
Command and Conquer Red Alert 2 v1.00 serial key or number

Command and Conquer Red Alert 2 v1.00 serial key or number
Command & Conquer 3
Tiberium Wars - Kane Edition
Kane's Wrath [Add-On]
| Backup & Installation Notes |
|
SetupDiag
Applies to

About SetupDiag
Current downloadable version of SetupDiag: 1.6.0.42
Always be sure to run the most recent version of SetupDiag, so that can access new functionality and fixes to known issues.
SetupDiag is a standalone diagnostic tool that can be used to obtain details about why a Windows 10 upgrade was unsuccessful.
SetupDiag works by examining Windows Setup log files. It attempts to parse these log files to determine the root cause of a failure to update or upgrade the computer to Windows 10. SetupDiag can be run on the computer that failed to update, or you can export logs from the computer to another location and run SetupDiag in offline mode.
SetupDiag in Windows 10, version 2004 and later
With the release of Windows 10, version 2004, SetupDiag is included with Windows Setup.
During the upgrade process, Windows Setup will extract all its sources files to the %SystemDrive%$Windows.~bt\Sources directory. With Windows 10, version 2004 and later, setupdiag.exe is also installed to this directory. If there is an issue with the upgrade, SetupDiag will automatically run to determine the cause of the failure.
When run by Windows Setup, the following parameters are used:
- /ZipLogs:False
- /Format:xml
- /Output:%windir%\logs\SetupDiag\SetupDiagResults.xml
- /RegPath:HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupDiag\Results
The resulting SetupDiag analysis can be found at %WinDir%\Logs\SetupDiag\SetupDiagResults.xml and in the registry under HKLM\SYSTEM\Setup\SetupDiag\Results.
If the upgrade process proceeds normally, the Sources directory including setupdiag.exe is moved under %SystemDrive%\Windows.Old for cleanup. If the Windows.old directory is deleted later, setupdiag.exe will also be removed.
Using SetupDiag
To quickly use SetupDiag on your current computer:
- Verify that your system meets the requirements described below. If needed, install the .NET framework 4.6.
- Download SetupDiag.
- If your web browser asks what to do with the file, choose Save. By default, the file will be saved to your Downloads folder. You can also save it to a different location if desired by using Save As.
- When SetupDiag has finished downloading, open the folder where you downloaded the file. By default, this is your Downloads folder, which is displayed in File Explorer under Quick access in the left navigation pane.
- Double-click the SetupDiag file to run it. Click Yes if you are asked to approve running the program.
- Double-clicking the file to run it will automatically close the command window when SetupDiag has completed its analysis. If you wish to keep this window open instead, and review the messages that you see, run the program by typing SetupDiag at the command prompt instead of double-clicking it. You will need to change directories to the location of SetupDiag to run it this way.
- A command window will open while SetupDiag diagnoses your computer. Wait for this to finish.
- When SetupDiag finishes, two files will be created in the same folder where you double-clicked SetupDiag. One is a configuration file, the other is a log file.
- Use Notepad to open the log file: SetupDiagResults.log.
- Review the information that is displayed. If a rule was matched, this can tell you why the computer failed to upgrade, and potentially how to fix the problem. See the Text log sample below.
For instructions on how to run the tool in offline mode and with more advanced options, see the Parameters and Examples sections below.
The Release notes section at the bottom of this topic has information about recent updates to this tool.
Requirements
The destination OS must be Windows 10.
.NET Framework 4.6 must be installed. If you are not sure what version of .NET is currently installed, see How to: Determine Which .NET Framework Versions Are Installed. You can also use the following command-line query to display the installed v4 versions:
Parameters
| Parameter | Description |
|---|---|
| /? |
|
| /Output:<path to results file> |
|
| /LogsPath:<Path to logs> |
|
| /ZipLogs:<True | False> |
|
| /Format:<xml | json> |
|
| /Scenario:[Recovery] |
|
| /Verbose |
|
| /NoTel |
|
| /AddReg |
|
| /RegPath |
|
Note: The /Mode parameter is deprecated in version 1.4.0.0 of SetupDiag.
- In previous versions, this command was used with the LogsPath parameter to specify that SetupDiag should run in an offline manner to analyze a set of log files that were captured from a different computer. In version 1.4.0.0 when you specify /LogsPath then SetupDiag will automatically run in offline mode, therefore the /Mode parameter is not needed.
Examples:
In the following example, SetupDiag is run with default parameters (online mode, results file is SetupDiagResults.log in the same folder where SetupDiag is run).
In the following example, SetupDiag is run in online mode (this is the default). It will know where to look for logs on the current (failing) system, so there is no need to gather logs ahead of time. A custom location for results is specified.
The following example uses the /Output parameter to save results to a path name that contains a space:
The following example specifies that SetupDiag is to run in offline mode, and to process the log files found in D:\Temp\Logs\LogSet1.
The following example sets recovery scenario in offline mode. In the example, SetupDiag will search for reset/recovery logs in the specified LogsPath location and output the results to the directory specified by the /Output parameter.
The following example sets recovery scenario in online mode. In the example, SetupDiag will search for reset/recovery logs on the current system and output results in XML format.
Log files
Windows Setup Log Files and Event Logs has information about where logs are created during Windows Setup. For offline processing, you should run SetupDiag against the contents of the entire folder. For example, depending on when the upgrade failed, copy one of the following folders to your offline location:
\$Windows.~bt\sources\panther
\$Windows.~bt\Sources\Rollback
\Windows\Panther
\Windows\Panther\NewOS
If you copy the parent folder and all sub-folders, SetupDiag will automatically search for log files in all subdirectories.
Setup bug check analysis
When Microsoft Windows encounters a condition that compromises safe system operation, the system halts. This condition is called a bug check. It is also commonly referred to as a system crash, a kernel error, a Stop error, or BSOD. Typically a hardware device, hardware driver, or related software causes this error.
If crash dumps are enabled on the system, a crash dump file is created. If the bug check occurs during an upgrade, Windows Setup will extract a minidump (setupmem.dmp) file. SetupDiag can also debug these setup related minidumps.
To debug a setup related bug check, you must:
- Specify the /LogsPath parameter. You cannot debug memory dumps in online mode.
- Gather the setup memory dump file (setupmem.dmp) from the failing system.
- Setupmem.dmp will be created in either %SystemDrive%$Windows.~bt\Sources\Rollback, or in %WinDir%\Panther\NewOS\Rollback depending on when the bug check occurs.
- Install the Windows Debugging Tools on the computer that runs SetupDiag.
In the following example, the setupmem.dmp file is copied to the D:\Dump directory and the Windows Debugging Tools are installed prior to running SetupDiag:
Known issues
- Some rules can take a long time to process if the log files involved are large.
Sample output
The following is an example where SetupDiag is run in offline mode.
Rules
When searching log files, SetupDiag uses a set of rules to match known issues. These rules are contained in the rules.xml file which is extracted when SetupDiag is run. The rules.xml file might be updated as new versions of SetupDiag are made available. See the release notes section for more information.
Each rule name and its associated unique rule identifier are listed with a description of the known upgrade-blocking issue. In the rule descriptions, the term "down-level" refers to the first phase of the upgrade process, which runs under the starting OS.
- CompatScanOnly - FFDAFD37-DB75-498A-A893-472D49A1311D
- This rule indicates that setup.exe was called with a specific command line parameter that indicated setup was to do a compat scan only, not an upgrade.
- BitLockerHardblock - C30152E2-938E-44B8-915B-D1181BA635AE
- This is a block when the target OS does not support BitLocker, yet the host OS has BitLocker enabled.
- VHDHardblock - D9ED1B82-4ED8-4DFD-8EC0-BE69048978CC
- This block happens when the host OS is booted to a VHD image. Upgrade is not supported when the host OS is booted from a VHD image.
- PortableWorkspaceHardblock - 5B0D3AB4-212A-4CE4-BDB9-37CA404BB280
- This indicates that the host OS is booted from a Windows To-Go device (USB key). Upgrade is not supported in the Windows To-Go environment.
- AuditModeHardblock - A03BD71B-487B-4ACA-83A0-735B0F3F1A90
- This block indicates that the host OS is currently booted into Audit Mode, a special mode for modifying the Windows state. Upgrade is not supported from this state.
- SafeModeHardblock - 404D9523-B7A8-4203-90AF-5FBB05B6579B
- This block indicates that the host OS is booted to Safe Mode, where upgrade is not supported.
- InsufficientSystemPartitionDiskSpaceHardblock - 3789FBF8-E177-437D-B1E3-D38B4C4269D1
- This block is encountered when setup determines the system partition (where the boot loader files are stored) does not have enough space to be serviced with the newer boot files required during the upgrade process.
- CompatBlockedApplicationAutoUninstall – BEBA5BC6-6150-413E-8ACE-5E1EC8D34DD5
- This rule indicates there is an application that needs to be uninstalled before setup can continue.
- CompatBlockedApplicationDismissable - EA52620B-E6A0-4BBC-882E-0686605736D9
- When running setup in /quiet mode, there are dismissible application messages that turn into blocks unless the command line also specifies “/compat ignorewarning”. This rule indicates setup was executed in /quiet mode but there is an application dismissible block message that have prevented setup from continuing.
- CompatBlockedApplicationManualUninstall - 9E912E5F-25A5-4FC0-BEC1-CA0EA5432FF4
- This rule indicates that an application without an Add/Remove Programs entry, is present on the system and blocking setup from continuing. This typically requires manual removal of the files associated with this application to continue.
- HardblockDeviceOrDriver - ED3AEFA1-F3E2-4F33-8A21-184ADF215B1B
- This indicates a device driver that is loaded on the host OS is not compatible with the newer OS version and needs to be removed prior to the upgrade.
- HardblockMismatchedLanguage - 60BA8449-CF23-4D92-A108-D6FCEFB95B45
- This rule indicates the host OS and the target OS language editions do not match.
- HardblockFlightSigning - 598F2802-3E7F-4697-BD18-7A6371C8B2F8
- This rule indicates the target OS is a pre-release, Windows Insider build, and the target machine has Secure Boot enabled. This will block the pre-release signed build from booting if installed on the machine.
- DiskSpaceBlockInDownLevel - 6080AFAC-892E-4903-94EA-7A17E69E549E
- This failure indicates the system ran out of disk space during the down-level operations of upgrade.
- DiskSpaceFailure - 981DCBA5-B8D0-4BA7-A8AB-4030F7A10191
- This failure indicates the system drive ran out of available disk space at some point after the first reboot into the upgrade.
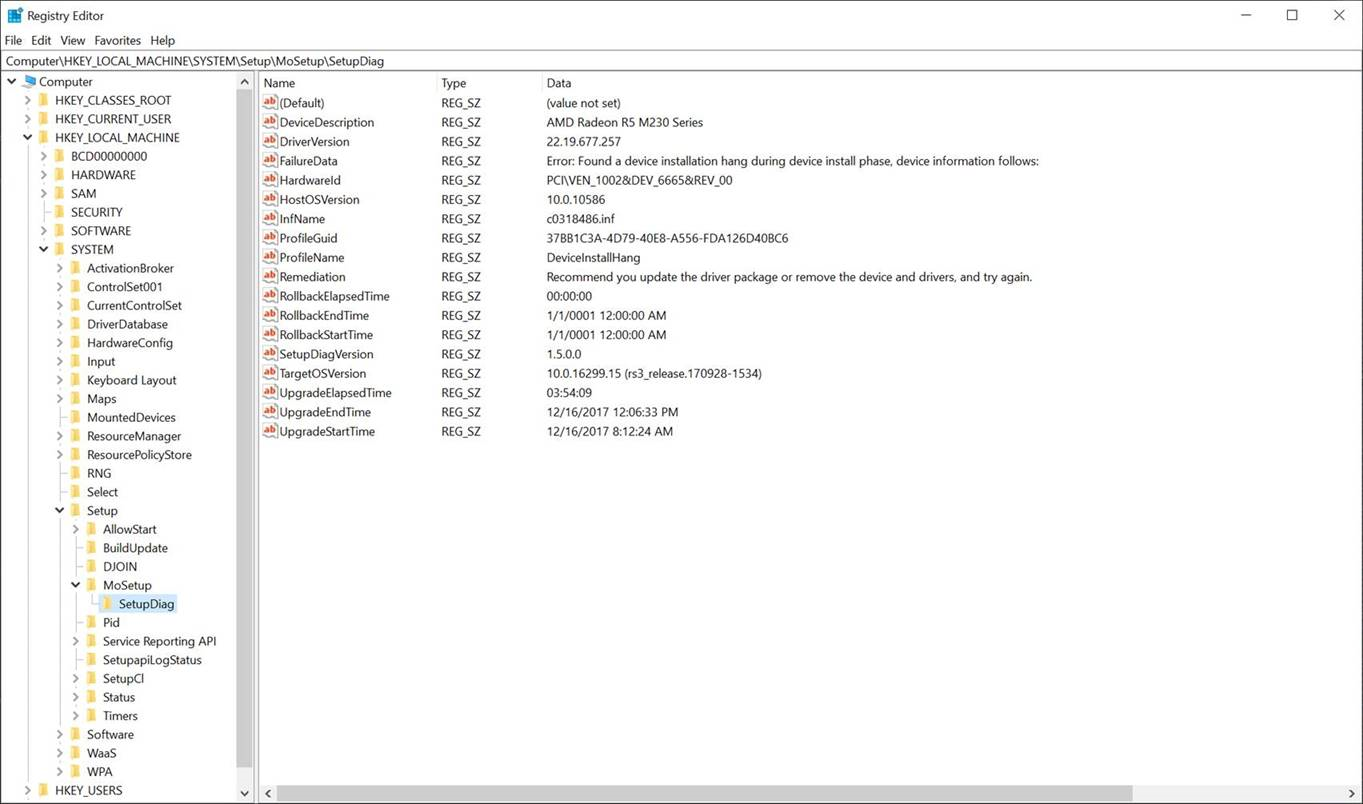
- DeviceInstallHang - 37BB1C3A-4D79-40E8-A556-FDA126D40BC6
- This failure rule indicates the system hung or bug checked during the device installation phase of upgrade.
- DebugSetupMemoryDump - C7C63D8A-C5F6-4255-8031-74597773C3C6
- This offline only rule indicates a bug check occurred during setup. If the debugger tools are available on the system, SetupDiag will debug the memory dump and provide details.
- DebugSetupCrash - CEEBA202-6F04-4BC3-84B8-7B99AED924B1
- This offline only rule indicates that setup itself encountered a failure that resulted in a process memory dump. If the debugger tools are installed on the system, SetupDiag will debug the memory dump and give further details.
- DebugMemoryDump - 505ED489-329A-43F5-B467-FCAAF6A1264C
- This offline only rule is for any memory.dmp file that resulted during the setup/upgrade operation. If the debugger tools are installed on the system, SetupDiag will debug the memory dump and give further details.
- BootFailureDetected - 4FB446C2-D4EC-40B4-97E2-67EB19D1CFB7
- This rule indicates a boot failure occurred during a specific phase of the update. The rule will indicate the failure code and phase for diagnostic purposes.
- FindDebugInfoFromRollbackLog - 9600EB68-1120-4A87-9FE9-3A4A70ACFC37
- This rule will determine and give details when a bug check occurs during the setup/upgrade process that resulted in a memory dump, but without the requirement of the debugger package being on the executing machine.
- AdvancedInstallerFailed - 77D36C96-32BE-42A2-BB9C-AAFFE64FCADC
- Finds fatal advanced installer operations that cause setup failures.
- FindMigApplyUnitFailure - A4232E11-4043-4A37-9BF4-5901C46FD781
- Detects a migration unit failure that caused the update to fail. This rule will output the name of the migration plug-in as well as the error code it produced for diagnostic purposes.
- FindMigGatherUnitFailure - D04C064B-CD77-4E64-96D6-D26F30B4EE29
- Detects a migration gather unit failure that caused the update to fail. This rule will output the name of the gather unit/plug-in as well as the error code it produced for diagnostic purposes.
- CriticalSafeOSDUFailure - 73566DF2-CA26-4073-B34C-C9BC70DBF043
- This rule indicates a failure occurred while updating the SafeOS image with a critical dynamic update. It will indicate the phase and error code that occurred while attempting to update the SafeOS image for diagnostic purposes.
- UserProfileCreationFailureDuringOnlineApply - 678117CE-F6A9-40C5-BC9F-A22575C78B14
- Indicates there was a critical failure while creating or modifying a User Profile during the online apply phase of the update. It will indicate the operation and error code associated with the failure for diagnostic purposes.
- WimMountFailure - BE6DF2F1-19A6-48C6-AEF8-D3B0CE3D4549
- This rule indicates the update failed to mount a wim file. It will show the name of the wim file as well as the error message and error code associated with the failure for diagnostic purposes.
- FindSuccessfulUpgrade - 8A0824C8-A56D-4C55-95A0-22751AB62F3E
- Determines if the given setup was a success or not based off the logs.
- FindSetupHostReportedFailure - 6253C04F-2E4E-4F7A-B88E-95A69702F7EC
- Gives information about failures surfaced early in the upgrade process by setuphost.exe
- FindDownlevelFailure - 716334B7-F46A-4BAA-94F2-3E31BC9EFA55
- Gives failure information surfaced by SetupPlatform, later in the down-level phase.
- FindAbruptDownlevelFailure - 55882B1A-DA3E-408A-9076-23B22A0472BD
- Gives last operation failure information when the system fails in the down-level, but the log just ends abruptly.
- FindSetupPlatformFailedOperationInfo - 307A0133-F06B-4B75-AEA8-116C3B53C2D1
- Gives last phase and error information when SetupPlatform indicates a critical failure. This rule will indicate the operation and error associated with the failure for diagnostic purposes.
- FindRollbackFailure - 3A43C9B5-05B3-4F7C-A955-88F991BB5A48
- Gives last operation, failure phase and error information when a rollback occurs.
- AdvancedInstallerGenericFailure – 4019550D-4CAA-45B0-A222-349C48E86F71
- A rule to match AdvancedInstaller read/write failures in a generic sense. Will output the executable being called as well as the error code and exit code reported.
- OptionalComponentFailedToGetOCsFromPackage – D012E2A2-99D8-4A8C-BBB2-088B92083D78 (NOTE: This rule replaces the OptionalComponentInstallFailure rule present in v1.10.
- This matches a specific Optional Component failure when attempting to enumerate components in a package. Will output the package name and error code.
- OptionalComponentOpenPackageFailed – 22952520-EC89-4FBD-94E0-B67DF88347F6
- Matches a specific Optional Component failure when attempting to open an OC package. Will output the package name and error code.
- OptionalComponentInitCBSSessionFailed – 63340812-9252-45F3-A0F2-B2A4CA5E9317
- Matches a specific failure where the advanced installer service or components aren’t operating or started on the system. Will output the error code.
- UserProfileCreationFailureDuringFinalize – C6677BA6-2E53-4A88-B528-336D15ED1A64
- Matches a specific User Profile creation error during the finalize phase of setup. Will output the failure code.
- WimApplyExtractFailure – 746879E9-C9C5-488C-8D4B-0C811FF3A9A8
- Matches a wim apply failure during wim extraction phases of setup. Will output the extension, path and error code.
- UpdateAgentExpanderFailure – 66E496B3-7D19-47FA-B19B-4040B9FD17E2
- Matches DPX expander failures in the down-level phase of update from WU. Will output the package name, function, expression and error code.
- FindFatalPluginFailure – E48E3F1C-26F6-4AFB-859B-BF637DA49636
- Matches any plug-in failure that setupplatform decides is fatal to setup. Will output the plugin name, operation and error code.
- AdvancedInstallerFailed - 77D36C96-32BE-42A2-BB9C-AAFFE64FCADC
- Indicates critical failure in the AdvancedInstaller while running an installer package, includes the .exe being called, the phase, mode, component and error codes.
- MigrationAbortedDueToPluginFailure - D07A24F6-5B25-474E-B516-A730085940C9
- Indicates a critical failure in a migration plugin that causes setup to abort the migration. Will provide the setup operation, plug-in name, plug-in action and error code.
- DISMAddPackageFailed - 6196FF5B-E69E-4117-9EC6-9C1EAB20A3B9
- Indicates a critical failure during a DISM add package operation. Will specify the Package Name, DISM error and add package error code.
- PlugInComplianceBlock - D912150B-1302-4860-91B5-527907D08960
- Detects all compat blocks from Server compliance plug-ins. Outputs the block information and remediation.
- AdvancedInstallerGenericFailure - 4019550D-4CAA-45B0-A222-349C48E86F71
- Triggers on advanced installer failures in a generic sense, outputting the application called, phase, mode, component and error code.
- FindMigGatherApplyFailure - A9964E6C-A2A8-45FF-B6B5-25E0BD71428E
- Shows errors when the migration Engine fails out on a gather or apply operation. Indicates the Migration Object (file or registry path), the Migration
- OptionalComponentFailedToGetOCsFromPackage - D012E2A2-99D8-4A8C-BBB2-088B92083D78
- Indicates the optional component (OC) migration operation failed to enumerate optional components from an OC Package. Outputs the package name and error code.
- OptionalComponentOpenPackageFailed - 22952520-EC89-4FBD-94E0-B67DF88347F6
- Indicates the optional component migration operation failed to open an optional component Package. Outputs the package name and error code.
- OptionalComponentInitCBSSessionFailed - 63340812-9252-45F3-A0F2-B2A4CA5E9317
- Indicates corruption in the servicing stack on the down-level system. Outputs the error code encountered while trying to initialize the servicing component on the existing OS.
- DISMproviderFailure - D76EF86F-B3F8-433F-9EBF-B4411F8141F4
- Triggers when a DISM provider (plug-in) fails in a critical operation. Outputs the file (plug-in name), function called + error code, and error message from the provider.
- SysPrepLaunchModuleFailure - 7905655C-F295-45F7-8873-81D6F9149BFD
- Indicates a sysPrep plug-in has failed in a critical operation. Indicates the plug-in name, operation name and error code.
- UserProvidedDriverInjectionFailure - 2247C48A-7EE3-4037-AFAB-95B92DE1D980
- A driver provided to setup (via command line input) has failed in some way. Outputs the driver install function and error code.
- PlugInComplianceBlock - D912150B-1302-4860-91B5-527907D08960
- These are for server upgrades only, will output the compliance block and remediation required.
- PreReleaseWimMountDriverFound - 31EC76CC-27EC-4ADC-9869-66AABEDB56F0
- Captures failures due to having an unrecognized wimmount.sys driver registered on the system.
- WinSetupBootFilterFailure - C073BFC8-5810-4E19-B53B-4280B79E096C
- Detects failures in the kernel mode file operations.
- WimMountDriverIssue - 565B60DD-5403-4797-AE3E-BC5CB972FBAE
- Detects failures in WimMount.sys registration on the system.
- DISMImageSessionFailure - 61B7886B-10CD-4C98-A299-B987CB24A11C
- Captures failure information when DISM fails to start an image session successfully.
- FindEarlyDownlevelError - A4CE4FC9-5E10-4BB1-8ECE-3B29EB9D7C52
- Detects failures in down-level phase before setup platform is invoked.
- FindSPFatalError - A4028172-1B09-48F8-AD3B-86CDD7D55852
- Captures failure information when setup platform encounters a fatal error.
Release notes
08/08/2019 - SetupDiag v1.6.0.42 is released with 60 rules, as a standalone tool available from the Download Center.
- Log detection performance is improved. What used to take up to a minute should take around 10 seconds or less.
- Added Setup Operation and Setup Phase information to both the results log and the registry information.
- This is the last Operation and Phase that Setup was in when the failure occurred.
- Added detailed Setup Operation and Setup Phase information (and timing) to output log when /verbose is specified.
- Note, if the issue found is a compat block, no Setup Operation or Phase info exists yet and therefore won’t be available.
- Added more info to the Registry output.
- Detailed ‘FailureData’ info where available. Example: “AppName = MyBlockedApplication” or “DiskSpace = 6603” (in MB)
- “Key = Value” data specific to the failure found.
- Added ‘UpgradeStartTime’, ‘UpgradeEndTime’ and ‘UpgradeElapsedTime’
- Added ‘SetupDiagVersion’, ‘DateTime’ (to indicate when SetupDiag was executed on the system), ‘TargetOSVersion’, ‘HostOSVersion’ and more…
- Detailed ‘FailureData’ info where available. Example: “AppName = MyBlockedApplication” or “DiskSpace = 6603” (in MB)
06/19/2019 - SetupDiag v1.5.0.0 is released with 60 rules, as a standalone tool available from the Download Center.
- All date and time outputs are updated to localized format per user request.
- Added setup Operation and Phase information to /verbose log.
- Added last Setup Operation and last Setup Phase information to most rules where it make sense (see new output below).
- Performance improvement in searching setupact.logs to determine correct log to parse.
- Added SetupDiag version number to text report (xml and json always had it).
- Added "no match" reports for xml and json per user request.
- Formatted Json output for easy readability.
- Performance improvements when searching for setup logs; this should be much faster now.
- Added 7 new rules: PlugInComplianceBlock, PreReleaseWimMountDriverFound, WinSetupBootFilterFailure, WimMountDriverIssue, DISMImageSessionFailure, FindEarlyDownlevelError, and FindSPFatalError. See the Rules section above for more information.
- Diagnostic information is now output to the registry at HKLM\SYSTEM\Setup\MoSetup\Volatile\SetupDiag
- The /AddReg command was added to toggle registry output. This setting is off by default for offline mode, and on by default for online mode. The command has no effect for online mode and enables registry output for offline mode.
- This registry key is deleted as soon as SetupDiag is run a second time, and replaced with current data, so it’s always up to date.
- This registry key also gets deleted when a new update instance is invoked.
- For an example, see Sample registry key.
05/17/2019 - SetupDiag v1.4.1.0 is released with 53 rules, as a standalone tool available from the Download Center.
- This release dds the ability to find and diagnose reset and recovery failures (Push Button Reset).
12/18/2018 - SetupDiag v1.4.0.0 is released with 53 rules, as a standalone tool available from the Download Center.
- This release includes major improvements in rule processing performance: ~3x faster rule processing performance!
- The FindDownlevelFailure rule is up to 10x faster.
- New rules have been added to analyze failures upgrading to Windows 10 version 1809.
- A new help link is available for resolving servicing stack failures on the down-level OS when the rule match indicates this type of failure.
- Removed the need to specify /Mode parameter. Now if you specify /LogsPath, it automatically assumes offline mode.
- Some functional and output improvements were made for several rules.
07/16/2018 - SetupDiag v1.3.1 is released with 44 rules, as a standalone tool available from the Download Center.
- This release fixes a problem that can occur when running SetupDiag in online mode on a computer that produces a setupmem.dmp file, but does not have debugger binaries installed.
07/10/2018 - SetupDiag v1.30 is released with 44 rules, as a standalone tool available from the Download Center.
- Bug fix for an over-matched plug-in rule. The rule will now correctly match only critical (setup failure) plug-in issues.
- New feature: Ability to output logs in JSON and XML format.
- Use "/Format:xml" or "/Format:json" command line parameters to specify the new output format. See sample logs at the bottom of this topic.
- If the “/Format:xml” or “/Format:json” parameter is omitted, the log output format will default to text.
- New Feature: Where possible, specific instructions are now provided in rule output to repair the identified error. For example, instructions are provided to remediate known blocking issues such as uninstalling an incompatible app or freeing up space on the system drive.
- 3 new rules added: AdvancedInstallerFailed, MigrationAbortedDueToPluginFailure, DISMAddPackageFailed.
05/30/2018 - SetupDiag v1.20 is released with 41 rules, as a standalone tool available from the Download Center.
- Fixed a bug in device install failure detection in online mode.
- Changed SetupDiag to work without an instance of setupact.log. Previously, SetupDiag required at least one setupact.log to operate. This change enables the tool to analyze update failures that occur prior to calling SetupHost.
- Telemetry is refactored to only send the rule name and GUID (or “NoRuleMatched” if no rule is matched) and the Setup360 ReportId. This change assures data privacy during rule processing.
05/02/2018 - SetupDiag v1.10 is released with 34 rules, as a standalone tool available from the Download Center.
- A performance enhancement has been added to result in faster rule processing.
- Rules output now includes links to support articles, if applicable.
- SetupDiag now provides the path and name of files that it is processing.
- You can now run SetupDiag by simply clicking on it and then examining the output log file.
- An output log file is now always created, whether or not a rule was matched.
03/30/2018 - SetupDiag v1.00 is released with 26 rules, as a standalone tool available from the Download Center.
Sample logs
Text log sample
XML log sample
JSON log sample
Sample registry key
Related topics
Resolve Windows 10 upgrade errors: Technical information for IT Pros
What’s New in the Command and Conquer Red Alert 2 v1.00 serial key or number?
Screen Shot

System Requirements for Command and Conquer Red Alert 2 v1.00 serial key or number
- First, download the Command and Conquer Red Alert 2 v1.00 serial key or number
-
You can download its setup from given links:


