
Delphi 5 serial key or number

Delphi 5 serial key or number
Delphi quick start
Below is a quick-start entry into how to use our license management components in your Delphi applications. Please make sure you read the introduction before following this article. You can also have a look at the code for one of the demonstrations that ship with the package.
The HexLicense package consists of three parts:
- The serial number generator application
- The Delphi license components
- The Delphi plugin menu
The license component package consists of 7 non-visual components. These components can be dropped on a form or a datamodule. They require very little work on your part and can just as easily be dropped into an already existing application as a completely new program.
The license components are as follows:
- THexLicense
- THexSerialNumber
- THexSerialMatrix
- THexFileLicenseStorage
- THexRegistryStorage
- THexOwnerStorage
Generating your root key
Adding serial management to your application begins with the serial number generator. The generator (called “keygen” from now on) allows you to generate a random root key, which is the basis from which all compatible serial numbers are derived.
Optionally you may type in your own root-key sequence, but you should try to keep your root-keys as unique as possible.
In the picture above the root key is defined by the 12 hexadecimal input boxes. You can use your own values or simply click “new key” to make a random number sequence.
When the key changes the application automatically generates the delphi code you see in the text-edit box below the key values. You need to copy this source-code into your Delphi application and preferably store it in a separate unit. A hexadecimal key is much harder to locate for hackers, since it’s stored with the machine code as opposed to a resource string or text constant.
Generating serial numbers
Once you have generated or typed in a root-key, the keygen application can be used to generate a large amount of unique serial numbers. Each of them derived from this root-key alone, which is also the only numeric sequence capable of validating them.
Note: While you can in theory create a massive amount of serial numbers from the same key, I strongly advice against this. All numbers once large enough begins to suffer from atrophy, meaning that the algorithm must search through a growing spectrum to locate an unused and reproducible combination.
It’s the exact same problem which make technologies like bit-coin extremely hard to work with. In that terminology locating a reproducible combination is referred to as “mining”.
In short: The more serial numbers you generate from the same root-key, the larger the distance between reproducible number combinations. The distance between matches grows exponentially as you mint and exhaust the base numbers.
As such I recommend that you generate an absolute maximum of 6000 serial numbers per key. But Istrongly urge you to create a new key for every 1000 licenses you put into circulation.
Preparing your online store
Most online store-fronts support pre-generated lists of serial numbers. Typically you are expected to upload a serial-number file to the server as a normal text-file. Lately some vendors also accept XML and JSON formats as well.
Personally I would like to recommend Gumroad as a vendor. They allow you to upload serial lists and their service is simplicity itself for both customer and provider. Another vendor which accepts serial-number lists is ShareIT, albeit their solution is more troublesome for the customer.
To generate serial numbers, simply click the “generate” button from the toolbar and select the amount. Please note that the more serials you mint, the longer it will take to produce the list (!)
Having generated your serial numbers there are two things you must do:
- Copy the Root-key const
- Export your serial numbers
- Save your key to disk (keep safe)
Root-Key constant
As mentioned, the keygen will automatically create a line of Delphi code for you; A single const array declaration which contains your root-key. This must be copied into the source-code of your application.
When you start your application the THexSerialMatrix component will ask for the root key. It does this through the OnGetKeyMatrix event.
Exporting serial numbers
Simply click the Export button from the keygen toolbar and you will be presented with several file-formats to choose from. You can choose to save the serial number list as:
- Text file
- XML dataset (TClientDataset)
- Binary dataset (TClientDataset binary format)
- JSON file
Since the majority of online vendors support plain text-files, this is the best format to pick. I have also added JSON support since I have nodeJS based servers written in Smart Mobile Studio for HTML5 services.
Save your key to disk
Having created a root-key, generated serial numbers and exported them to the file-system, remember to save your key as well. While you can just type in the root key, saving it in a safe place makes it easier to keep track of your number series.
Please note that saving your key does not save any generated lists. You are meant to use a different root-key ever time you mint new serial numbers.
The Delphi side of things
Now that you have done the preliminary work it’s time to work with the components from Delphi. Before we start, a few words about architecture:
Delphi allows your to auto-create datamodules as part of your application’s startup sequence. Datamodules are, as you probably know, “invisible forms” (actually they are components with resource persistency) which can host non-visual components exclusively.
If you are adding license management to an already existing application, chances are that you want to keep it separate from your already existing codebase. If that is the case, simply add a blank datamodule to your project and make sure Delphi automatically creates it when your application starts.
You start by dropping the following components on your datamodule or form:
- THexLicense
- THexSerialNumber
- THexSerialMatrix
Selecting a storage mechanism
Next you need to select a storage mechanism. By default HexLicense ships with 3 different storage adapters, these are:
- THexFileLicenseStorage
- THexRegistryLicenseStorage
- THexOwnerLicenseStorage
I strongly urge you to pick THexOwnerLicenseStorage. Using this storage adapter you can handle the entire storage of license information via ordinary Delphi events. It is imperative that you find a safe place to store the actual license data – here you are only limited by operative system credentials and creativity. Some typical places to store data are:
- Encoded into the pixel-buffer of an image
- Stored as a file inside a zip-file cabinet (password protected)
- Stored as a resource inside an .exe or .dll file (MSDN: UpdateResource API)
- Stored as a TAG chunk of an image file
Connecting the root-key
The component THexSerialMatrix has a single event called “OnGetKeyMatrix”. You must respond to this event and return the const array generated by the codegen. An example of such an event handler is:
procedure TfrmMain.HexSerialMatrix1GetKeyMatrix (Sender: TObject;var Value: THexKeyMatrix); Const CNT_ROOTKEY:THexKeyMatrix = ($4F,$9B,$BD,$7E, $79,$8E,$40,$98,$93,$EC,$FB,$D0); begin Value:=CNT_ROOTKEY; end;This is more or less all the manual coding you have to do. Next you simply need to connect each component to its corresponding published properties.
THexLicense must have it’s properties “SerialNumber” and “Storage” connected to the THexSerialNumber and THexStorage component you selected (THexOwnerLicenseStorage is recommended).
THexSerialNumber needs to have the property SerialMatrix connected to the THexSerialMatrix component you dropped on the form or datamodule.
And finally, THexOwnerLicenseStorage must have it’s SerialMatrix property connected to the same THexSerialMatrix component as THexSerialNumber.
This may sound very complex but it’s very easy and self-explanatory when you examine the properties for these components.
Storage events
The component THexOwnerLicenseStorage exposes only three events. These are:
- OnDataExists
- OnReadData
- OnWriteData
The component does not really care how or where you store the license data (which is just a small chunk of encrypted data), it only cares that these three events are handled properly.
When your application starts the first event to fire on this component is OnDataExists.
If no data can be found (meaning, that it’s the first time the user starts you program) a blank license is initialized and immediately stored though OnWriteData.
What is written inside the license file greatly depends on what type of license you want to use. As of writing you can choose between:
- ltDayTrial
- ltFixed
- ltRunTrial
ltDayTrial
Day trial allows the user to test your product for a finite amount of days. Typically 14 or 30 days of free use, before the customer must buy a full license if he or she wants to continue using your application. The amount of days is defined by the property “duration” of THexLicense. The program starts to count down the first time the application is executed. It also checks if the clock has been held back.
ltFixed
While rare, this type of license allows you to compile a fixed start and stop date into your application – and your program will only work within the range of those dates. The start and stop-dates are defined by the “fixedStart” and “fixedEnd” TDateTime properties exposed by THexLicense.
ltRunTrial
This kind of license allows the user to start your application a finite amount of times, typically 100 times for commercial applications or 200 times for share-ware. The amount of runs is defined by the “duration” property of THexLicense.
You define your license type completely through the properties of THexLicense. This component also exposes all the events you need to handle activation, trial “time out” and other measurements. By setting the property “Automatic” to true the license session is initialized immediately when the application starts. If you want a finer grain of control over how the license management system works, you can set disable to false and activate the component by calling the method “BeginSession()” whenever you mean it’s most appropriate for your program.
Final words
HexLicense ships with two demonstration programs that show exactly how to deal with everything explained so far. Each demonstration is heavily documented (in code) to make the process as straight-forward as possible; even for novice Delphi developers.
It is important to recognize that HexLicense was designed to deal with serial number generation, validation and recognition. It was made to keep ordinary customers from abusing your licenses – and also for you to have a uniform way of linking customers to their licenses in order to protect their investment.
But there is no such thing as an un-crackable product. If a company makes such a claim I would avoid them at all cost, because lying about something so fundamentally incorrect is simply fraud.
“Bottom line: only with a secure hardware dongle, implemented correctly, can you guarantee against cracking” -Source: John Browne, Wibu systems
Microsoft spent millions trying to come up with a scheme to make Windows “un breakable”, yet only hours after Windows 7 was released – a fully working cracked pirate version could be downloaded from the internet. Same with Windows 10 and all previous version of their operative system.
The same goes for huge corporations like Adobe, Apple and all the others. The open-source tools for disassembling and reverse-engineer software is just as evolved as the products to compile and build software.
If you are going to put your trust in a company or security company, at least make sure they are honest and genuinely interested in buying you time, which is what serial number protection is all about.
In short, serial number protection gives you the following advantages:
- Non technical users are stopped from abusing their license
- Serious customers recognize the value of a proper license
- By carefully planning your release cycle and the use of keys, you can minimize loss even if your product is hacked. Only the hacked build will be vulnerable, which represents only a single key combination
HexLicense makes it harder and more time consuming for hackers to break your software, they have to go out of their way to do so. This time, the point of sales window, is basically where you make your earnings. The larger the windows of opportunity, the more sales you can secure.
Steps you can take
There are several steps you can take to make your product more time consuming to break, like refusing to run the application if a system-wide debugger is running and also to disable memory dumps. These steps are publicly known, and while effective – they wont stop the most experienced hackers from getting at your code. Nothing will. Thats just reality.
But at least with HexLicense you wont make it easy for them, and it will stop ordinary users from copying your work without any resistance.
adventureenergy

Delphi 7 Personal Promotion came free with some magazines. Some of these magazines provided an incorrect link to obtain the Serial Number and Authorization key. I am trying to make delphi program Server And Client so To Secure my App and To Make Sure all user are under control i should give them a unique Key that can't be. Nov 07, 2013 I need serial number of Borland Delphi 7 Enterprise. Serial number of delphi 7. Authorization Key.
This release was created for you, eager to use Delphi 5 full and with without limitations. Our intentions are not to harm Delphi software company but to give the possibility to those who can not pay for any piece of software out there. This should be your intention too, as a user, to fully evaluate Delphi 5 without restrictions and then decide. If you are keeping the software and want to use it longer than its trial time, we strongly encourage you purchasing the license key from Delphi official website. Our releases are to prove that we can!
Nothing can stop us, we keep fighting for freedom despite all the difficulties we face each day. Cara Download Majalah Dewasa Gratis. Last but not less important is your own contribution to our cause. Full Moon Wo Sagashite Episodi Streaming Ita.
You should consider to submit your own serial numbers or share other files with the community just as someone else helped you with Delphi 5 serial number. Sharing is caring and that is the only way to keep our scene, our community alive.
The strongest and most complete protection available today for Borland Delphi and C++ Builder. ICE License is a new and innovative licensing protection system for Borland developers wishing to integrate copy protection and maximum security into their applications.
Professional Copy Protection for Borland
ICE License is designed for Borland Delphi (from Delphi 5 up to 2007) and C++ Builder, add VCL copy protection system on your projects and get a high level of security.
Some protections don't work in entreprise environment, because user's account is limited or restricted and require administrator rights to run application, so you lose many customers becaue they can't try your evaluation version.With ICE License you can protect your application, run in restricted environment without requiring administrator right, it's difference than other protection.
With ICE License it's easy to turn your application into "try-before-you-buy" versions with little effort, offering everything to guarantee maximum protection. If you want to protect your investments, ICE License is designed specifically for you. ICE License has been created for the software developer looking for powerful and flexible protection, license management tools and to retain total control of their software products when delivering them into the hands of their customers.
Build Multi-Editions in One
Building one product version and using digital licensing to partition that product through license-based feature access controls reduces the need for distinct product upgrades and saves engineering and quality assurance costs. ICE License Protection can help you prevent key generation and therefore help to protect your investment.
Our Protection Technology
Antidebugging protection to prevent reverse engineering
ICE License use antidebugging and antimonitoring protect which provide a good way to prevent people from analysing your code instructions.
Asymmetric encryption technology to prevent against key generator
ICE License Protection provides a high barrier against illegal copy using the power of asymmetric encryption to protect your application. The asymmetric encryption system allows for the transmission of secret information over an open channel without a common secret key previously shared between the ends of the transmission. Your application is protected by two keys; One key (public key) is inside your application and the second is a private key known only to the developer. These two keys are used in combination to encrypt and decrypt the software Key.
Even if cracker can access to the source of ICE License, he cannot make key generator, due to the Asymmetric Encryption (based on public key asymmetric) systems, example : RSA Encryption, the source is available on the net, but it's very hard to break.
Only you can control the software license creation so that no key generator can be made.
Runtime Source Code Encryption to prevent against patching or cracking
Fragments of code are marked in your source code by using special start and end marks. These fragments of code are recognized by ICE License in the compiled application and are additionally encrypted during the protection process.
Runtime encrypted code always stays encrypted in memory. It's managed by special code each time it should be executed. Due to the encrypted blocks inside your software, your program cannot be completely cracked without a real key. This ActiveKey can be provided only in the Full License Key.
If cracker try to patch your application to avoid control, he cannot crack (to turn in full) your software, because inside your compiled executable, the key for decryption is not inside, it's different approach than other protection.
Secure application strings resource using encryption
With the SecureStrings feature, you can encrypt all strings in your application. SecureStrings encrypt and decrypt in memory to protect them from being viewed or changed by anyone other than developer. These options provide good protection against executable modification. All ICE License information is encrypted and protected in your project resource to reduce the risk of being cracked.
MachineID technology to prevent unauthorized copy of your software
Machine locking prevents your software from being illegally duplicated and used on other machines. The License can be run on the specified machine only. This protection it's based on CPU, Bios and Hard Disk manufacturer identification. This protection is not based on the getvolume and other routines that require you to send a new license if the user reformats their HDD. Note MachineID result is not warranties.
Prevent against illegal license exportation - Unique !
ICE License is the first and only protection which enables you to get total control of licenses using country locking. With this new technique, you can prevent illegal exportation of the LicenseKey.
If you create a LicenseKey for a customer located in the United States, other people from around the world cannot use this LicenseKey.
Even if a customer tries to deploy or supply the LicenseKey for other people arould the world, the LicenseKey will be not valid. This technique allows you to protect your LicenseKey against illegal warez or serialz websites.
Create a key generator for distributor
ICE License Protection allows you to create a key generator for your Distributor or Partner to allow them to create licenses for your customers without the need to contact you.
Network Protection - control each workstation (TCP/IP protocol)
ICE License is designed for networks and allows you to control the number of simultaneous users. It lets you effectively license your application in network environments by controlling the number of software copies that can run at the same time or by assigning the application to specific workstations by Computer ID.
ICE License can prohibit the copying of your software from the server hard drive, limit the number of simultaneous workstations, or assign the application to specific workstations by Computer ID.
ICE License can limit and lock the number of allowed network users or computers.
Features
· Sophisticated Asymmetric Encryption Technology (prevent against Key Generator)
· Advanced Digital Authentication to prevent against patching
· Advanced Code Encryption Protection to prevent against cracking or dumping
· Transfer License to another PC (Trial License or Full License)
· Create a Key Generator for your partner or distributor
· Detects backdating or demo reinstallation to gain additional usage
· AES Rijndael Encryption functions to protect your data
· Cryptographic hashing MD5 to lock licenses to your software
· Machine Locking Protection (when is possible)
· Network LAN Control Protection by TCP/IP Protocol (in Trial or Full Mode)
· Encrypt & Hide Application Strings to provide a high level of security
· Prevent and Control your LicenseKey against illegal exportation - New !
· Using compact LicenseKeys to register with ActiveKey for increased security
· Add Extra Information inside License (in Trial or Full Mode)
· Restricted Environments (Limited User Mode for NT4, 2000, XP)
· View LicenseKey to see details about any License
· Create custom URL links to directly access your ordering web page
· Invisible software based protection requiring no dongles
· Create "Trial Edition" by days, number of uses, hours or a set date
· Compatible with Windows 95, 98, Me, NT, 2000, XP.
· Support Windows XP SP2 (from ICE License v2.09)
· Sources available in Pro Edition only include VCL + ICE Network Server source
ICE License actually resists piracy and also prevents the spread of universal cracking methods.
Get free fully functional version for evaluation, please go to Download Center
borland delphi license control software protection borland delphi c++ builder protection copy protection delphi, software protection delphi, delphi license control, digitals rights, borland delphi protection, shareware protection, delphi lock, native delphi vcl protection

Screen Captures
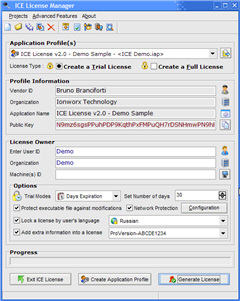
ICE License Manager
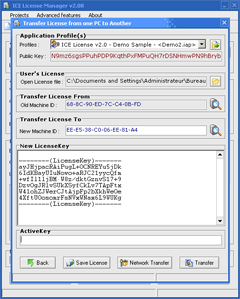
Transfer License Menu
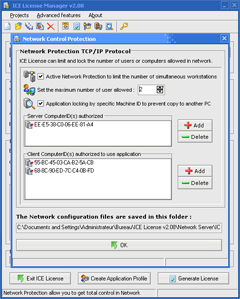
Network Control Management
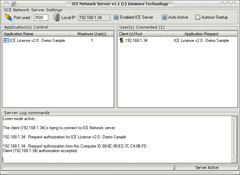
ICE Network Server (Monitoring)
Distributor Key Generator Management
What’s New in the Delphi 5 serial key or number?
Screen Shot

System Requirements for Delphi 5 serial key or number
- First, download the Delphi 5 serial key or number
-
You can download its setup from given links:


