use the color code. For example, will be displayed as the color in the selector, and will be output as .
Read more in the documentation and see the example.
Defaults to
Defines how many colors will be shown per row in the color selectors.
Read more in the documentation and see the example.
Defaults to
Whether to enable the Automatic button in the color selectors.
Read more in the documentation and see the example.
Defaults to
Whether to enable the More Colors button in the color selectors.
What’s New in the Code Red HTML Editor v1.3.4 serial key or number?
Screen Shot

System Requirements for Code Red HTML Editor v1.3.4 serial key or number
- First, download the Code Red HTML Editor v1.3.4 serial key or number
-
You can download its setup from given links:


