![Malware Hunter [1 January 2018] serial key or number](http://chimiephysique.ma/1ere/2014/12/dowloads.png?w=300&h=141)
Malware Hunter [1 January 2018] serial key or number
![Malware Hunter [1 January 2018] serial key or number Malware Hunter [1 January 2018] serial key or number](https://crackingpatching.com/wp-content/uploads/2018/08/Glarysoft-Malware-Hunter-1.64.0.647-Portable-Repack-CrackingPatching-1.jpg)
Malware Hunter [1 January 2018] serial key or number

Threat Hunting & Incident Response Summit & Training 2020 (September 2020)
- A Tale of Two Hunters - Practical Approaches for Building a Threat Hunting Program, Peter Ortiz.pdf
- Applying Fraud Detection Techniques to Hunt Adversaries, Nicole Hoffman.pdf
- Big Game Hunting - Major threat group joins the targeted ransomware-as-a-Service (RaaS) scene via a Valak partnership, John Dwyer, Christopher Kiefer.pdf
- Building a Hunting Program at a Global Scale, Pete Bryan.pdf
- Cybersecurity and the Platypus - Why Information Modeling is Essential, Yet Challenging, Jason Keirstead.pdf
- External Threat Hunters are Red Teamers, David Maynor, Jorge Orchilles.pdf
- From One Sec Guy to the Team That Saved the CISO's Day, Diego Mariano.pdf
- Hunting Human-Operated Ransomware Operators, Ryan Chapman.pdf
- Hunting Immaturity Model, Mangatas Tondang.pdf
- Hunting Powershell Obfuscation with Linear Regression, Joe Petroske.pdf
- Leveraging Beacon Detection Techniques to Identify Anomalous Logons, Fred Nolte, Nikita Jain, Dante Razo, Jacob Alongi.pdf
- Machine Learning Meets Regex Rule Engine, David Rodriguez.pdf
- New Tools for Your Threat Huntung Toolbox, Mark Baggett.pdf
- Open NDR and the Great Pendulum (Keynote), Greg Bell.pdf
- Raising the Tide - Driving Improvement in Security by Being a Good Human- Keynote, David J Bianco.pdf
- SaaS Hunting, Ben Johnson.pdf
- Started from the Bottom - Exploiting Data Sources to Uncover ATTCK Behaviors, Jose Rodriguez, Jamie Williams.pdf
- The SOC Puzzle - Where Does Threat Hunting Fit, Ashley Pearson.pdf
- WinSCP - Yeah You Know Me, Mari DeGrazia.pdf
Security Awareness Forum & Training (August 2020)
- 28 Common Attitudes and Behaviors - Racial Literacy Resource, Joey Oteng.pdf
- A Step-by-Step Guide to Engaging a Global Workforce with Podcasts, Paige Ishii.pdf
- Create Your Own Awareness Videos at Home, Kerry Tomlinson.pdf
- Diversity, Equity, Inclusion, & Justice in Cyber - Action Items and Resources.pdf
- Diversity, Equity, Inclusion, & Justice in Cyber- Schilling, Otengo, Selemani, Stewart.pdf
- General Info and Reference Slides.pdf
- How to Build a Global Digital Security Awareness Scavenger Hunt, Neaka Lynn Balloge.pdf
- How to Engage Globally with Podcasts, Paige Ishii.pdf
- Keynote - The Human Side of Threats, Katie Nickels.pdf
- SANS Scavenger Hunt Clues and Answers.pdf
- Social Justice 101 - Joey Oteng.pdf
- stop action video tipsheet - Kerry Tomlinson.pdf
DFIR Summit & Training 2020 (July 2020)
- Accelerate Your Threat Hunting and IR with Next-Gen NDR+EDR, Balaji Prasad, Arun Raman, Heike Ritter.pdf
- capa - Automatically Identify Malware Capabilities, Willi Ballenthin, Moritz Raabe.pdf
- Captain's Log - Take Your Application Log Analysis from Starfleet to Star Fleek, David Pany, Ryan Tomcik.pdf
- Completing the Triad - The Case for Leading with NDR, John Smith.pdf
- CyberSleuth - Education and Immersion for the Next Generation, Daryl Pfief.pdf
- Data Science for DFIR - The Force Awakens, Jess Garcia.pdf
- Did I Do That- Understanding Action and Artifacts in Real Time, David Cowen, Matthew Seyer.pdf
- Dig Deeper - Acquisition and Analysis of AWS Cloud Data, Trey Amick, Curtis Mutter.pdf
- Empowering DFIR Through Automation and Orchestration - Enhancing Your Artifacts with Threat Intelligence, Iain Davison.pdf
- Forensic Analysis of the Apple HomePod and the Apple HomeKit Environment, Mattia Epifani.pdf
- Forensic Marriage - The Love-Hate Relationship Between eDiscovery and DFIR, Andrew + Sarah Konunchuk.pdf
- From Threat Detection to Organizational Threat Detection, O'Shea Bowens, Nico Smith.pdf
- Healthy Android Exams - Timelining Digitial Wellbeeing Data, Alexis Brignoni, Joshua Hickman.pdf
- Help, We Need an Adult, Liz Waddell.pdf
- How Not to Ruin Your Day - Avoiding Common Threat Huntung Mistakes, Menachem Perlman.pdf
- Hunting Bad Guys That Use TOR in Real-Time, Milind Bhargava.pdf
- If At First You Don't Succeed, Try Something Else, Jim Clausing.pdf
- Just Forensics - Mercifully, Lee Whitfield.pdf
- Kansa for Enterprise Scale Threat Hunting, Jonathan Ketchum.pdf
- Keynote - Strengthening Trust in DFIR, Eoghan Casey, Daryl Pfeif.pdf
- Long Live Linux Forensics, Ali Hadi, Brendan Brown, Victor Griswold.pdf
- Lucky (iOS) #13 - Time to Press Your Bets, Jared Barnhart.pdf
- Making Memories - Using Memory Analysis for Faster Response to User Investigations, Jessica Hyde, Aaron Sparling.pdf
- Man in The Mirror - Upping Your Threat Hunting Game by Seeing Yourself as an Attacker, Eric McIntyre, Randori.pdf
- Profiling Threat Actors in DNS, Taylor Wilkes-Pierce.pdf
- Putting Big Data to Work in DFIR, Jason Mical.pdf
- Think Like a Threat Actor to Handle Remote Work Risks, Brandon Hoffman, NetEnrich Lunch.pdf
- Using Big DFIR Data in Autopsy and Other Tools, Brian Carrier.pdf
- Using Storytelling to Be Heard and Remembered, Frank McClain.pdf
- What the DLL is Happening - A Practical Approach to Identifying SOH, Frank McClain.pdf
- You Need a PROcess to Check Your Running Processes and Modules, Michael Gough.pdf
Pen Test HackFest & Cyber Ranges Summit (June 2020)
- Anatomy of a Gopher - Binary Analysis of Go Binaries, Alex Useche.pdf
- Assumed Breach - The Better Pen Test, Tim Medin.pdf
- Automated Detection of Software Vulnerabilities Using Deep Learning, Nidhi Rastogi.pdf
- Building Compelling Cyber Challenges and Range Scenarios, Chris Elgee, Simon McNamee.pdf
- Creating Simulations for Historical Data Collection I, Tim Conway.pdf
- Creating Simulations for Historical Data Collection II, Phil Hagen.pdf
- Emulating the Adversary in Post-Exploitation, Jake Williams.pdf
- Fully Functional Cloud C2, Chris Truncer.pdf
- Getting tthe Most Out of Free CtFs, Derek Rook.pdf
- Handling Advanced Threats - De-Obfuscation, Emulation, and Anti-Forensics, Alexandre Borges.pdf
- Handling Advanced Threats - Extended Version, Alexandre Borges.pdf
- Hardware Hacking - Intro to Programming Micro Controllers, Mick Douglas.pdf
- How You Can Use Your Offensive Skills to Help the Air Force, Capt. Lillian Warner.pdf
- Identifying Novel Malware at Scale, Pedram Amini.pdf
- Keynote - Opportunity Amidst Uncertainty - Spinning Up Virtual Cons on a Shoestring, Lesley Carhart.pdf
- Keynote - Using CTF Challenges to Massively Level-Up Your Cybersecurity Career, Ed Skoudis.pdf
- Let the Games Begin- Overview of Summit Challenges and Jupiter Rockets, Steve Sims, Ed Skoudis, Simon Vernon.pdf
- Maldocs - Tips for Red Teamers, Didier Stevens.pdf
- Open Source Election Security - End-to-End Verifiable Voting with Microsoft ElectionGuard, Ethan Chumley, Matthew Wilhelm.pdf
- Quickstart Guide to MITRE ATT&CK, Adam Mashinchi .pdf
- Some of Them Want to Use You; Some of Them Want to Get Used By You, Chris Wysopal.pdf
- Supercharge Your Red Team with RedELK, Marc Smeets.pdf
- Where the ---- Is My Identity, Chris Edmundson.pdf
- Windows 10 Kernel Mitigations and Exploitation, Jaime Geiger, Stephen Sims.pdf
Cloud Security Summit & Training 2020 (May 2020)
- Building a Pipeline for Secure Virtual Machines in AWS, Shaun McCullough.pdf
- Cloud Breaches - Case Studies, Best Practices, and Pitfalls - Dylan Marcoux, Christopher Romano.pdf
- Cloud Security Posture Management from Security Hygiene to Incident Response, Yuri Diogenes, Jess Huber, Ricardo Bruno.pdf
- Cloud Security to Go, Ken Hartman.pdf
- Cover Your SaaS - Practical SaaS Security Tips, Ben Johnson.pdf
- Doing Cloud in China, Kenneth G. Hartman.pdf
- Don't Just Lift and Shift - Why Traditional Controls Don't Always Apply to the Cloud and What You Can Do About It, Steve Turner.pdf
- Keynote - Lessons Learned from Cloud Security Incidents Past and Present, Dave Shackleford.pdf
- Keynote - Securing Cloud Deployments - A Red Team Perspective, Matt Burrough.pdf
- Leveling Up Your Workforce for Cloud Enablement - Pathways to Total Pwnage, Aaron Lancaster.pdf
- Modern Identity Strategies to Securely Manage Your Cloud Infrastructure, Michael Soule.pdf
- Multi-Cloud Visibility for Large Organizations, Chris Farris.pdf
- Put a Lid on Those AWS S3 Buckets, Lily Lee & Melisa Napoles.pdf
- Reimagining Vulnerability Management in the Cloud, Eric Zielinski.pdf
- Static Analysis of Infrastructure as Code, Barak Schoster Goihman.pdf
- Threat Hunting in the Microsoft Cloud - The Times They Are a-Changin', John Stoner.pdf
ICS Security Summit & Training 2020 (March 2020)
Blue Team Summit & Training 2020 (March 2020)
Open-Source Intelligence Summit & Training 2020 (February 2020)
Cyber Threat Intelligence Summit & Training 2020 (January 2020)
SANS Threat Hunting & IR Europe Summit & Training 2020 (January 2020)
SANS Cyber Threat Summit 2019 (November 2019)
Pen Test HackFest Summit & Training 2019 (November 2019)
European Security Awareness Summit 2019 (November 2019)
Cloud & DevOps Security Summit & Training 2019 (November 2019)
Purple Team Summit & Training 2019 (October 2019)
SIEM Summit & Training 2019 (October 2019)
SANS DFIR Europe Summit & Training 2019 - Prague Edition (September 2019)
Threat Hunting & Incident Response Summit & Training 2019 (September 2019)
Oil & Gas Cybersecurity Summit & Training 2019 (September 2019)
Supply Chain Cybersecurity Summit & Training 2019 (August 2019)
Security Awareness Summit & Training 2019 (August 2019)
Malware Hunter Pro License Key Free Activation Code 2019
Do you need Malware Hunter Pro License Key for free? you are the right place here. Just Visit a Giveaway page and Get Malware Hunter Pro Free Activation Code 2019 free download full version. Let’s Know about the software review first. Everybody wants to keep their PC safe from any type of stubborn Malware or Viruses. Because of a single Malware or Virus can create enough trouble for you. So there shouldn`t be any consideration when it will come about your PC protection which contains your lots of important data. Now the good news for you is what I am about to tell you now is about an amazing software which will not only give you malware protection but also from viruses also.

It’s a product from Glarysoft company which we have known as Malware Hunter.
Why Malware Hunter to Get Rid of Malware?
It`s the most reliable name for you when you are aware of your PC protection. With a faster scanning process Malware Hunter is designed to detect and clean out all the stubborn Malware from your PC along with Viruses. This will ensure the highest protection for your PC.
How does it work to Protect or Remove from Malware and Adware?
Whenever you are having this on your PC you have nothing to worry. Malware Hunter will take care of all of the Malware and Viruses with its 3-way scanning process like Quick, Full and Custom. All the process are quick enough so your precious and important time doesn`t kill. These scans will utilize Glarysoft cloud but you can also enable Avira Antivir engine. Though if you are using any other security software this application will not get the conflict with them.
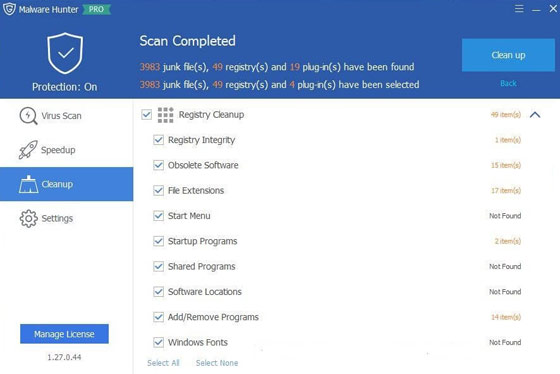
It has been designed with some great features like:
1. Hyper scanning process with which you can enjoy faster scanning speed.
2. Detect and remove stubborn malware and against any potential danger.
3. This award-winning product will ensure your security along with secures your important data, protects your privacy. Read Also: Keep your Privacy Safe with Best Free Adware Remover 2019.
4. Ensure you a Virus-free PC experience.
5. Enabling the Avira Antivir engine.
6. Automatic updates will make you safe from new threats.
7. It can also clean junks and boost your PC performance and can optimize startup items.
Malware Hunter Pro 2019 Supported Windows OS:
- Windows 7 (32 bit and 64-bit windows)
- Windows 10 (64 bit and 32-bit windows)
- Windows 8/8.1 (32 bit and 64-bit windows)
- Windows XP / Vista
If you are looking for some well-featured security software which can take down Malware and Viruses both at the same time then trust me this software is for you. Get Also: AVG Internet Security 2019 License key Free for 1 Year.
How to get Malware Hunter Pro License Key Free Activation Code 2019:
Now you can have this amazing software on just $25.00 for a 1-year serial key for 3 PCs but from here you can get all this feature at just free. Want to know how? You just simply have to follow some simple steps below.
Use this below activation code:
Email: aa@a.com
License Key : 361A1D-053439-022A67-43BFE2-DF23BA
or,
1. Just go on one of this giveaway link shown below:
Giveaway Page 1
Giveaway Page 2
2.
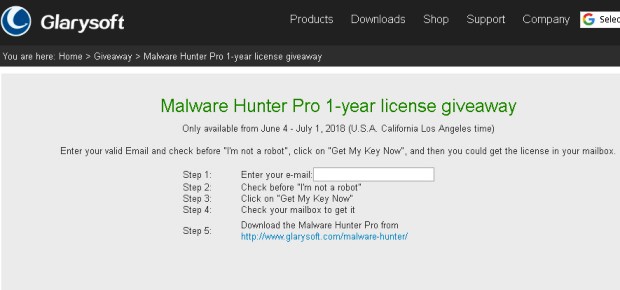
3. After that, you have to click on ‘Get My New Key’.
4. Then check your e-mail you will find a confirmation link from Glarysoft.
5. Just click on that mail and create an account after that just log in to your account and you will find there your own Malware Hunter Pro key.
6. You can have your full set up file from us too by clicking below link.
7. Malware Hunter Pro download here
After that install, run and put your Malware Hunter Pro license key to activate it then sits back and relax and get the best safe and secure PC experience. You don’t need any or serial number to full feathers enable with this spyware removal software. Just use those giveaway trick to get full version gratis to enjoy malware free windows 10. If you want to get more full version anti-malware and antivirus or PC security software, Then you need to visit here: https://besttechadvise.com. This website is best for the free software giveaway, free internet security software, pc cleanup tools and many more. Hope you can download free PC applications with activation key from this website.
STOP Ransomware (.STOP, .Puma, .Djvu, .Promo, .Drume) Help & Support Topic
This topic is the primary support topic for assistance with STOP (DJVU) Ransomware. It includes an updated summary of this infection, it's variants and possible decryption solutions with instructions.
Any files that are encrypted with older STOP (DJVU) Ransomware variants will have the .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, .shadow, .djvu, .djvuu, .udjvu, .djvuq, .uudjvu, .djvus, .djvur, .djvut.pdff, .tro, .tfude, .tfudeq, .tfudet, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promock, .promoks, .promorad,, promorad2, .kroput, .kroput1, .charck, .pulsar1, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .verasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan,.sarut, .fedasot, .forasom, .berost, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidon, .heroset, .myskle, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .tocue, .darus, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato. .masodas, .stare, .cetori or .carote extension appended to the end of the encrypted data filename as explained here by Amigo-A (Andrew Ivanov).
Any files that are encrypted with newer STOP (DJVU) Ransomware variants after August 2019 will have the .coharos, .shariz, .gero, .hese, .xoza, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .noos, .kuub, .reco, .bora, .leto, .nols, .werd, .coot, .derp, .nakw, .meka, .toec, .mosk, .lokf, .peet, .grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .mkos, .nbes, .piny, .redl, .nosu, .kodc, .reha, .topi, .npsg,.btos,.repp, .alka, .bboo, .rooe, .mmnn, .ooss, .mool, .nppp, .rezm, .lokd, .foop, .remk, .npsk, .opqz, .mado,.jope, .mpaj, .lalo, .lezp, .qewe,.mpal, .sqpc,.mzlq, .koti, .covm, .pezi, .zipe, .nlah,.kkll, .zwer .nypd, .usam, .tabe, .vawe, .moba, .pykw,.zida,.maas, .repl, .kuus, .erif, .kook, .nile, .oonn,.vari, .boop, .geno,.kasp,.ogdo,.npph or .kolz extension appended to the end of the encrypted data filename as explained here by Amigo-A (Andrew Ivanov). Since switching to the new STOP Djvu variants (and the release of .gero) the malware developers have been consistent on using 4-letter extensions.
STOP Ransomware will leave files (ransom notes) named !!!YourDataRestore!!!.txt, !!!RestoreProcess!!!.txt, !!!INFO_RESTORE!!!.txt, !!RESTORE!!!.txt, !!!!RESTORE_FILES!!!.txt, !!!DATA_RESTORE!!!.txt, !!!RESTORE_DATA!!!.txt, !!!KEYPASS_DECRYPTION_INFO!!!.txt, !!!WHY_MY_FILES_NOT_OPEN!!!.txt, !!!SAVE_FILES_INFO!!!.txt and !readme.txt. The .djvu* and newer variants will leave ransom notes named_openme.txt, _open_.txt or _readme.txt
***IMPORTANT:@ ALL VICTIMS....
STOP Djvu Ransomware has two versions.
1. Old Version: Most older extensions, starting with .djvu (v013) up to .carote (v154)...decryption for most of these versions was previously supported by STOPDecrypter if infected with an OFFLINE KEY (and a few ONLINE KEYS). That same support has been incorporated into the new Emsisoft Decryptor/submission method for these old Djvu variants...the decrypter will only decrypt your files without submitting file pairs if you have an OFFLINE KEY.
2. New Version: The newest extensions released around the end of August 2019 AFTER the criminals made changes....starting with .coharos (v146) were never supported by STOPDecrypter. However, OFFLINE KEYS for some newer variants have been obtained by Emsisoft and uploaded to their server. This is possible after a victim pays the ransom, receives a key from the criminals and shares that key with the Emsisoft Team..ONLINE KEYS are UNIQUE for each victim and randomly generated in a secure manner so they too were never supported by the decryptor.
As a result of the changes made by the criminals, STOPDecrypter is no longer supported...it has been discontinued AND replaced with the Emsisoft Decryptor for STOP Djvu Ransomware developed by Emsisoft and Demonslay335 (Michael Gillespie).
Going forward, EVERYONE should be using the Emsisoft Decryptor.
STOP Ransomware Decryptor (released for 148 variants) <- Be sure to READ the INSTRUCTIONS in this article
A decryptor for the STOP Ransomware has been released by Emsisoft and Michael Gillespie that allows you to decrypt files encrypted by 148 variants of the infection for free....anyone who was infected after August 2019 cannot be helped with this service. With that said, it may be possible to decrypt using an offline key, so even with these variants there may be some success.
Emsisoft does not announce when keys are recovereddue to victim confidentiality so that means victims must keep reading this support topic for updates or run the decryptor on a test sample of encrypted files every week or so to check if new variants can be decrypted...scroll down to see the UPDATED LIST under the section ABOUT ONLINE & OFFLINE IDS / KEYS.
---------------------------------------------------------------------------------------------------------------------------------------------------------------
USING EMSISOFT DECRYPTOR FOR STOP DJVU RANSOMWARE:
Emsisoft Decryptor for STOP Djvu<- official authorized download link
Emsisoft Decryptor for STOP Djvu alternate download
There are limitations on what files can be decrypted. For all versions of STOP Djvu, files can be successfully decrypted if they were encrypted by an offline key that we have. For Old Djvu, files can also be decrypted using encrypted/original file pairs submitted to the STOP Djvu Submission portal; this does not apply to New Djvu after August 2019.
If you were infected after August 2019, then you are encrypted with a new version. In order to decrypt any of these new versions an OFFLINE KEY with corresponding private key is required. If an OFFLINE KEY is obtained, it will be pushed to the server and automatically added to the decryptor. As such, you should download the decryptor to see if Emsisoft has been able to gain access to an OFFLINE KEY which can decrypt your files. The Emsisoft decryptor requires a working Internet connection so make sure you are connected before running it.
If you are infected with the .puma, .pumas, .pumax or .INFOWAIT, .DATAWAIT extensions of the earlier STOP Ransomware variants, you should download and use the Emsisoft Decryptor for STOP Puma. The older .puma based variants used XOR encryption and these extensions can be decrypted by providing a single encrypted and original file pair over 150KB.
Note: Dr.Web may be able to help with other earlier UPPERCASE variants as noted here by Emmanuel_ADC-Soft.
There is also a Media-Repair...Small repair tool for MP3 and WAV files affected by STOP (Djvu). Instructions and documentation are provided here.
Emsisoft STOP Djvu Decryption Service
In order to decrypt some of your files, we need some encrypted files and their originals.
Specifically, these file pairs need to meet the following requirements:
- Must be the same file before and after encryption[1]
- Must be a different file pair per file type you wish to decrypt[2]
- Must be at least 150KB
Notice: this service does not support the "New" variants that use RSA encryption.
If your files were encrypted after August 2019, chances are it is the "New" version
Again, the decryptor can only decrypt files with the same first 5 bytes as what you submitted and you have to supply a file pair for each format you want to decrypt. A single file pair means an encrypted file AND a copy of its exact unencrypted original file (same size). Everyone can always find a clean unencrypted copy of an original file that was encrypted for a file pair in order to reconstruct/extrapolate the encryption keys.
- Files you downloaded from the Internet that were encrypted and you can download again to get the original.
- Pictures that you shared with family and friends that they can just send back to you.
- Pictures you uploaded on social media or cloud services like Carbonite, OneDrive, iDrive, Google Drive, etc)
- Attachments in emails you sent or received and saved.
- Files on an older computer, flash drive, external drive, camera memory card or iphone where you transfered data to the infected computer.
- Default or sample wallpapers and pictures that were shipped with your Windows version which you can get from another system running the same Windows version.
For more information, please read the Frequent Questions at the bottom of STOP Djvu Decryption Service page.
---------------------------------------------------------------------------------------------------------------------------------------------------------------
ABOUT ONLINE & OFFLINE IDS / KEYS:
Emsisoft Decryptor supports and will only attempt to decrypt files if they were encrypted by one of the known STOP (Djvu) OFFLINE KEY's and some ONLINE ID's if a proper file pair is supplied to the submission form as explained here by GT500. For newer STOP (Djvu) variants, the criminals switched to a new cryptographically strong key protected by RSA Salsa20 algorithm. Every file is generated securely with a new key using UuidCreate (which internally uses CryptGenRandom) that cannot be brute-forced. The encryption is the exact same regardless of whether it is an ONLINE or OFFLINE KEY which encrypted your files.
If the malware is able to connect (communicate) with its command and control servers it will obtain and use a unique randomly generated ONLINE KEY. Without the master private RSA key that can be used to decrypt your files, decryption is impossible...the key is generated in a secure way that cannot be brute-forced. The public RSA key alone that encrypted the files is useless for decryption, therefore a malware sample of any particular variant is also useless for decryption since it on;y contains the public key. We cannot help decrypt files encrypted with the ONLINE KEY due to the type of encryption used by the criminals.
If the malware is unable to connect (communicate) with its servers and fails to get an ONLINE KEY it will give up and resort to using an OFFLINE KEY. The OFFLINE KEY is a hard-coded built-in encryption KEY (used with a built-in OFFLINE ID) at the time the ransomware encrypted your files.Each variant extension only has one OFFLINE ID (a string of numbers and letters that identifies the infected computer to the ransomware) which generallyends in"t1" so they are usually easy to identify. Since the OFFLINE KEY and ID only change with each variant/extension, everyone who has had their files encrypted by the same variant will have the same ID and the files will be decryptable by the same key (or "private key" in the case of RSA encryption) as explained by GT500 in the Emsisoft STOP/Djvu Decryptor FAQs.
- Decryption of new STOP (Djvu) variants is possible IF infected with the OFFLINE ID using the Emsisoft Decryptor only after obtaining and sharing the corresponding private OFFLINE KEY from victims who paid the ransom for a specific variant. OFFLINE KEYS will work for ALL victims who were encrypted by the same key. If there is no OFFLINE KEY available for any specific variant, then your files cannot be decrypted at this time. We have no way of knowing when or if an OFFLINE KEY will be recovered and shared with Emsisoft.
- Decryption of new STOP (Djvu) variants is impossible IF infected by an ONLINE KEY without paying the criminals for that victim’s specific private key...these keys are unique for each victim and randomly generated in a secure manner. Since ONLINE KEYS are unique and random for each victim, they cannot be shared or re-used by other victims. Although support for most of the OFFLINE ID's (and a few ONLINE KEYS) for older STOP (Djvu) versions was added to the Emsisoft Decryptor, no ONLINE ID's are supported for new STOP (Djvu) versions.
Per the Emsisoft STOP/Djvu Decryptor FAQs:
New Variants....As for online ID's, due to the new form of encryption, there's currently nothing the decrypter can do to help recover files.
Will it ever be possible to decrypt new variants with online ID's? That depends on whether or not law enforcement is able to catch the criminals who are behind this ransomware. If law enforcement is able to catch them and release their database of keys, then we can add those to our database for decryption... The more reports law enforcement agencies receive, the more motivation they have to track down the criminals.
The decrypter can't decrypt my files? In most cases this means you have an online ID. It could also mean your files were encrypted by a newer variant of STOP/Djvu...
Some victims may have files encrypted by both an OFFLINE KEY and an ONLINE KEYdue to the malware running multiple times and making repeated attempts to get an ONLINE KEY, sometimes successfully communicating with the command and control server, sometimes failing to communicate and resorting to using an OFFLINE KEY. In such scenarios the Emsisoft Decryptor will skip any files encrypted by the ONLINE KEY since they cannot be decrypted.
There no longer is an easy method to get OFFLINE KEYS for many of these newer variants and no way to decrypt files if infected with an ONLINE KEY without paying the ransom and obtaining the private keys from the criminals who created the ransomware. Emsisoft can only get OFFLINE KEYS AFTER a victim has PAID the ransom, receives a key and provides it to them. This meansif infected with an ONLINE KEY, we cannot help you decrypt your files since there is no way to gain access to the criminal's command server and retrieve this KEY.
Updated List: Emsisoft has obtained and uploaded to their server OFFLINE KEYS for the following new STOP (Djvu) variants....gero, .hese, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .noos, .kuub, .reco, .bora, .nols, .werd, .coot, .derp, .meka, .toec, .mosk, .lokf, .peet, .grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .mkos, .nbes, .nosu, .reha, .topi, .repp, .alka, .nppp, .remk, .npsk, .opqz, .mado, .covm, .usam, .tabe, .vawe, .maas, .nile, .geno as noted in Post #9297 and elsewhere in the support topic.
** If there is no OFFLINE KEY for the variant you are dealing with OR if it is one of the newer STOP (Djvu) variants which used an ONLINE KEY, we cannot help you unless an OFFLINE KEY is retrieved and added to the Emsisoft server / decryptor.
If you run the Emsisoft Decryptor for a new variant with an OFFLINE ID which has not been recovered, the decrypter will indicate the following "error" under the Results Tab.
Error: No key for New Variant offline ID: ***************************t1 For now, the only other alternative to paying the ransom, is to backup/save your encrypted data as is and wait for possible future recovery of an OFFLINE KEY.
** If an OFFLINE KEY is available for the variant you are dealing with and your files were not decrypted by Emsisoft Decryptor, then you most likely were encrypted by an ONLINE KEY and those files are not recoverable since they are not decryptable unless you pay the ransom to the criminals. ONLINE ID's for new STOP (Djvu) variants are not supportedby the Emsisoft Decryptor.
If you run the Emsisoft Decryptor for a new variant with an ONLINE ID, the decryptor will indicate there is "no key" under the Results Tab and note it is impossible to decrypt.
No key for New Variant online ID *************************** Notice: this ID appears to be an online ID. decryption is impossibleThere are a few older STOP (DJVU) variants which are not decryptable. The Emsisoft decrypter is able to identify Old Variant IDs which it is unable to decrypt and note that under the Results Tab just as it does with new STOP (DJVU) variants which are not decryptable.
Unable to decrypt Old Variant ID: *************************** First 5 bytes: *************Emsisoft Decryptor does not need to be updated unless a bug (glitch) is discovered. Any new OFFLINE KEYS found will be be pushed to the server and automatically pulled down by the decryptor. There is no timetable for when or if an OFFLINE KEY will be recovered and shared with Emsisoft and no announcement when they are recovered. Victims should run the decryptor on a test sample of encrypted files every week or so to check if new variants can be decrypted.
Why Emsisoft Decrypter will not run. Your .NET Framework is outdated or corrupted. Per the FAQs.
Why won't the decrypter run? The decrypter requires version 4.5.2 or newer of the Microsoft .NET Framework, so this could mean your version of the .NET Framework is out of date. We recommend installing the latest version of the .NET Framework - 4.8 at the time of writing this - and then trying the decrypter again.
Why is the decrypter stuck on "Starting"?. Per the FAQs
When you run the decrypter, it looks for encrypted files. It will say "Starting" until it is able to find some. If the decrypter remains stuck on "Starting" for a long period of time, then this means it is unable to find any encrypted files
What does "Remote name could not be resolved" mean? Per the FAQs
It's an indication of a DNS issue. Our first recommendation is to reset your HOSTS file back to default. Microsoft has an article about this at the following link:
https://support.microsoft.com/en-us/help/972034/how-to-reset-the-hosts-file-back-to-the-default
While running Emsisoft Decryptor, victims may notice their files are briefly visible with their original extension but then revert to their encrypted state. This is by design...the decryptor prepares a copy of the encrypted file without the encrypted extension in order to safely work on it. The decryptor then checks for a key or keystream from the server, and if it fails, the decryptor reverts and deletes the copy it just made in order to clean up after itself as explained here
While running Emsisoft Decryptor, an "1nvalid file pair; "encrypted" file is not encrypted" occurs when the file you put in the "Encrypted file" field is missing the filemarker - this means either the malware didn't encrypt it at all, or it bugged out during the encryption as explained here.
While running Emsisoft Decryptor, an "Error: The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel" occurs - this means that your computer doesn't support TLS 1.2 as explained here.
.
OTHER IMPORTANT INFORMATION:
- Beware ofZorab Fake STOP Djvu ransomware decryptor double-encrypts desperate victims' files
...The creators of the Zorab ransomware have released a fake STOP Djvu decryptor that does not recover any files for free but instead encrypts all of the victim's already encrypted data with another ransomware.
- STOP (Djvu) Ransomware only encrypts the first150 KBof files.
- All of the new STOP (Djvu) variants add334 bytesto encrypted file size due to including the RSA-encrypted key, the ID and filemarker as explained here.
- Newer STOP (Djvu) Ransomware variants are known to cause dual (multiple) encryptions with more than one variantbecause he ransomware is loaded as a Scheduled Task and sets itself to run every 5 minutes.
- Newer STOP (Djvu) Ransomware variants and other ransomwares have been reported to spread by downloading & using adware bundles, pirated software, activators for Office and Windows, cracks. and shady sites.
- Newer STOP (Djvu) Ransomware variants are also installing Password Stealing Trojans.
In addition to encrypting a victim's files, the STOP ransomware family has also started to install the Azorult password-stealing Trojan on victim's computer to steal account credentials, cryptocurrency wallets, desktop files, and more...Victims who have been infected with a STOP Ransomware variant should immediately change the passwords to any online accounts that are used, especially ones that are saved in the browser. Victims should also change passwordsin software such as Skype, Steam, Telegram, and FTP Clients. Finally, victims should check any files stored on the Windows desktop for private information that may now be in the hands of the attackers.
It is imperative that you change all passwords for your computer to include those used for banking, taxes, email, eBay, paypal and any online activities which require a username and password. You should consider them to be compromised and change passwords from a clean computer as a precaution, not the infected one.
WARNING NOTE: Please DO NOT use or share download links for decrypter_2.exe. This was the shoddy decrypter written by the criminals which victims were using as a LAST RESORT. With the release of Emsisoft's decryptor. there is no need for victims to use this use this decrypter any more...the Emsisoft decryptor does everything it can do and more safely. All the download links for decrypter_2.exe have been removed and if anyone posts a new download link, that too will be removed.
.
.
Windows Insider MVP 2017-2020
Microsoft MVP Reconnect 2016
Microsoft MVP Consumer Security 2007-2015
Member ofUNITE, Unified Network of Instructors and Trusted Eliminators
If I have been helpful & you'd like to consider a donation, click
What’s New in the Malware Hunter [1 January 2018] serial key or number?
Screen Shot

System Requirements for Malware Hunter [1 January 2018] serial key or number
- First, download the Malware Hunter [1 January 2018] serial key or number
-
You can download its setup from given links:


