
Simply ID 4.1 serial key or number
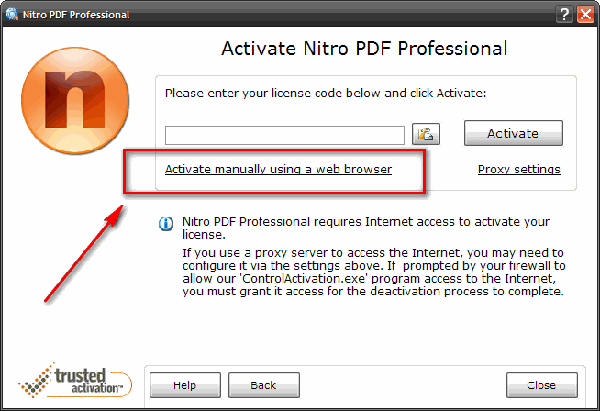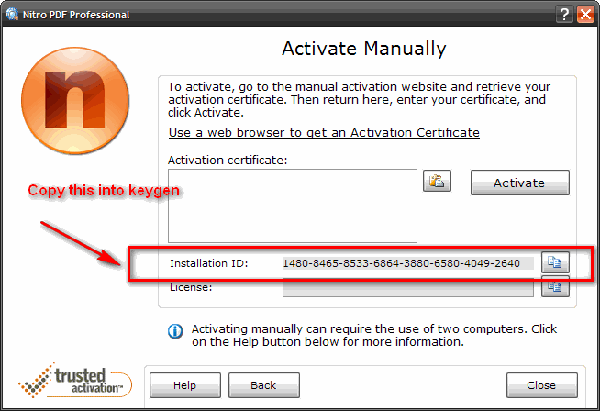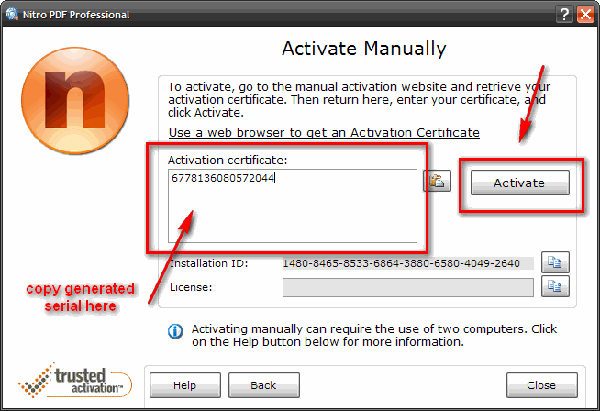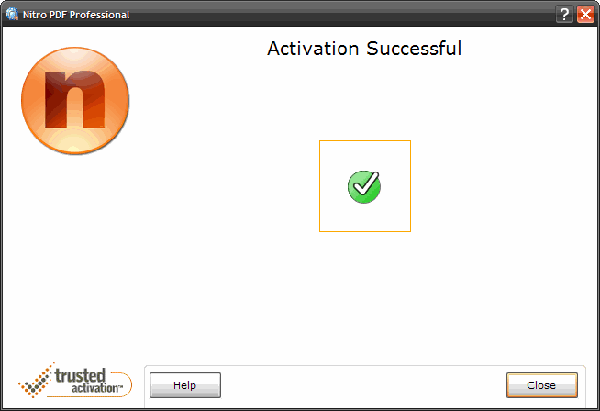
Simply ID 4.1 serial key or number
Oracle Exadata System Software uses keys to identify clients and determine access rights to the grid disks.
To determine which clients have access to a grid disk, a key is generated using CellCLI and stored in a read-only file that is accessible only by the clients. The CellCLI command generates a random hexadecimal string for use as a security key. This key is stored in a file on the client side, and assigned to the targets on the storage servers using the command.
Note:
The client name or Oracle ASM cluster name not case-sensitive. For example, and are treated as the same value.The command can be run on any cell. You should only run this command when you need to create a new unique key. If you are configuring ASM-scoped security, then only a single security key is needed for each Oracle ASM cluster. If you are configuring DB-scoped security, then one key is needed for each Oracle ASM cluster and an additional security key is needed for each database client.
For ASM-scoped security, the file is only accessible by the Oracle ASM cluster and its database clients. For DB-scoped security multiple security keys are used. One key is assigned to the Oracle ASM cluster, and one key is assigned to each database client. These security keys are stored in separate files, and each file is accessible only by the client.
The file contains entries that configure security among Oracle ASM, database clients and cells. The and values in the files on the Oracle ASM and database host computers must match the values assigned to the clients on the cells.
The file contains the following fields:
— This field is required.
For ASM-scoped security, this key must match the value of the key assigned to the Oracle ASM cluster with the CellCLI command.
For DB-scoped security, this key must match the value of the key assigned to the database client with the CellCLI command.
— This field is required.
This field contains a unique identifier for each Oracle ASM cluster. This value must be unique among all the clusters that access the storage servers in the storage grid. This value is used in the command run on each cell, and the and commands used to configure grid disks to allow access from only a specific Oracle ASM cluster.
Note:
The field is used when configuring both ASM-scoped security and DB-scoped security.
Access to the file is controlled by operating system privileges.
For Oracle ASM clients, the file is stored in the directory, and is readable by the Oracle Grid Infrastructure software owner and the group to which the user belongs.
For DB-scoped security, there is a for Oracle ASM, readable only by the Oracle Grid Infrastructure software owner, and additional files for each database client. For the database clients, the file is stored in the directory of the Oracle home directory for each database. The file for a database is readable only by the operating system user that owns the Oracle Database software installation.
Note:
The Oracle Grid Infrastructure and Oracle Database software must by owned by different operating system users to implement DB-scoped security.
On the storage servers, you use the command to store the security keys in an access control list (ACL) for the cells. You use the command to set the access rights for individual grid disks with the attribute. In order to access a grid disk, the security key of the cell ACL must match the security key of the client and the unique name of the client must be included in the attribute of the grid disk.
The identifying names used for the Oracle ASM and database must be unique. However, in some environments, there is more than one database with the same value for the . Each database uses a different Oracle ASM cluster for storage. Starting with Oracle Exadata System Software release 12.2.1.1.0, you can define ASM-scoped security based on Oracle ASM clusters. You use the keyword with the command. When you use the keyword, the database name is qualified by the Oracle ASM unique identifier, creating a unique ID for each database, even if they have the same . Within each Oracle ASM cluster, the database names still have to be unique.
If you configure ASM-scoped security or DB-scoped security, then you also need to configure security keys to enable cell-to-cell operations. You create a key for each storage server, or cell, and assign that key as a local key for the cell using the command. You then assign the keys for the other cells that perform cell-to-cell operations with the current cell using the command.
Example 4-5 Creating a Security Key for Exadata Storage Security
Use the following command on any storage server to generate a unique security key. This key will be used to configure ASM-scoped security or DB-scoped security.
Example 4-6 cellkey.ora File Entries
This example shows the entries for the file.
ID Works Identification Software 6.5 Upgrade
Updated 12/17/2018
If you are using ID Works v6.0 software and plan to continue to use Microsoft Windows 2000 or XP operating system, you do not need to upgrade to v6.5 as no new features have been added. If you do not have a card printer driver that is Vista operating system compatible, or if you are using the TruFinger Print solution, do NOT upgrade. If you are using TruPhoto solution, you must have v6.5 or greater and if you are using TruSignature solution, you must have v6.5. All components must be Vista operating system compatible for the solution to run on Vista.
Before installing the upgrade, read the complete description. If your card printer is not Vista operating system compatible, please do not upgrade.
If you have any questions regarding upgrades, please contact your Datacard service provider.
This upgrade will install the new software for the following products:
- Datacard® ID Works™ Enterprise Edition software
- Datacard® ID Works™ Entterprise Production software
- Datacard® ID Works™ Enterprise Designer software
- Datacard® ID Works™ Standard Edition software
- Datacard® ID Works™ Standard Production software
- Datacard® ID Works™ Standard Designer software
- Datacard® ID Works™ Basic Edition software
Before installing the software, please make sure that you are using ID Works v6.0. If you have an older version of ID Works software, please contact your Datacard Service Provider to discuss an upgrade. If you upgrade to ID Works v6.5 software to run on Vista operating system and are using any of the software offerings listed below, you must also upgrade those applications to be compatible. If you are using hardware that is not Vista operating system compatible, do not upgrade.
- Datacard® Visitor Manager™ software v6.5 upgrade
- Datacard® TruPhoto v7.1 software upgrade - obsolete. This is replaced by the Datacard DSLR Plugin.
- Datacard® TruSignature™ v6.5 software upgrade
![]() 119.1 MB .zip
119.1 MB .zip
Datacard® DSLR-1 v1.3 Camera Plug in for ID Works, IDCentre, WebID
Updated 1/30/2018
If you are using ID Works, IDCentre, or WebID and would like to incorporate facial capture functionality with Cannon EOS Rebel T5 / 1200D camera, download and run the attached file.
DSLR v1.3 Camera Plug in uses Canon ED SDK v3.6.1. The EOS Rebel T6 camera has been tested by Entrust Datacard
Entrust Datacard supports the use of DSLR v1.3 camera plug-in software with the following applications:
- Datacard ID Works® v6.5 (Basic, Standard and Enterprise)
- Datacard IDCentre™ v6.5 (Bronze, Silver and Gold)
- Datacard WebID™ Workstation v6 or later
Operating systems supported by the applications listed above are supported by the DSLR v1.3 camera plug-in with the following exceptions:
- Windows 2000 is not supported by the camera plug-in
- Windows XP 64-bit is not supported by the camera plug-in
NOTE: Prior to installing v1.3, make sure that previous versions of the plug-in are uninstalled.
When using the camera with ID Works/ID Centre, make sure the dial on the camera is set to P. If this is not set you will not see the menus to configure the camera.
![]() 11.5 MB .ZIP
11.5 MB .ZIP
ID Works v5.1 Plug-in for the SD/CD or CE Printers
Updated 3/12/2014
Download and install this plug-in if you are using a Datacard SD/CD or CE printer with ID Works v5.1 identification software. The plug-in is required to support card production features such as K panel printing, topcoat application, and magnetic stripe encoding.
The plug-in requires the following to install and function:
- ID Works v5.1 Service Pack 1
- XPS Card Printer Driver v4.1 or later
- Windows XP Service Pack 3
NOTE: This plug-in version replaces the plug-in included with the v5.0 XPS Card Printer driver installation. The plug-in included with the v5.0 driver installation does not support ID Works v5.1 software..
![]() 8.4 MB .ZIP
8.4 MB .ZIP
Datacard® DSLR-2 Camera Plug in for ID Works, IDCentre, WebID
Updated 9/14/2015
If you are using ID Works, IDCentre, or WebID and would like to incorporate facial capture functionality with Cannon EOS Rebel T5 / 1200D camera, download and run the attached file.
DSLR v1.2 Camera Plug in uses Canon ED SDK v2.14. EOS Rebel T5 camera has been tested by Entrust Datacard.
Entrust Datacard supports the use of DSLR v1.2 camera plug-in software with the following applications:
- Datacard ID Works® v6.5 (Basic, Standard and Enterprise)
- Datacard IDCentre™ v6.5 (Bronze, Silver and Gold)
- Datacard WebID™ Workstation v6 or later
Operating systems supported by the applications listed above are supported by the DSLR v1.2 camera plug-in with the following exceptions:
- Windows 2000 is not supported by the camera plug-in
- Windows XP 64-bit is not supported by the camera plug-in
NOTE: When using the camera with ID Works/ID Centre, make sure the dial on the camera is set to P. If this is not set you will not see the menus to configure the camera.
![]() 9.5 MB .ZIP
9.5 MB .ZIP
ID Works v6.5 Support for 64-bit Microsoft® Operating Systems
Updated 1/13/2020
For customers who wish to use Datacard® ID Works® Identification Software v6.5 and Datacard® IDCentre™ Identification Software v6.5 on Microsoft® 64-bit Operating Systems, download and run the attached file. The upgrade installs the necessary 64-bit prerequisite software enabling you to run on that operating system. A 64 bit printer driver for your printer is also required.
![]() 50.3 MB .zip
50.3 MB .zip
ID Works software v6.5 upgrade
Updated 9/18/2008
If you are using ID Works v6.0 software and plan to continue to use Microsoft Windows 2000, Windows XP or Windows 7 operating system, you will need to upgrade to v6.5. If you do not have a card printer driver that is Vista or Windows 7 operating system compatible, or if you are using the Tru Fingerprint solution, do NOT upgrade. If you are using Tru Photo solution, you must have v6.5 or greater and if you are using Tru Signature solution, you must have v6.5. All components must be Vista or Windows 7 operating system compatible for the solution to run on Vista.
Before installing the upgrade, read the complete description. If you are using Tru Capture solutions, you must use the Vista or Windows 7 operating system compatible software version and hardware noted in the description. If your card printer is not Vista or Windows 7 operating system compatible, please do not upgrade.
If you have any questions regarding upgrades, please contact your Datacard service provider.
This upgrade will install the new software for the following products::
- Datacard® ID Works® Enterprise software
- Datacard® ID Works® Enterprise Production software
- Datacard® ID Works® Enterprise Designer software
- Datacard® ID Works® Standard software
- Datacard® ID Works® Standard Production software
- Datacard® ID Works® Standard Designer software
- Datacard® ID Works® Basic software
- Datacard® ID Works® Intro software
Before installing the software, please make sure that you are using ID Works v6.0. If you have an older version of ID Works software, please contact your Datacard Service Provider to discuss an upgrade. If you upgrade to ID Works v6.5 software to run on Vista operating system and are using any of the software offerings listed below, you must also upgrade those applications to be compatible. If you are using hardware that is not Vista operating system compatible, do not upgrade.
- Datacard® ID Works® Visitor Manager software v6.5 upgrade
- Datacard® Tru Photo™ v 7.1 software upgrade
- Datacard® Tru™ Signature Pointe v6.5 software upgrade
![]() 119.1 MB .zip
119.1 MB .zip
software downloads
ECHELON IzoT CT 4.1 LICENSE AGREEMENT
I.NOTICE
This Echelon Service Pack License Agreement ("Agreement") is entered into between you ("You" or "Your") and Echelon Corporation ("Echelon") with respect to your use of the Echelon Service Pack Software made available for download by Echelon (“Software"). If you are entering into this Agreement on behalf of a company or other legal entity, (a) you represent that you have the right to bind them to this Agreement, and (b) the reference to You and Your refers to that company or entity. YOU MUST READ AND AGREE TO THE TERMS OF THIS AGREEMENT BEFORE DOWNLOADING, INSTALLING OR USING THE SOFTWARE. BY DOWNLOADING, INSTALLING OR USING THE SOFTWARE, YOU AGREE TO BE BOUND BY THE TERMS AND CONDITIONS OF THIS AGREEMENT. IF YOU DO NOT AGREE WITH THE TERMS AND CONDITIONS OF THIS AGREEMENT, DO NOT DOWNLOAD, INSTALL OR USE THE SOFTWARE.
II.LICENSE GRANT
The terms of Your use of the Software is governed by the terms of Your license to use the software that has been updated, revised or otherwise modified by the Service Pack (the “Original Software"). If there was no license that was provided with or included in the Original Software, Echelon grants You a non-exclusive, non-sublicensable, revocable, limited license (“License") to use the Software solely in connection with those activities or functions for which the Original Software was provided (the “Purpose").
III.PERMITTED USE
The License permits you to:
(a)download, install and use the Software solely for the Purpose; and(b)copy the documentation included with the Software ("Documentation") for internal reference use in connection with the Purpose, provided that You reproduce, unaltered, all proprietary notices on or in the copy.
IV.RESTRICTIONS AND INDEMNITY
The License shall not permit You or allow You to permit others to:
(a)use the Software or Documentation for any purpose other than the Purpose;
(b)copy the Software other than making a reasonable number of copies for archival purposes or as necessary to use the Software;
(c)modify, translate, create derivative works of, reverse engineer, decompile, disassemble or otherwise attempt (i) to defeat, avoid, bypass, remove, deactivate, or otherwise circumvent any software protection mechanisms in the Software, including without limitation any such mechanism used to restrict or control the functionality of the Software, or (ii) to derive the source code or the underlying ideas, algorithms, structure or organization of the Software (except to the extent that such activities may not be prohibited under applicable law);
(d)permit any third party to use the Software or Documentation; or
(e)remove or modify any proprietary legends or notices contained on or in the Software or Documentation.
The License is not a sale. Title and copyrights to the Software, Documentation, and any copy made by You remain with Echelon or its suppliers. Unauthorized copying of the Software or Documentation, or failure to comply with this Section IV, will result in automatic termination of the License and will make available to Echelon and its suppliers other legal remedies.
You agree to indemnify, to the fullest extent permitted by law, Echelon and its directors, officers, agents, employees and suppliers (“Indemnitees"), for any third party claims, actions, proceedings, liabilities, loss, damage, cost, or expenses (including, without limitation, attorneys' fees), arising out of or in connection with Your use of the Software or Documentation, your violation of applicable law or your breach of this Agreement. Echelon reserves the right, at your expense to assume the exclusive defense and control of any matter for which you are required to indemnify Echelon, and you agree to cooperate with the defense of such claims. You agree not to settle such matter without Echelon's prior consent.
V.TERMINATION
Unless earlier automatically terminated as provided in Section IV, the License will continue until terminated by either party in writing. Upon termination of the License for any reason You shall destroy all copies of the Software and Documentation.
VI. CONFIDENTIALITY
The Software, including in its object code form, and any Documentation marked as "confidential" or "proprietary", together with any information provided to You by Echelon in connection with the License that a reasonable person would deem confidential given the nature of the information, constitutes "Confidential Information" of Echelon or its suppliers. You agree not to use any Confidential Information for any purpose not permitted by this Agreement, and that you will make such Confidential Information available only to Your employees that require access to such Confidential Information in connection with exercising Your rights under the License. You agree that you will protect such Confidential Information from unauthorized use, disclosure or access in the same manner as You protect your own confidential or proprietary information of a similar nature and with no less than reasonable care. Your obligations with respect to Confidential Information shall continue during the term of the License and for a period of five years after its termination.
VII.WARRANTY AND DISCLAIMER
THE SOFTWARE AND DOCUMENTATION ARE PROVIDED “AS IS" AND WITHOUT WARRANTY, WHETHER EXPRESS, IMPLIED, STATUTORY OR GIVEN IN ANY COMMUNICATION WITH YOU. ECHELON AND ITS SUPPLIERS SPECIFICALLY DISCLAIM ANY IMPLIED WARRANTY AND CONDITION OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, SATISFACTORY QUALITY, TITLE, AND NONINFRINGEMENT, AND THEIR EQUIVALENTS. YOU ACKNOWLEDGE THAT ECHELON'S DISTRIBUTORS AND SALES REPRESENTATIVES ARE NOT AUTHORIZED TO PROVIDE ANY WARRANTIES IN ADDITION TO, OR IN CONFLICT WITH, THE PROVISIONS OF THIS SECTION.
The provision of the Software does not extend the period of the warranty, if any, applicable to the Original Software.
VIII.LIMITATION OF LIABILITY
IN NO EVENT WILL ECHELON AND ITS SUPPLIERS BE LIABLE FOR ANY DAMAGES, INCLUDING WITHOUT LIMITATION, DIRECT, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER (INCLUDING DAMAGES RESULTING FROM LOSS OR CORRUPTION OF DATA, LOST PROFITS, LOSS OF CONTRACTS AND COST OF PROCUREMENT OF SUBSTITUTE GOODS, TECHNOLOGY OR SERVICES) ARISING FROM THE SUPPLY, USE OR PERFORMANCE OF THE SOFTWARE AND DOCUMENTATION, HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY (INCLUDING CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION). THIS LIMITATION WILL APPLY EVEN IF ECHELON OR AN AUTHORIZED DISTRIBUTOR OR SALES REPRESENTATIVE HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
IX.COMPLIANCE WITH LAWS
You agree to comply with all applicable laws and regulations in connection with your use of the Software and Documentation. This includes, but is not limited to, export and re-export control laws and regulations of the United States and any other applicable jurisdiction (“Export Laws"). You covenant that You shall not—directly or indirectly—sell, export, re-export, transfer, divert, or otherwise dispose of any software, source code, or technology (including products derived from or based on such technology) received from Echelon under this Agreement to any country (or national thereof) subject to antiterrorism controls or U.S. embargo, or to any other person, entity, or destination prohibited by the laws or regulations of the United States, without obtaining prior authorization. You warrant that you are not prohibited under the Export Laws from downloading, installing or using the Software and Documentation. You agree to indemnify, to the fullest extent permitted by law, Echelon (and its officers, directors, employees, agents and suppliers) from and against any fines or penalties that may arise as a result of Your breach of this provision. This provision shall survive termination or expiration of this Agreement.
X.LANGUAGE
The parties hereto confirm that it is their wish that this Agreement, as well as other documents relating hereto, have been and shall be written in the English language only.
Les parties aux présentes confirment leur volonté que cette convention de même que tous les documents y compris tout avis qui s'y rattache, soient rédigés en langue anglaise.
XI.GENERAL
This Agreement shall not be governed by the 1980 U.N. Convention on Contracts for the International Sale of Goods, but shall be governed by the laws of the State of California, including the Uniform Commercial Code as enacted in California, without reference to conflicts of laws principles. This Agreement is the entire agreement between us and supersedes any other communications or advertising with respect to the Software and Documentation. The waiver of a breach of any provision of this Agreement shall not be construed as a waiver of any other provision or any other breach. If any provision of this Agreement is held invalid or unenforceable, such provision shall be revised to the extent necessary to cure the invalidity or unenforceability, and the remainder of the Agreement shall continue in full force and effect.
If You are acquiring the Software and Documentation on behalf of any part of the U.S. Government, the following provisions apply. The Software and Documentation were developed at private expense and are deemed to be "commercial computer software" and "commercial computer software documentation", respectively, pursuant to DFAR Section 227.7202 and FAR 12.212(b), as applicable. Any use, modification, reproduction, release, performance, display or disclosure of the Software or Documentation by the U.S. Government or any of its agencies shall be governed solely by the terms of this Agreement and shall be prohibited except to the extent expressly permitted by the terms of this Agreement.
What’s New in the Simply ID 4.1 serial key or number?
Screen Shot

System Requirements for Simply ID 4.1 serial key or number
- First, download the Simply ID 4.1 serial key or number
-
You can download its setup from given links:


