CC Software Access Password Recover 2.00 serial key or number

CC Software Access Password Recover 2.00 serial key or number
Alesis Vortex Wireless 2 - Frequently Asked Questions
 It's time to experience unprecedented keytar performance with the Alesis Vortex Wireless 2. The Vortex Wireless 2 eliminates the barrier between you and your audience by giving you the freedom to move around the stage and take the lead without being connected to any cables. This article walks through a number of frequently asked questions about the Alesis Vortex Wireless 2.
It's time to experience unprecedented keytar performance with the Alesis Vortex Wireless 2. The Vortex Wireless 2 eliminates the barrier between you and your audience by giving you the freedom to move around the stage and take the lead without being connected to any cables. This article walks through a number of frequently asked questions about the Alesis Vortex Wireless 2.
Frequently Asked Questions
Do I need a computer to use the Vortex Wireless 2?
The Vortex Wireless 2 will require either a computer with accompanying software* or a sound module (such as the M-Audio Accent module) in order to generate any sound. The keyboard will send MIDI messages wirelessly to the included USB receiver and/or to the 5-pin MIDI out port which will trigger sound in the connected software or sound module.
* The Vortex Wireless 2 includes the Ableton Live Lite software and several plugins to help you get started.
Does the Vortex Wireless 2 require any drivers?
No, the Vortex Wireless 2 is class-compliant and does not require any drivers for use with Mac and Windows operating systems.
What are the main differences between the Vortex Wireless and the Vortex Wireless 2?
The Vortex Wireless 2 shares a lot of the popular features from the original Vortex Wireless like the glossy black finish, MIDI-assignable accelerometer (tilt) and touchstrip ribbon controller, thumb controlled volume slider and pitch-bend wheel on the neck, and more. Expanding on the original, the eight velocity-sensitive drum pads now have assignable RGB backlighting, and the three assignable knobs have been upgraded to eight backlit, MIDI-assignable faders to give you more wireless control over your sound.
The Vortex Wireless 2 also includes a brand new software package so you can get to making music right out of the box.
What is included in the box?
- Vortex Wireless 2
- USB Wireless Reciever
- USB Cable
- Strap
- Cable Harness
- Software Download Card (For Ableton Live Lite)
- User Guide
- Safety & Warranty Manual
Does the Vortex Wireless 2 come with any software?
The Vortex Wireless 2 comes with the following software:
All software (with the exception of Ableton Live Lite) will be available from the user account page once the Vortex Wireless 2 has been registered. See the questions below for more information about accessing the software:
How do I get the software that is included?
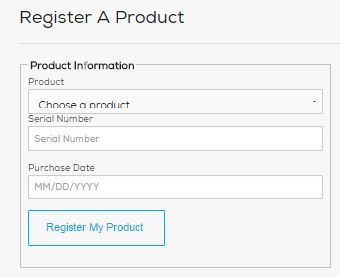
Most of the available software for the Vortex Wireless 2 will be provided after registration of the product into your user account on the Alesis website. You will be required to enter your serial number and then a link will be provided.
- Go to https://alesis.com/account/signin/
- If you have an account; input your Email Address, Password and select the bottom Login to your Alesis account. If you do not have an account, Create one.
- Once you have logged in or created your Alesis user account, choose Register Product.
- Enter the requested information to register your Vortex Wireless 2 and press Register My Product. Note: Include all the characters for the serial number including (21) and Purchase of Date by MM/DD/YYYY format.
- Once you have registered your Vortex Wireless 2, you can now find the downloads for the software within the My Products section.
How do I Install Ableton Live Lite?
A software download card for Ableton Live Lite is included in the box with your Vortex Wireless 2. Here you will find a download link and authorization code to activate the software. Follow our video below for a complete walkthrough.
How do I power the Vortex Wireless 2?
The Vortex Wireless 2 can powered by (4) AA Batteries (batteries not included) or via USB cable. Use the power switch on the bottom (near the USB port) to power the keyboard on/off and select its power source.
What are the faders for?
You can use these faders to send MIDI CC messages to your software. You can set the range and CC message number—and the direction (“polarity”) of the fader—in the editor software found in your user account after registration.
Is the wireless capability the same as the original Vortex Wireless?
Yes! The Vortex Wireless 2 comes with a USB dongle allowing for easy wireless USB MIDI connection, just like the original Vortex Wireless. Simply connect the USB dongle to your computer, and then power on the Vortex Wireless 2, using (4) AA batteries (batteries not included). The USB receiver is always “paired” (wirelessly connected) to your Vortex Wireless 2, so no further steps are required.
Can I use the Vortex Wireless 2 wirelessly with an external sound module?
Yes, the Vortex Wireless can be connected to most external sound modules by using the included USB receiver or the 5-pin MIDI out port. If your external sound module has a USB port for the use of MIDI controllers, the Vortex Wireless 2 will work. If it does not, you can also use the 5-pin MIDI DIN port on the bottom of the Vortex Wireless 2 to connect directly to your external sound module.
What are Ribbon Banks?
The ribbon controller can store three different types of MIDI messages to be recalled by pressing one of the three Ribbon Bank buttons. This means that you can assign three different functions to the ribbon controller per preset and easily switch between them on the fly. All parameters can be set using the included software editor.
Can I set the range of the tilt and ribbon controller?
Yes, the software editor can be used to assign the range of the tilt and ribbon controllers, as well as assign MIDI type, CC, note, channel, and more.
Does the Vortex Wireless 2 have a factory reset?
To restore the default settings, press and hold the lowest C and Gb keys on the keyboard and use the power switch to power it on. This will erase all of the settings stored on your Vortex Wireless 2.
If I lose the wireless receiver, can it be replaced?
Yes, a new wireless receiver can be paired with your Vortex Wireless 2 using the software editor. In the software editor, go to File > Update USB Receiver Pairing and follow the instructions to enter the last 6-digits of the serial number on the wireless receiver to re-pair.
To obtain a replacement wireless receiver, please contact your nearest Alesis support office.
Further Technical Support
Whether you are a customer or dealer, if you already own an Alesis product, or if you just have pre-sales questions, the Alesis technical support team is available to help!
Each product has a dedicated support page on the website where you can find manuals, specifications, software updates, drivers and troubleshooting guides: www.alesis.com
Visit the link below to connect with any of the following support options: online community support, phone support, email support.
Privileged Password Manager for Enterprises
Privileged Password Management With Password Manager Pro
Securely share administrative passwords with the members of your team on need basis.
Automatically reset the passwords of servers, databases, network devices and other resources.
Control access to IT resources and applications based on roles and job responsibilities.
World's Largest Organizations Rely on Password Manager Pro
The IT divisions of some of the World's largest organizations and Fortune 500 companies rely on Password Manager Pro to control access to their IT infrastructure. Over 300,000 IT admins and end users log in to Password Manager Pro on a typical day and manage millions of privileged passwords.
Highlights of Password Manager Pro
Password Storage, Management & Workflow
Centralized Password Vault
Store all your enterprise passwords - privileged accounts, shared accounts, firecall accounts and others in the secure, centralized repository.
Shared Administrative Password Management
Securely manage shared accounts such as 'Administrator' on Windows, 'root' on Unix/Linux, 'enable' on Cisco, 'sa' on SQL and others.
Password Access Control Workflow
Request-release controls for password retrieval. Provision for granting time-limited access, exclusive privilege and concurrency controls.
Password Sharing, User Provisioning & Management
Password Ownership & Sharing
Well-defined ownership for the passwords stored in the centralized vault. Provision for selective sharing of passwords on need basis.
Active Directory / LDAP Integration
Import users / user groups from Windows Active Directory or LDAP and also leverage the authentication mechanism.
Role-based Access Controls
Fine-grained restrictions on managing resources and passwords stored in PMP. Restrictions are enforced based on predefined user roles.
Remote Password Reset
Automated Password Resets
Reset the passwords of remote resources from Password Manager Pro web-interface as and when required or automatically through scheduled tasks.
Enforce Password Policy
Ensure usage of strong passwords and periodic resets by creating and enforcing your password policy.
Wide Range of Target Systems
Supports out-of-the-box a wide range of target systems, databases, network devices for access control and automatic password resets.
Application-to-Application Password Management
Any application or script can query PMP and retrieve passwords to connect with other applications or databases, eliminating hard-coded passwords.
Windows Service Accounts Management
Automatically identify and reset the passwords of service accounts associated with domain accounts.
Post-Password Reset Custom Script Execution
Option to automatically execute custom scripts to carry out any follow-up action after a password reset action.
Privileged Session Management, Remote Access & Auto Logon
First-in Class Remote Login
Users can launch highly secure, reliable and completely emulated Windows RDP, SSH and Telnet sessions from browser without any plug-in or agent software.
Privileged Session Recording
Privileged sessions launched from PMP can be completely video recorded, archived and played back for forensic audits.
Automatic Login to Target Systems, Websites
Automatically log on to the target systems, websites and applications directly from the PMP web interface without copying and pasting of passwords.
Audit, Compliance & Reports
Comprehensive Audit Trails & Reporting
Complete record of 'who', 'what' and 'when' of password access. Intuitive reports on entire password management scenario in your enterprise.
Real-time Notifications, SIEM Integration
Real-time alerts on the occurrence of various password events enabling integration with Security Information and Event Management (SIEM) solutions
PCI DSS Compliance Reporting
Reports on the violations with respect to the use and management of privileged passwords based on the requirements of PCI-DSS.
Secure and Enterprise Ready
Extremely Secure & Reliable
All passwords & sensitive data are encrypted using AES 256-bit encryption. Dual encryption for extra security. Can be configured to run in FIPS 140-2 compliant mode.
Two-Factor Authentication
Enforcing two successive stages of authentication for logging in to PMP. Usual authentication is the first stage. Various options provided for the second stage.
Mobile Access
Retrieve passwords and approve requests on the go. Provision for secure offline access.
Android App iPhone App Windows App
Disaster Recovery & High Availability
Live Backup
Provision for both scheduled and live backup of entire database for disaster recovery.
High Availability Architecture
Uninterrupted access to enterprise passwords through the deployment of redundant server and database instances. (A single Premium or Enterprise Edition license is enough for High Availability).
Secure Offline Access
Retrieve passwords even when there is no internet connectivity. The offline copy is as secure as the online version. Offline access is available in mobile app too.

- Success Stories
- Customer Voice
- Alliances
- Product Reviews
- Magazine Articles
- White Papers
- Advisory
Password Manager Pro has earned the business and goodwill of scores of customers worldwide. Its deployment has immensely benefitted businesses in many ways. The following are a few samples:
"The automated, policy-driven password management provided by Password Manager Pro has made us realize how inefficient and insecure the traditional 'excel sheet storage' approach was. Usage of Password Manager Pro is certainly the best practice approach for us."
 Stefan Stefansson
Stefan StefanssonNova, Iceland

ManageEngine has partnered with PhoneFactor, the leading global provider of phone-based two-factor authentication, to enable simple, effective two-factor security for Password Manager Pro. ManageEngine is a PhoneFactor Alliance Partner and offers seamless integration with PhoneFactor's authentication services.

ManageEngine has forged a technology interoperability partnership with RSA, The Security Division of EMC (NYSE: EMC), and has achieved RSA Secured® certification. Password Manager Pro is technically interoperable with the RSA SecurID® two-factor authentication system.

"
Password Manager Pro offers a great feature set at a very reasonable cost.
"
SC Magazine, the world's longest running monthly publication focusing on information security reviewed Password Manager Pro as part of its Group Test of various password management solutions. Learn More.
Articles on Password Management authored by Password Manager Pro analyst in various magazines:
What Platforms Does Password Manager Pro Support?
- Platforms (for password reset):Windows, Windows Domain, Linux, IBM AIX, IBM AS400, HP UNIX, Solaris, Mac OS, Sun Oracle XSCF, Sun Oracle ALOM, Sun Oracle ILOM, VMWare ESXi, MS SQL server, MySQL Server, Oracle DB Server, Sybase ASE, LDAP Server, HP iLO, HP ProCurve devices and Cisco Devices (IOS, CatOS, PIX), Juniper Netscreen Devices
- Platforms (for product installation): Windows, Linux
What Problems Does Password Manager Pro Solve?
If you are an IT Administrator responsible for securely managing your IT infrastructure, check yourself:
- Are you drowning in a pile of privileged passwords? Do you store administrative passwords in spreadsheets & flat files?
- Do you find it difficult to track who has access to which accounts?
- Do you laboriously logon to each application separately to periodically change passwords?
If yes, you certainly need Password Manager Pro!
Administrative/Privileged passwords are literally aplenty in enterprises. Servers, databases, switches, routers, firewalls and any other hardware or software, could have equally large number of administrative passwords. These passwords are insecurely stored in spreadsheets, text files and even as printouts and are shared by a group of administrators.
This traditional practice brings with it a host of issues such as:
- Insecure storage of passwords inviting security threats
- Uncontrolled super-user privileges
- No role-based access control; internal controls become fragile
- Lack of accountability for actions
- No provision for enforcing standard password practices/policies
- No centralized control
Password Manager Pro solves all these problems by providing a secure system to store, administer, and share passwords.
What are the Licensing Options for Password Manager Pro?
There are three license types:
- Evaluation download valid for 30 days capable of supporting a maximum of 2 administrators. You can test Enterprise edition features.
- Free Edition licensed software allows you to have 1 administrator and manage up to 10 resources. Valid forever.
- Registered Version - Licensing is based on two factors:
- Number of Administrators
- Type of Edition - Standard, Premium or Enterprise
Note:
Password Manager Pro comes with five user roles - Administrator, Password Administrator, Privileged Administrator, Password Auditor and Password User. The term 'administrator' denotes Administrators, Password Administrators and Privileged Administrators. So, licensing restricts the number of administrators as a whole, which includes Administrators, Password Administrators and Privileged Administrators. There is no restriction on the number of Password Users and Password Auditors. To get more details on the five user roles, refer to this section of our help documentation.
- Standard Edition - If your requirement is to have a secure, password repository to store your passwords and selectively share them among enterprise users, Standard Edition would be ideal.
- PremiumEdition - Apart from storing and sharing your passwords, if you wish to have enterprise-class password management features such as remote password synchronization, password alerts and notifications, application-to-application password management, reports, high-availability and others, Premium edition would be the best choice.
- Enterprise Edition - If you require more enterprise-class features like auto discovery of privileged accounts, integration with ticketing systems and SIEM solutions, jump server configuration, application-to-application password management, out-of-the-box compliance reports, SQL server / cluster as backend database, Enterprise edition will be ideal.
Password Management Features Matrix
- All Features of Standard Edition
- AD / Azure AD Sync - User groups & OUs
- Auto Logon Helper
- Password access control workflow
- Admin dashboard (Live feeds, reports and graphs)
- Password action notifications (Resource group-specific)
- Remote Password Reset (On-demand, Scheduled, and Action-based) - List of supported platforms
- Agent-based password reset
- Canned reports
- Two-factor authentication - PhoneFactor, RSA SecurID, Google Authenticator, Duo security, YubiKey, Microsoft Authenticator,Okta Verify
- High availability
- Privileged session recording
- AD / Azure AD Sync - User groups & OUs
- Privacy settings
- Password reset plugin
- User Sessions
- Trash Users
- IP Restrictions - API access and Agent Access
- Disable Password Resets for Privileged Accounts
- Password Reset using SSH Command Sets
- All features of Premium edition
- Data Encryption and Protection with SafeNet HSM
- MS SQL server as backend database
- Password management API (XML RPC, SSH CLI)
- Privileged accounts discovery
- Active directory sync - resources
- LDAP Sync - User and User Groups
- SAML 2.0 support
- Remote SQL sessions with auto logon
- Role customization
- Ticketing system integration-ServiceDesk Plus On-Demand, ServiceDesk Plus MSP, ServiceDesk Plus, ServiceNow, JIRA Service Desk
- Custom password reset listeners
- Scheduled export of encrypted HTML files
- SIEM integration - SNMP traps & Syslog messages generation
- Email templates for notification configuration
- Landing Server Configuration
- Federated Identity Management
- Smart Card / PKI / Certificate Authentication
- Two-factor Authentication - RADIUS
- Custom Reports
- Out-of-the-box compliance reports (PCI DSS, NERC-CIP, ISO/IEC 27001, GDPR)
- SQL query reports
- Privileged session shadowing and termination
- SQL server failover clustering
- RESTful API
- Encryption key rotation
- EAR support while using MS SQL as backend database
- Purging selective session recordings
- File transfers over remote desktop sessions
- Secure cloud storage options
- CI/CD Platform Integration - Jenkins, Ansible, Chef, Puppet
Password Manager Pro Add-on Features
10 Software to Recover Product Key Licenses from Computer
There are many backup software on the market and some of them does a really good job in making sure that there is an exact copy of the important files available at the backup drive. Although backing up of files is important, many people forget to backup the Windows product key or third party software license that is installed on their computer. When their computer crashes and had to reinstall everything from scratch, they had to go through the trouble of searching for the license number to activate the software that they’ve purchased. If the license key are misplaced and forgotten, they’d have to contact the software support team and provide them with proof of purchase so that they can reissue the license.
The problem is software licenses aren’t stored in one standard location where you can just copy the whole folder to backup and then paste it back to reactivate all the software. They are stored all over the place either in a form of an external file or a registry key. Fortunately we found 10 software that can scan your computer and recover the lost or forgotten product key licenses so you can back it up in case you need to reactivate them again. Computer technicians can also use these software to help customers recover their software license numbers from non-bootable drive.
1. LicenseCrawler
LicenseCrawler is a portable license recovery tool that is free for private use. It scans the registry area on local and remote computers located at the same network for available serial numbers for Windows, Office and third party applications. The amount of software license that LicenseCrawler can detect is unknown because there is no such information being published at their website or program. Since it is free, you can run it and cross check if it is able to reveal the license for the shareware installed on your computer. Works on all versions of Windows including both 32-bit and 64-bit.
Download LicenseCrawler
2. MSKeyViewer Plus

MSKeyViewer Plus is free and portable. Although the name of this tool sounded like it can only view Microsoft key, but it also support Office and third party applications as well. To view the supported applications, run the program, click the About button and followed by clicking the Supported Products button. The list of supported product seems a bit outdated because this program itself was last updated nearly 2 years ago.
Download MSKeyViewer Plus
3. Product Key Finder

Product Key Finder is free but take note of the adware installation when installing this program. It is a very simple program that claims to support over 200 programs but without a detailed listings. Running the program will instantly list all the license number and allows you to backup to a CSV file by clicking the Save button. Only support 32-bit Windows operating system.
Download Product Key Finder
4. Softkey Revealer

Softkey Revealer is free and portable program that is able to support retrieving licenses from a huge list of software which can be found on this page. Other than just depending on the signature that they created, it also seems to list keys with the value username, password, user and etc. The program is very small in size at only 200KB in size and even comes with additional tools to decrypt Adobe encrypted key, removing content advisor password and changing the current Windows key.
Download Softkey Revealer
5. Keyfinder Thing

Keyfinder Thing is probably one of the most popular free tool to help you recover product keys from your computer. It supports a total of 90 software titles which can be viewed from the View > Software List. You can save the results from the File menu. Take note of the installation of adware during setup.
Download Keyfinder Thing
6. Magic Keyfinder 2012

Magic Keyfinder 2012 is actually a shareware but the you can use it for free with a huge limitation where only the first 10 digits of the supported product keys are displayed. The actual amount of supported software are unknown. Other than using their database signature, you can also use the deep scan where it detects a certain keywords and determine that it is a possible license key. During testing, only 5 digits from our Windows 7 product keys are being displayed.
Download Magic Keyfinder 2012
7. Product Key Viewer

Product Key Viewer is a shareware that supports retrieving license key over 1000 applications from your computer. Only the Pro and Tech version will report activation keys for third party applications. The Lite version will only locate the Windows and Office product keys. You can test Product Key Viewer to identify what software is being identified on your computer for free except the data are being partially hidden.
Download Product Key Viewer
8. Product Key Finder by Top Password

The name of this software is exactly the same as the one listed under number 3 except this is a shareware that cost $17.95 and developed under a different company called Top Password. The amount of supported software is unknown but the official webpage did mention Windows, Office, SQL Server, Exchange Server, Visual Studio, VMWare, Adobe and many other products. The results are displayed instantly upon scanning. It supports scanning the current system, remote system or even on non-booting systems. Works on both 32-bit and 64-bit Windows.
Download Product Key Finder by Top Password
9. Product Key Explorer

Product Key Explorer is a shareware that cost $29.50 that supports more than 4000 software and games as well. You can view the complete list of supported products at this page. You can scan both local and remote computers with the built-in option to use a different login credentials. The results can be saved to an external file or a registry file.
Download Product Key Explorer
10. Recover Keys

Recover Keys is developed by the same company as KeyFinder Thing except that this is their shareware version that supports over 3000 software titles including games. It cost $24.95 to unlock the program or else it will only show the first 4 characters of the license number. It also comes with advanced features to scan multiple computers through IP range or manually selecting the computers that is available on the network.
Download Recover Keys
Editor’s Note: After testing the 10 product key recovery software above, the software that stood out in the tests are LicenseCrawler and Recover Keys. Both of this tool managed to retrieve additional licenses that weren’t detected on the other 8. Although some of the software claims to support recovering license keys from more than a few thousands software, it is possible that the software installed on your computer is not in the list. You can definitely make a request by contact them to include it in their database.
What’s New in the CC Software Access Password Recover 2.00 serial key or number?
Screen Shot

System Requirements for CC Software Access Password Recover 2.00 serial key or number
- First, download the CC Software Access Password Recover 2.00 serial key or number
-
You can download its setup from given links:
.JPG)