
Password Kit Enterprise Edition 7.0 serial key or number
Password Kit Enterprise Edition 7.0 serial key or number
Microsoft Surface Enterprise Management Mode
- 14 minutes to read
Microsoft Surface Enterprise Management Mode (SEMM) is a feature of Surface devices with Surface UEFI that allows you to secure and manage firmware settings within your organization. With SEMM, IT professionals can prepare configurations of UEFI settings and install them on a Surface device. In addition to the ability to configure UEFI settings, SEMM also uses a certificate to protect the configuration from unauthorized tampering or removal. SEMM is a requirement to be able to migrate a Surface Hub 2S to Windows 10 Pro and Enterprise.
Note
SEMM is only available on devices with Surface UEFI firmware. This comprises most other Surface devices including Surface Pro 7, Surface Pro X, Surface Hub 2S, and Surface Laptop 3 commercial SKUs with an Intel processor. SEMM is not supported on the 15" Surface Laptop 3 SKU with AMD processor (only available as a retail SKU).
When Surface devices are configured by SEMM and secured with the SEMM certificate, they are considered enrolled in SEMM. When the SEMM certificate is removed and control of UEFI settings is returned to the user of the device, the Surface device is considered unenrolled in SEMM.
There are two administrative options you can use to manage SEMM and enroll Surface devices – a standalone tool or integration with Microsoft Endpoint Configuration Manager. The SEMM standalone tool, called the Microsoft Surface UEFI Configurator, is described in this article. For more information about how to manage SEMM with Microsoft Endpoint Configuration Manager, see Use Microsoft Endpoint Configuration Manager to manage devices with SEMM.
Microsoft Surface UEFI Configurator
The primary workspace of SEMM is Microsoft Surface UEFI Configurator, as shown in Figure 1. Microsoft Surface UEFI Configurator is a tool used to create Windows Installer (.msi) packages or WinPE images used to enroll, configure, and unenroll SEMM on a Surface device. These packages contain a configuration file where the settings for UEFI are specified. SEMM packages also contain a certificate, which is installed and stored in firmware and used to verify the signature of configuration files before UEFI settings are applied.
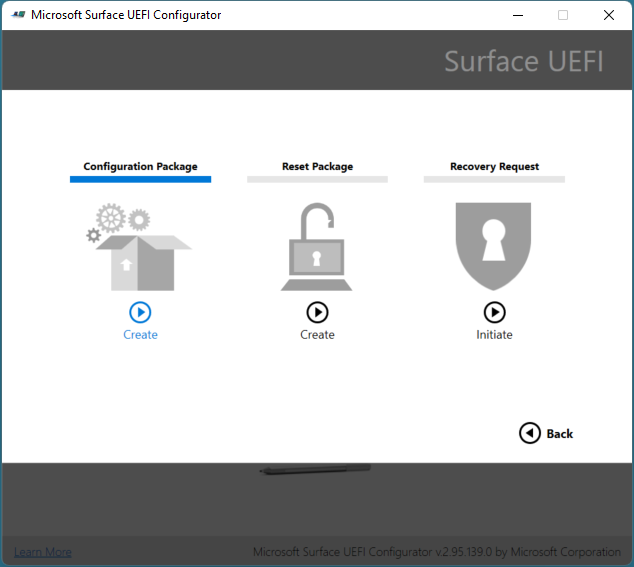
Figure 1. Microsoft Surface UEFI Configurator
You can use the Microsoft Surface UEFI Configurator tool in three modes:
Download Microsoft Surface UEFI Configurator
You can download Microsoft Surface UEFI Configurator from the Surface Tools for IT page in the Microsoft Download Center.
Configuration package
Surface UEFI configuration packages are the primary mechanism to implement and manage SEMM on Surface devices. These packages contain a configuration file of UEFI settings specified during creation of the package in Microsoft Surface UEFI Configurator and a certificate file, as shown in Figure 2. When a configuration package is run for the first time on a Surface device that is not already enrolled in SEMM, it provisions the certificate file in the device’s firmware and enrolls the device in SEMM. When enrolling a device in SEMM, you will be prompted to confirm the operation by providing the last two digits of the SEMM certificate thumbprint before the certificate file is stored and the enrollment can complete. This confirmation requires a user be physically present at the device at the time of enrollment to perform the confirmation.
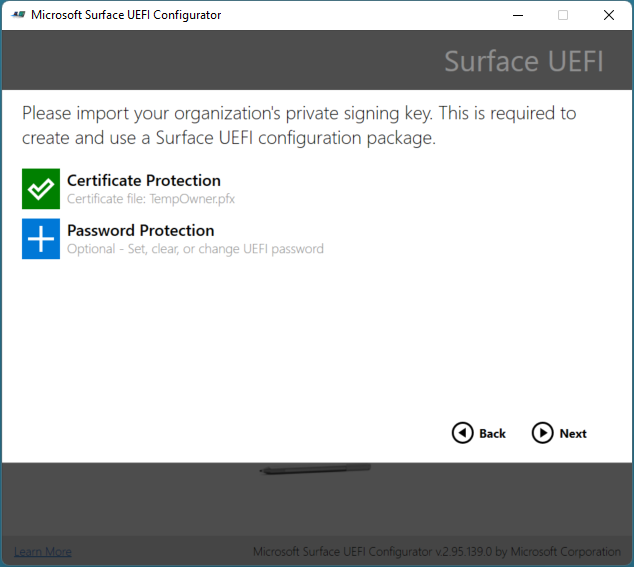
Figure 2. Secure a SEMM configuration package with a certificate
See the Surface Enterprise Management Mode certificate requirements section of this article for more information about the requirements for the SEMM certificate.
Note
You can also specify a UEFI password with SEMM that is required to view the Security, Devices, Boot Configuration, or Enterprise Management pages of Surface UEFI.
After a device is enrolled in SEMM, the configuration file is read and the settings specified in the file are applied to UEFI. When you run a configuration package on a device that is already enrolled in SEMM, the signature of the configuration file is checked against the certificate that is stored in the device firmware. If the signature does not match, no changes are applied to the device.
Enable or disable devices in Surface UEFI with SEMM
The following list shows all the available devices you can manage in SEMM:
- Docking USB Port
- On-board Audio
- DGPU
- Type Cover
- Micro SD Card
- Front Camera
- Rear Camera
- Infrared Camera, for Windows Hello
- Bluetooth Only
- Wi-Fi and Bluetooth
- LTE
Note
The built-in devices that appear in the UEFI Devices page may vary depending on your device or corporate environment. For example, the UEFI Devices page is not supported on Surface Pro X; LTE only appears on LTE-equipped devices.
Configure advanced settings with SEMM
Table 1. Advanced settings
| Setting | Description |
|---|---|
| IPv6 for PXE Boot | Allows you to manage IPv6 support for PXE boot. If you do not configure this setting, IPv6 support for PXE boot is disabled. |
| Alternate Boot | Allows you to manage use of an Alternate boot order to boot directly to a USB or Ethernet device by pressing both the Volume Down button and Power button during boot. If you do not configure this setting, Alternate boot is enabled. |
| Boot Order Lock | Allows you to lock the boot order to prevent changes. If you do not configure this setting, Boot Order Lock is disabled. |
| USB Boot | Allows you to manage booting to USB devices. If you do not configure this setting, USB Boot is enabled. |
| Network Stack | Allows you to manage Network Stack boot settings. If you do not configure this setting, the ability to manage Network Stack boot settings is disabled. |
| Auto Power On | Allows you to manage Auto Power On boot settings. If you do not configure this setting, Auto Power on is enabled. |
| Simultaneous Multi-Threading (SMT) | Allows you to manage Simultaneous Multi-Threading (SMT) to enable or disable hyperthreading. If you do not configure this setting, SMT is enabled. |
| Enable Battery limit | Allows you to manage Battery limit functionality. If you do not configure this setting, Battery limit is enabled |
| Security | Displays the Surface UEFI Security page. If you do not configure this setting, the Security page is displayed. |
| Devices | Displays the Surface UEFI Devices page. If you do not configure this setting, the Devices page is displayed. |
| Boot | Displays the Surface UEFI Boot page. If you do not configure this setting, the Boot page is displayed. |
| DateTime | Displays the Surface UEFI DateTime page. If you do not configure this setting, the DateTime page is displayed. |
| EnableOSMigration | Allows you to migrate Surface Hub 2 from Windows 10 Team to Windows 10 Pro or Enterprise. If you do not configure this setting, Surface Hub 2 devices can only run Windows 10 Team OS. Note: Dual booting between Windows 10 Team and Windows 10 Pro/Enterprise is not available on Surface Hub 2. |
Note
When you create a SEMM configuration package, two characters are shown on the Successful page, as shown in Figure 3.
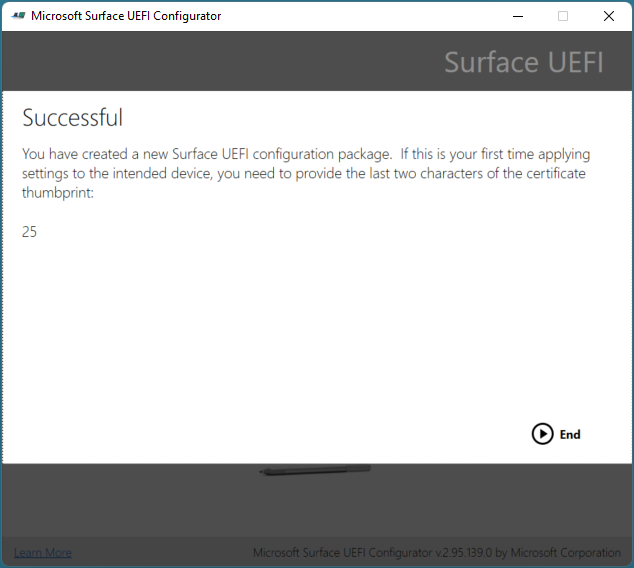
Figure 3. Display of the last two characters of the certificate thumbprint on the Successful page
These characters are the last two characters of the certificate thumbprint and should be written down or recorded. The characters are required to confirm enrollment in SEMM on a Surface device, as shown in Figure 4.

Figure 4. Enrollment confirmation in SEMM with the SEMM certificate thumbprint
Note
Administrators with access to the certificate file (.pfx) can read the thumbprint at any time by opening the .pfx file in CertMgr. To view the thumbprint with CertMgr, follow this process:
- Right-click the .pfx file, and then click Open.
- Expand the folder in the navigation pane.
- Click Certificates.
- Right-click your certificate in the main pane, and then click Open.
- Click the Details tab.
- All or Properties Only must be selected in the Show drop-down menu.
- Select the field Thumbprint.
To enroll a Surface device in SEMM or to apply the UEFI configuration from a configuration package, all you need to do is run the .msi file with administrative privileges on the intended Surface device. You can use application deployment or operating system deployment technologies such as Microsoft Endpoint Configuration Manager or the Microsoft Deployment Toolkit. When you enroll a device in SEMM you must be physically present to confirm the enrollment on the device. User interaction is not required when you apply a configuration to devices that are already enrolled in SEMM.
For a step-by-step walkthrough of how to enroll a Surface device in SEMM or apply a Surface UEFI configuration with SEMM, see Enroll and configure Surface devices with SEMM.
Reset package
A Surface UEFI reset package is used to perform only one task — to unenroll a Surface device from SEMM. The reset package contains signed instructions to remove the SEMM certificate from the device’s firmware and to reset UEFI settings to factory default. Like a Surface UEFI configuration package, a reset package must be signed with the same SEMM certificate that is provisioned on the Surface device. When you create a SEMM reset package, you are required to supply the serial number of the Surface device you intend to reset. SEMM reset packages are not universal and are specific to one device.
Recovery request
In some scenarios, it may be impossible to use a Surface UEFI reset package. (For example, if Windows becomes unusable on the Surface device.) In these scenarios you can unenroll the Surface device from SEMM through the Enterprise Management page of Surface UEFI (shown in Figure 5) with a Recovery Request operation.

Figure 5. Initiate a SEMM recovery request on the Enterprise Management page
When you use the process on the Enterprise Management page to reset SEMM on a Surface device, you are provided with a Reset Request. This Reset Request can be saved as a file to a USB drive, copied as text, or read as a QR Code with a mobile device to be easily emailed or messaged. Use the Microsoft Surface UEFI Configurator Reset Request option to load a Reset Request file or enter the Reset Request text or QR Code. Microsoft Surface UEFI Configurator will generate a verification code that can be entered on the Surface device. If you enter the code on the Surface device and click Restart, the device will be unenrolled from SEMM.
Note
A Reset Request expires two hours after it is created.
For a step-by-step walkthrough of how to unenroll Surface devices from SEMM, see Unenroll Surface devices from SEMM.
Surface Enterprise Management Mode certificate requirements
Using SEMM with Microsoft Surface UEFI Configurator requires a certificate to verify the signature of configuration files before UEFI settings can be applied. This certificate ensures that after a device is enrolled in SEMM, only packages created with the approved certificate can be used to modify the settings of UEFI.
Note
The SEMM certificate is required to perform any modification to SEMM or Surface UEFI settings on enrolled Surface devices. If the SEMM certificate is corrupted or lost, SEMM cannot be removed or reset. Manage your SEMM certificate accordingly with an appropriate solution for backup and recovery.
Packages created with the Microsoft Surface UEFI Configurator tool are signed with a certificate. This certificate ensures that after a device is enrolled in SEMM, only packages created with the approved certificate can be used to modify the settings of UEFI.
Recommended certificate settings
The following settings are recommended for the SEMM certificate:
- Key Algorithm – RSA
- Key Length – 2048
- Hash Algorithm – SHA-256
- Type – SSL Server Authentication
- Key Usage – Digital signature, Key Encipherment
- Provider – Microsoft Enhanced RSA and AES Cryptographic Provider
- Expiration Date – 15 Months from certificate creation
- Key Export Policy – Exportable
It is also recommended that the SEMM certificate be authenticated in a two-tier public key infrastructure (PKI) architecture where the intermediate certification authority (CA) is dedicated to SEMM, enabling certificate revocation. For more information about a two-tier PKI configuration, see Test Lab Guide: Deploying an AD CS Two-Tier PKI Hierarchy.
Self-signed certificate
You can use the following example PowerShell script to create a self-signed certificate for use in proof-of-concept scenarios. To use this script, copy the following text into Notepad and save the file as a PowerShell script (.ps1). Note: This script creates a certificate with a password of .The certificate generated by this script is not recommended for production environments.
Important
For use with SEMM and Microsoft Surface UEFI Configurator, the certificate must be exported with the private key and with password protection. Microsoft Surface UEFI Configurator will prompt you to select the SEMM certificate file (.pfx) and certificate password when it is required.
- Create a folder on your C: drive where you will save the script; for example, C:\SEMM.
- Copy the example script into Notepad or equivalent text editor and save the file as a PowerShell script (.ps1).
- Sign into your PC with administrator credentials and open an elevated PowerShell session.
- Ensure your permissions are set to allow scripts to run. By default, scripts are blocked from running unless you modify the execution policy. To learn more, see About Execution Policies.
- At the command prompt, enter the full path of the script and then press Enter. The script creates a Demo Certificate named TempOwner.pfx.
Alternatively, you can create your own self-signed certificate using PowerShell. For more information, see the following PowerShell documentation: New-SelfSignedCertificate.
Note
For organizations that use an offline root in their PKI infrastructure, Microsoft Surface UEFI Configurator must be run in an environment connected to the root CA to authenticate the SEMM certificate. The packages generated by Microsoft Surface UEFI Configurator can be transferred as files and therefore can be transferred outside the offline network environment with removable storage, such as a USB stick.
Managing certificates FAQ
The recommended minimum length is 15 months. You can use a certificate that expires in less than 15 months or use a certificate that expires in longer than 15 months.
Note
When a certificate expires, it does not automatically renew.
Will an expired certificate affect the functionality of SEMM-enrolled devices?
No, a certificate only impacts IT admin management tasks in SEMM and has no effect on device functionality when it expires.
Will the SEMM package and certificate need to be updated on all machines that have it?
If you want SEMM reset or recovery to work, the certificate needs to be valid and not expired.
Can bulk reset packages be created for each surface that we order? Can one be built that resets all machines in our environment?
The PowerShell samples that create a config package for a specific device type can also be used to create a reset package that is serial-number independent. If the certificate is still valid, you can create a reset package using PowerShell to reset SEMM.
Version History
Version 2.73.136.0
This version of SEMM includes:
- Audio can now be disabled on Surface Hub2S using SEMM
- Support to Surface Pro X for Dock 2
- Support to UEFI Manager for Dock 2 related operations
- Surface Go reset package bug fix
- Support for migrating Surface Hub 2 devices from Windows 10 Team OS to Windows 10 Pro or Enterprise.
Version 2.71.139.0
This version of SEMM adds support for Surface Dock 2 management features for Surface Book 3, Surface Laptop 3, and Surface Pro 7 including:
- Enabling audio (locking/unlocking), Ethernet and USB ports
- Ability to create dock packages for both authenticated and unauthenticated hosts
Version 2.70.130.0
This version of SEMM includes:
- Support for Surface Go 2
- Support for Surface Book 3
- Bug fixes
Version 2.59.139.0
- Support for Surface Pro 7, Surface Pro X, and Surface Laptop 3 13.5" and 15" models with Intel processor. Note: Surface Laptop 3 15" AMD processor is not supported.
- Support for Wake on Power feature
Version 2.54.139.0
- Support to Surface Hub 2S
- Bug fixes
Version 2.43.136.0
- Support to enable/disable simulatenous multithreating
- Separate options for WiFi and Bluetooth for some devices
- Battery Limit removed for Surface Studio
Version 2.26.136.0
- Add support to Surface Studio 2
- Battery Limit feature
Version 2.21.136.0
- Add support to Surface Pro 6
- Add support to Surface Laptop 2
Version 2.14.136.0
- Add support to Surface Go
Version 2.9.136.0
- Add support to Surface Book 2
- Add support to Surface Pro LTE
- Accessibility improvements
Version 1.0.74.0
- Add support to Surface Laptop
- Add support to Surface Pro
- Bug fixes and general improvement
Related topics
Find your Secret Key or Setup Code
Help
Do I have a Secret Key?
You have a Secret Key if you have a 1Password membership, or if you belong to a family or team account.
If you purchased a standalone license for 1Password, then you don’t have a Secret Key, and you don’t need to sign in when you open the app.
Locate your Secret Key or Setup Code:
Find your Secret Key on 1Password.com
You can find your Secret Key and Setup Code in your 1Password account on the web. Use a browser you’ve used to sign in to your account before, like the browser you used to create your account.
- Sign in to your 1Password account.
- Click your name in the top right and choose Get the Apps to see your Setup Code.
To view your Secret Key, click “Can’t scan your Setup Code? Sign in manually.”
Important
You won’t be able to find your Secret Key in Safari unless you sign in to your 1Password account at least once every 7 days. To make sure you can always access your account, set up the 1Password apps and download your Emergency Kit.
Find your Secret Key in the 1Password apps
You can find your Secret Key and Setup Code in the 1Password app on any device where you’re already signed in to your account.
Mac
- Open and unlock 1Password.
- Choose 1Password > Preferences.
- Click the Accounts icon, then select your account.
- Click your Secret Key to copy it. Or click “Set up other devices” to see your Setup Code.
Windows
- Open and unlock 1Password.
- Choose Accounts and select your account.
- Select your Secret Key > Copy to copy it. Or select “Set up other devices” to see your Setup Code.
iOS
- Open and unlock 1Password.
- Tap Settings > 1Password Accounts.
- Tap your account, then tap your Secret Key and choose Copy. Or tap Set Up Other Devices to see your Setup Code.
Android
- Open and unlock 1Password.
- Tap Settings > “1Password accounts”.
- Tap your account, then tap your Secret Key and choose Reveal. Or tap “Set up other devices” to see your Setup Code.
Find your Secret Key in your Emergency Kit
You can find your Secret Key and Setup Code in your Emergency Kit, which you downloaded if you created your account on 1Password.com.
If you don’t remember saving your Emergency Kit, look in your Downloads folder for a PDF file named “1Password Emergency Kit”.
Learn more about your Emergency Kit.
Get more help
Your Secret Key is your secret. It protects your account together with your Master Password, which only you know. We don’t have a copy of your Secret Key or any way to recover or reset it for you. To find your Secret Key, you’ll need one of the following:
- the 1Password app on any device where you’re already signed in to your account
- a browser you’ve used to sign in to your account before
- your Emergency Kit
If you don’t have one of those, but you belong to a family or team account, ask a family organizer or team administrator to recover your account.
If you’ve lost access to a device, learn how to regenerate your Secret Key.
If you still can’t find your Secret Key, and a family organizer or team administrator isn’t able to recover your account, you’ll have to start over.
Learn more
Passware Kit Business
| Microsoft Word | |||||
| Microsoft Excel | |||||
| Microsoft PowerPoint |
| Local Administrator on workstation | |||||
| Other local accounts | ౼ | ౼ | |||
| Server accounts | ౼ | ౼ | |||
| Microsoft Live ID accounts | ౼ | ౼ | |||
| Domain Administrator | ౼ | ౼ | ౼ |
| Archives (.zip, .7z, .rar, .exe) | ౼ |
| ౼ | |||||
| MS Outlook (PST, email accounts) | ౼ | ||||
| MS Access | ౼ | ||||
| VBA projects (MS Access, Word, PowerPoint, Excel) | ౼ | ||||
| QuickBooks databases | ౼ | ౼ | |||
| FileMaker | ౼ | ౼ |
| APFS | ౼ | ౼ | ౼ | ||
| Apple DMG | ౼ | ౼ | ౼ | ||
| BitLocker | ౼ | ౼ | ౼ | ||
| DriveCrypt | ౼ | ౼ | ౼ | ||
| FileVault2 | ౼ | ౼ | ౼ | ||
| LUKS disk images | ౼ | ౼ | ౼ | ||
| McAfee Drive Encryption | ౼ | ౼ | ౼ | ||
| PGP | ౼ | ౼ | ౼ | ||
| Symantec Endpoint Encryption | ౼ | ౼ | ౼ | ||
| TrueCrypt | ౼ | ౼ | ౼ | ||
| VeraCrypt | ౼ | ౼ | ౼ |
| Android backups | ౼ | ౼ | ౼ | ౼ | |
| Android physical images | ౼ | ౼ | ౼ | ౼ | |
| Dropbox data | ౼ | ౼ | ౼ | ౼ | |
| iCloud keychain extraction | ౼ | ౼ | ౼ | ౼ | |
| iOS iCloud backups | ౼ | ౼ | ౼ | ౼ | |
| iOS iCloud photo streams | ౼ | ౼ | ౼ | ౼ | |
| iTunes mobile backup | ౼ | ౼ | ౼ | ౼ | |
| MS OneDrive data | ౼ | ౼ | ౼ | ౼ |
| Password Exchange | ౼ | ౼ | ౼ | ౼ |
| 1Password | ౼ | ౼ | |||
| KeePass | ౼ | ౼ | |||
| LastPass | ౼ | ౼ | |||
| masOS Keychain | ౼ | ౼ | ౼ |
| Windows/Unix/Mac hashes | ౼ | ౼ | ౼ |
| 160 other file types supported | ౼ | ౼ | ౼ |
| Password recovery for OS user accounts and websites | ౼ | ౼ | ౼ | ||
| Authentication data extraction for iCloud, MS OneDrive, etc. | ౼ | ౼ | ౼ | ౼ | |
| Decryption of hard disk images | ౼ | ౼ | ౼ |
| Support for distributed and Amazon cloud password recovery | ౼ | ౼ | ౼ | ||
| Passware Kit Agents included | ౼ | ౼ | ౼ | 0 | 5 |
| Automatic updates for the Server and the Agents | ౼ | ౼ | ౼ |
| Batch files processing | ౼ | ౼ | ౼ |
| Automatic software updates ? | ౼ | ౼ | ౼ | 1 year included, optional subscription | 1 year included, optional subscription |
| Price | $49 | $79 | $195 | $875 | $1,095 |
What’s New in the Password Kit Enterprise Edition 7.0 serial key or number?
Screen Shot

System Requirements for Password Kit Enterprise Edition 7.0 serial key or number
- First, download the Password Kit Enterprise Edition 7.0 serial key or number
-
You can download its setup from given links:




