
4th Pass Source Guard Enterprise Edition v4.0 serial key or number

4th Pass Source Guard Enterprise Edition v4.0 serial key or number
*サンウェーブ【日本限定モデル衝撃価格】*GK[W*サンウェーブ 在庫あり即納/F]-A-105F[L/R]BL 吊戸棚[不燃仕様]/R]BL GK-BLシリーズ GK-BLシリーズ 間口105cm:給湯器とガスコンロのお店
▼お選びください アイボリー(GKF) ライトオーク(GKW) ▼お選びください 左勝手タイプ(L) 右勝手タイプ(R)



↑モバイルページはこちら
 メーカーサンウェーブ商品名GK[W/F]-A-105F[L/R]BL 吊戸棚(不燃処理仕様)外形寸法(mm)幅1050×奥行367×高さ500備考 ※こちらの商品は扉カラー【アイボリー(GKF) / ライトオーク(GKW)】が選択できます。
メーカーサンウェーブ商品名GK[W/F]-A-105F[L/R]BL 吊戸棚(不燃処理仕様)外形寸法(mm)幅1050×奥行367×高さ500備考 ※こちらの商品は扉カラー【アイボリー(GKF) / ライトオーク(GKW)】が選択できます。※商品写真はアイボリー(GKF)です。
※こちらの商品は、受注生産品ですので、お届けに日数がかかります。注意不燃処理吊戸棚は、右勝手タイプ(R)の場合、左側面【左勝手タイプ(L)の場合は右側面】と底面に不燃処理をしている吊戸棚です。レンジフードの右側に設置するときは右勝手タイプ(R)、左側に設置するときは左勝手タイプ(L)の不燃処理吊戸棚を選択してください。
※不燃処理吊戸棚について


■木製扉
下記の2色からお選びいただけます。

※商品は写真のため、実際とは色が異なる場合があります。
登录 | 注册 | 外贸论坛
- 中国の炎のグループ株式会社。
*サンウェーブ【日本限定モデル衝撃価格】*GK[W*サンウェーブ 在庫あり即納/F]-A-105F[L/R]BL 吊戸棚[不燃仕様]/R]BL GK-BLシリーズ GK-BLシリーズ 間口105cm:給湯器とガスコンロのお店
正会員8 年
- ホーム
- 製品カタログ
- 会社概要
- 品質管理
- ガスコンロ,ガステーブル,ガス器具,給湯器,ふろ給湯器,給湯機,ガス器具,大阪ガス,東京ガス,設置工事可能,水廻り,水栓,給湯器交換,石油ボイラー,石油給湯器,リンナイ,パロマ,ノーリツ,パーパス,,*サンウェーブ*GK[W/F]-A-105F[L/R]BL,吊戸棚[不燃仕様],GK-BLシリーズ,間口105cm花·ガーデン·DIY,木材·建築資材·設備,キッチン用設備,システムキッチン お問い合わせ
- 割当て要求
Pretty Good Privacy
Pretty Good Privacy (PGP) is an encryption program that provides cryptographicprivacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991.[2]
PGP and similar software follow the OpenPGP, an open standard of PGP encryption software, standard (RFC 4880) for encrypting and decrypting data.
Design[edit]

PGP encryption uses a serial combination of hashing, data compression, symmetric-key cryptography, and finally public-key cryptography; each step uses one of several supported algorithms. Each public key is bound to a username or an e-mail address. The first version of this system was generally known as a web of trust to contrast with the X.509 system, which uses a hierarchical approach based on certificate authority and which was added to PGP implementations later. Current versions of PGP encryption include both options through an automated key management server.
PGP fingerprint[edit]
A public key fingerprint is a shorter version of a public key. From a fingerprint, someone can validate the correct corresponding public key. A fingerprint like C3A6 5E46 7B54 77DF 3C4C 9790 4D22 B3CA 5B32 FF66 can be printed on a business card.[3][4]
Compatibility[edit]
As PGP evolves, versions that support newer features and algorithms are able to create encrypted messages that older PGP systems cannot decrypt, even with a valid private key. Therefore, it is essential that partners in PGP communication understand each other's capabilities or at least agree on PGP settings.
Confidentiality[edit]
PGP can be used to send messages confidentially. For this, PGP uses hybrid cryptosystem by combining symmetric-key encryption and public-key encryption. The message is encrypted using a symmetric encryption algorithm, which requires a symmetric key generated by the sender. The symmetric key is used only once and is also called a session key. The message and its session key are sent to the receiver. The session key must be sent to the receiver so they know how to decrypt the message, but to protect it during transmission it is encrypted with the receiver's public key. Only the private key belonging to the receiver can decrypt the session key, and use it to symmetrically decrypt the message.
Digital signatures[edit]
PGP supports message authentication and integrity checking. The latter is used to detect whether a message has been altered since it was completed (the message integrity property) and the former, to determine whether it was actually sent by the person or entity claimed to be the sender (a digital signature). Because the content is encrypted, any changes in the message will result in failure of the decryption with the appropriate key. The sender uses PGP to create a digital signature for the message with either the RSA or DSA algorithms. To do so, PGP computes a hash (also called a message digest) from the plaintext and then creates the digital signature from that hash using the sender's private key.
Web of trust[edit]
Both when encrypting messages and when verifying signatures, it is critical that the public key used to send messages to someone or some entity actually does 'belong' to the intended recipient. Simply downloading a public key from somewhere is not a reliable assurance of that association; deliberate (or accidental) impersonation is possible. From its first version, PGP has always included provisions for distributing users' public keys in an 'identity certification', which is also constructed cryptographically so that any tampering (or accidental garble) is readily detectable. However, merely making a certificate which is impossible to modify without being detected is insufficient; this can prevent corruption only after the certificate has been created, not before. Users must also ensure by some means that the public key in a certificate actually does belong to the person or entity claiming it. A given public key (or more specifically, information binding a user name to a key) may be digitally signed by a third party user to attest to the association between someone (actually a user name) and the key. There are several levels of confidence which can be included in such signatures. Although many programs read and write this information, few (if any) include this level of certification when calculating whether to trust a key.
The web of trust protocol was first described by Phil Zimmermann in 1992, in the manual for PGP version 2.0:
As time goes on, you will accumulate keys from other people that you may want to designate as trusted introducers. Everyone else will each choose their own trusted introducers. And everyone will gradually accumulate and distribute with their key a collection of certifying signatures from other people, with the expectation that anyone receiving it will trust at least one or two of the signatures. This will cause the emergence of a decentralized fault-tolerant web of confidence for all public keys.
The web of trust mechanism has advantages over a centrally managed public key infrastructure scheme such as that used by S/MIME but has not been universally used. Users have to be willing to accept certificates and check their validity manually or have to simply accept them. No satisfactory solution has been found for the underlying problem.
Certificates[edit]
In the (more recent) OpenPGP specification, trust signatures can be used to support creation of certificate authorities. A trust signature indicates both that the key belongs to its claimed owner and that the owner of the key is trustworthy to sign other keys at one level below their own. A level 0 signature is comparable to a web of trust signature since only the validity of the key is certified. A level 1 signature is similar to the trust one has in a certificate authority because a key signed to level 1 is able to issue an unlimited number of level 0 signatures. A level 2 signature is highly analogous to the trust assumption users must rely on whenever they use the default certificate authority list (like those included in web browsers); it allows the owner of the key to make other keys certificate authorities.
PGP versions have always included a way to cancel ('revoke') identity certificates. A lost or compromised private key will require this if communication security is to be retained by that user. This is, more or less, equivalent to the certificate revocation lists of centralised PKI schemes. Recent PGP versions have also supported certificate expiration dates.
The problem of correctly identifying a public key as belonging to a particular user is not unique to PGP. All public key/private key cryptosystems have the same problem, even if in slightly different guises, and no fully satisfactory solution is known. PGP's original scheme at least leaves the decision as to whether or not to use its endorsement/vetting system to the user, while most other PKI schemes do not, requiring instead that every certificate attested to by a central certificate authority be accepted as correct.
Security quality[edit]
To the best of publicly available information, there is no known method which will allow a person or group to break PGP encryption by cryptographic, or computational means. Indeed, in 1995, cryptographerBruce Schneier characterized an early version as being "the closest you're likely to get to military-grade encryption."[5] Early versions of PGP have been found to have theoretical vulnerabilities and so current versions are recommended.[6] In addition to protecting data in transit over a network, PGP encryption can also be used to protect data in long-term data storage such as disk files. These long-term storage options are also known as data at rest, i.e. data stored, not in transit.
The cryptographic security of PGP encryption depends on the assumption that the algorithms used are unbreakable by direct cryptanalysis with current equipment and techniques.
In the original version, the RSA algorithm was used to encrypt session keys. RSA's security depends upon the one-way function nature of mathematical integer factoring.[7] Similarly, the symmetric key algorithm used in PGP version 2 was IDEA, which might at some point in the future be found to have previously undetected cryptanalytic flaws. Specific instances of current PGP or IDEA insecurities (if they exist) are not publicly known. As current versions of PGP have added additional encryption algorithms, their cryptographic vulnerability varies with the algorithm used. However, none of the algorithms in current use are publicly known to have cryptanalytic weaknesses.
New versions of PGP are released periodically and vulnerabilities fixed by developers as they come to light. Any agency wanting to read PGP messages would probably use easier means than standard cryptanalysis, e.g. rubber-hose cryptanalysis or black-bag cryptanalysis (e.g. installing some form of trojan horse or keystroke logging software/hardware on the target computer to capture encrypted keyrings and their passwords). The FBI has already used this attack against PGP[8][9] in its investigations. However, any such vulnerabilities apply not just to PGP but to any conventional encryption software.
In 2003, an incident involving seized PsionPDAs belonging to members of the Red Brigade indicated that neither the Italian police nor the FBI were able to decrypt PGP-encrypted files stored on them.[10][unreliable source?]
A second incident in December 2006, (see In re Boucher), involving US customs agents who seized a laptop PC that allegedly contained child pornography, indicates that US government agencies find it "nearly impossible" to access PGP-encrypted files. Additionally, a magistrate judge ruling on the case in November 2007 has stated that forcing the suspect to reveal his PGP passphrase would violate his Fifth Amendment rights i.e. a suspect's constitutional right not to incriminate himself.[11][12] The Fifth Amendment issue was opened again as the government appealed the case, after which a federal district judge ordered the defendant to provide the key.[13]
Evidence suggests that as of 2007[update], British police investigators are unable to break PGP,[14] so instead have resorted to using RIPA legislation to demand the passwords/keys. In November 2009 a British citizen was convicted under RIPA legislation and jailed for nine months for refusing to provide police investigators with encryption keys to PGP-encrypted files.[15]
PGP as a cryptosystem has been criticized for complexity of the standard, implementation and very low usability of the user interface[16] including by recognized figures in cryptography research.[17][18] It uses an ineffective serialization format for storage of both keys and encrypted data, which resulted in signature-spamming attacks on public keys of prominent developers of GNU Privacy Guard. Backwards compatibility of the OpenPGP standard results in usage of relatively weak default choices of cryptographic primitives (CAST5 cipher, CFB mode, S2K password hashing).[19] The standard has been also criticized for leaking metadata, usage of long-term keys and lack of forward secrecy. Popular end-user implementations have suffered from various signature-striping, cipher downgrade and metadata leakage vulnerabilities which have been attributed to the complexity of the standard.[20]
History[edit]
Early history[edit]
Phil Zimmermann created the first version of PGP encryption in 1991. The name, "Pretty Good Privacy" was inspired by the name of a grocery store, "Ralph's Pretty Good Grocery", featured in radio host Garrison Keillor's fictional town, Lake Wobegon.[21] This first version included a symmetric-key algorithm that Zimmermann had designed himself, named BassOmatic after a Saturday Night Live sketch. Zimmermann had been a long-time anti-nuclear activist, and created PGP encryption so that similarly inclined people might securely use BBSs and securely store messages and files. No license fee was required for its non-commercial use, and the complete source code was included with all copies.
In a posting of June 5, 2001, entitled "PGP Marks 10th Anniversary",[22] Zimmermann describes the circumstances surrounding his release of PGP:
It was on this day in 1991 that I sent the first release of PGP to a couple of my friends for uploading to the Internet. First, I sent it to Allan Hoeltje, who posted it to Peacenet, an ISP that specialized in grassroots political organizations, mainly in the peace movement. Peacenet was accessible to political activists all over the world. Then, I uploaded it to Kelly Goen, who proceeded to upload it to a Usenet newsgroup that specialized in distributing source code. At my request, he marked the Usenet posting as "US only". Kelly also uploaded it to many BBS systems around the country. I don't recall if the postings to the Internet began on June 5th or 6th. It may be surprising to some that back in 1991, I did not yet know enough about Usenet newsgroups to realize that a "US only" tag was merely an advisory tag that had little real effect on how Usenet propagated newsgroup postings. I thought it actually controlled how Usenet routed the posting. But back then, I had no clue how to post anything on a newsgroup, and didn't even have a clear idea what a newsgroup was.
PGP found its way onto the Internet and rapidly acquired a considerable following around the world. Users and supporters included dissidents in totalitarian countries (some affecting letters to Zimmermann have been published, some of which have been included in testimony before the US Congress), civil libertarians in other parts of the world (see Zimmermann's published testimony in various hearings), and the 'free communications' activists who called themselves cypherpunks (who provided both publicity and distribution); decades later, CryptoParty activists did much the same via Twitter.
Criminal investigation[edit]
Shortly after its release, PGP encryption found its way outside the United States, and in February 1993 Zimmermann became the formal target of a criminal investigation by the US Government for "munitions export without a license". At the time, cryptosystems using keys larger than 40 bits were considered munitions within the definition of the US export regulations; PGP has never used keys smaller than 128 bits, so it qualified at that time. Penalties for violation, if found guilty, were substantial. After several years, the investigation of Zimmermann was closed without filing criminal charges against him or anyone else.
Zimmermann challenged these regulations in an imaginative way. He published the entire source code of PGP in a hardback book,[23] via MIT Press, which was distributed and sold widely. Anybody wishing to build their own copy of PGP could cut off the covers, separate the pages, and scan them using an OCR program (or conceivably enter it as a type-in program if OCR software was not available), creating a set of source code text files. One could then build the application using the freely available GNU Compiler Collection. PGP would thus be available anywhere in the world. The claimed principle was simple: export of munitions—guns, bombs, planes, and software—was (and remains) restricted; but the export of books is protected by the First Amendment. The question was never tested in court with respect to PGP. In cases addressing other encryption software, however, two federal appeals courts have established the rule that cryptographic software source code is speech protected by the First Amendment (the Ninth Circuit Court of Appeals in the Bernstein case and the Sixth Circuit Court of Appeals in the Junger case).
US export regulations regarding cryptography remain in force, but were liberalized substantially throughout the late 1990s. Since 2000, compliance with the regulations is also much easier. PGP encryption no longer meets the definition of a non-exportable weapon, and can be exported internationally except to seven specific countries and a list of named groups and individuals[24] (with whom substantially all US trade is prohibited under various US export controls).
PGP 3 and founding of PGP Inc.[edit]
During this turmoil, Zimmermann's team worked on a new version of PGP encryption called PGP 3. This new version was to have considerable security improvements, including a new certificate structure which fixed small security flaws in the PGP 2.x certificates as well as permitting a certificate to include separate keys for signing and encryption. Furthermore, the experience with patent and export problems led them to eschew patents entirely. PGP 3 introduced use of the CAST-128 (a.k.a. CAST5) symmetric key algorithm, and the DSA and ElGamal asymmetric key algorithms, all of which were unencumbered by patents.
After the Federal criminal investigation ended in 1996, Zimmermann and his team started a company to produce new versions of PGP encryption. They merged with Viacrypt (to whom Zimmermann had sold commercial rights and who had licensed RSA directly from RSADSI), which then changed its name to PGP Incorporated. The newly combined Viacrypt/PGP team started work on new versions of PGP encryption based on the PGP 3 system. Unlike PGP 2, which was an exclusively command line program, PGP 3 was designed from the start as a software library allowing users to work from a command line or inside a GUI environment. The original agreement between Viacrypt and the Zimmermann team had been that Viacrypt would have even-numbered versions and Zimmermann odd-numbered versions. Viacrypt, thus, created a new version (based on PGP 2) that they called PGP 4. To remove confusion about how it could be that PGP 3 was the successor to PGP 4, PGP 3 was renamed and released as PGP 5 in May 1997.
Network Associates acquisition[edit]
In December 1997, PGP Inc. was acquired by Network Associates, Inc. ("NAI"). Zimmermann and the PGP team became NAI employees. NAI was the first company to have a legal export strategy by publishing source code. Under NAI, the PGP team added disk encryption, desktop firewalls, intrusion detection, and IPsecVPNs to the PGP family. After the export regulation liberalizations of 2000 which no longer required publishing of source, NAI stopped releasing source code.[25]
In early 2001, Zimmermann left NAI. He served as Chief Cryptographer for Hush Communications, who provide an OpenPGP-based e-mail service, Hushmail. He has also worked with Veridis and other companies. In October 2001, NAI announced that its PGP assets were for sale and that it was suspending further development of PGP encryption. The only remaining asset kept was the PGP E-Business Server (the original PGP Commandline version). In February 2002, NAI canceled all support for PGP products, with the exception of the renamed commandline product. NAI (formerly McAfee, then Intel Security, and now McAfee again) continued to sell and support the product under the name McAfee E-Business Server until 2013.[26][27][28]
PGP Corporation and Symantec[edit]
In August 2002, several ex-PGP team members formed a new company, PGP Corporation, and bought the PGP assets (except for the command line version) from NAI. The new company was funded by Rob Theis of Doll Capital Management (DCM) and Terry Garnett of Venrock Associates. PGP Corporation supported existing PGP users and honored NAI's support contracts. Zimmermann served as a special advisor and consultant to PGP Corporation while continuing to run his own consulting company. In 2003, PGP Corporation created a new server-based product called PGP Universal. In mid-2004, PGP Corporation shipped its own command line version called PGP Command Line, which integrated with the other PGP Encryption Platform applications. In 2005, PGP Corporation made its first acquisition: the German software company Glück & Kanja Technology AG,[29] which became PGP Deutschland AG.[30] In 2010, PGP Corporation acquired Hamburg-based certificate authority TC TrustCenter and its parent company, ChosenSecurity, to form its PGP TrustCenter[31] division.[32]
After the 2002 purchase of NAI's PGP assets, PGP Corporation offered worldwide PGP technical support from its offices in Draper, Utah; Offenbach, Germany; and Tokyo, Japan.
On April 29, 2010, Symantec Corp. announced that it would acquire PGP for $300 million with the intent of integrating it into its Enterprise Security Group.[33] This acquisition was finalized and announced to the public on June 7, 2010. The source code of PGP Desktop 10 is available for peer review.[34]
Also in 2010, Intel Corporation acquired McAfee. In 2013, the McAfee E-Business Server was transferred to Software Diversified Services, which now sells, supports, and develops it under the name SDS E-Business Server.[26][27]
For the enterprise, Townsend Security currently offers a commercial version of PGP for the IBM i and IBM z mainframe platforms. Townsend Security partnered with Network Associates in 2000 to create a compatible version of PGP for the IBM i platform. Townsend Security again ported PGP in 2008, this time to the IBM z mainframe. This version of PGP relies on free z/OS encryption facility, which utilizes hardware acceleration. Software Diversified Services also offers a commercial version of PGP (SDS E-Business Server) for the IBM z mainframe.
In May 2018, a bug named EFAIL was discovered in certain implementations of PGP which from 2003 could reveal the plaintext contents of emails encrypted with it.[35][36]
PGP Corporation encryption applications[edit]
- This section describes commercial programs available from PGP Corporation. For information on other programs compatible with the OpenPGP specification, see External links below.
While originally used primarily for encrypting the contents of e-mail messages and attachments from a desktop client, PGP products have been diversified since 2002 into a set of encryption applications which can be managed by an optional central policy server. PGP encryption applications include e-mails and attachments, digital signatures, laptop full disk encryption, file and folder security, protection for IM sessions, batch file transfer encryption, and protection for files and folders stored on network servers and, more recently, encrypted or signed HTTP request/responses by means of a client-side (Enigform) and a server-side (mod openpgp) module. There is also a Wordpress plugin available, called wp-enigform-authentication, that takes advantage of the session management features of Enigform with mod_openpgp.
The PGP Desktop 9.x family includes PGP Desktop Email, PGP Whole Disk Encryption, and PGP NetShare. Additionally, a number of Desktop bundles are also available. Depending on application, the products feature desktop e-mail, digital signatures, IM security, whole disk encryption, file and folder security, encrypted self-extracting archives, and secure shredding of deleted files. Capabilities are licensed in different ways depending on features required.
The PGP Universal Server 2.x management console handles centralized deployment, security policy, policy enforcement, key management, and reporting. It is used for automated e-mail encryption in the gateway and manages PGP Desktop 9.x clients. In addition to its local keyserver, PGP Universal Server works with the PGP public keyserver—called the PGP Global Directory—to find recipient keys. It has the capability of delivering e-mail securely when no recipient key is found via a secure HTTPS browser session.
With PGP Desktop 9.x managed by PGP Universal Server 2.x, first released in 2005, all PGP encryption applications are based on a new proxy-based architecture. These newer versions of PGP software eliminate the use of e-mail plug-ins and insulate the user from changes to other desktop applications. All desktop and server operations are now based on security policies and operate in an automated fashion. The PGP Universal server automates the creation, management, and expiration of keys, sharing these keys among all PGP encryption applications.
The Symantec PGP platform has now undergone a rename. PGP Desktop is now known as Symantec Encryption Desktop (SED), and the PGP Universal Server is now known as Symantec Encryption Management Server (SEMS). The current shipping versions are Symantec Encryption Desktop 10.3.0 (Windows and macOS platforms) and Symantec Encryption Server 3.3.2.
Also available are PGP Command Line, which enables command line-based encryption and signing of information for storage, transfer, and backup, as well as the PGP Support Package for BlackBerry which enables RIM BlackBerry devices to enjoy sender-to-recipient messaging encryption.
New versions of PGP applications use both OpenPGP and the S/MIME, allowing communications with any user of a NIST specified standard.[citation needed]
OpenPGP[edit]
Inside PGP Inc., there was still concern about patent issues. RSADSI was challenging the continuation of the Viacrypt RSA license to the newly merged firm. The company adopted an informal internal standard they called "Unencumbered PGP" which would "use no algorithm with licensing difficulties". Because of PGP encryption's importance worldwide, many wanted to write their own software that would interoperate with PGP 5. Zimmermann became convinced that an open standard for PGP encryption was critical for them and for the cryptographic community as a whole. In July 1997, PGP Inc. proposed to the IETF that there be a standard called OpenPGP. They gave the IETF permission to use the name OpenPGP to describe this new standard as well as any program that supported the standard. The IETF accepted the proposal and started the OpenPGP Working Group.
OpenPGP is on the Internet Standards Track and is under active development. Many e-mail clients provide OpenPGP-compliant email security as described in RFC 3156. The current specification is RFC 4880 (November 2007), the successor to RFC 2440. RFC 4880 specifies a suite of required algorithms consisting of ElGamal encryption, DSA, Triple DES and SHA-1. In addition to these algorithms, the standard recommends RSA as described in PKCS #1 v1.5 for encryption and signing, as well as AES-128, CAST-128 and IDEA. Beyond these, many other algorithms are supported. The standard was extended to support Camellia cipher by RFC 5581 in 2009, and signing and key exchange based on Elliptic Curve Cryptography (ECC) (i.e. ECDSA and ECDH) by RFC 6637 in 2012. Support for ECC encryption was added by the proposed RFC 4880bis in 2014.
The Free Software Foundation has developed its own OpenPGP-compliant program called GNU Privacy Guard (abbreviated GnuPG or GPG). GnuPG is freely available together with all source code under the GNU General Public License (GPL) and is maintained separately from several Graphical User Interfaces (GUIs) that interact with the GnuPG library for encryption, decryption and signing functions (see KGPG, Seahorse, MacGPG). Several other vendors have also developed OpenPGP-compliant software.
The development of an open source OpenPGP-compliant library, OpenPGP.js,[37] written in JavaScript, has allowed web-based applications to use PGP encryption in the web browser.
OpenPGP's encryption can ensure secure delivery of files and messages, as well as provide verification of who created or sent the message using a process called digital signing. The open source office suite LibreOffice implemented document signing with OpenPGP as of version 5.4.0 on Linux.[39] Using OpenPGP for communication requires participation by both the sender and recipient. OpenPGP can also be used to secure sensitive files when they're stored in vulnerable places like mobile devices or in the cloud.[40]
Limitations[edit]
With the advancement of cryptography, parts of PGP have been criticized for being dated:
In October 2017, the ROCA vulnerability was announced, which affects RSA keys generated by buggy Infineon firmware used on Yubikey 4 tokens, often used with PGP. Many published PGP keys were found to be susceptible.[43] Yubico offers free replacement of affected tokens.[44]
See also[edit]
References[edit]
- ^"Where to Get PGP". philzimmermann.com. Phil Zimmermann & Associates LLC. February 28, 2006.
- ^Zimmermann, Philip R. (1999). "Why I Wrote PGP". Essays on PGP. Phil Zimmermann & Associates LLC.
- ^Furley, Paul M. "PGP public key example". There are shorter ways of referring to PGP keys. Archived from the original on December 21, 2018.
- ^Marcia Hofmann [@marciahofmann] (January 20, 2015). "my new business card (with image)" (Tweet). Retrieved July 30, 2020 – via Twitter.
- ^Schneier, Bruce (October 9, 1995). Applied Cryptography. New York: Wiley. p. 587. ISBN .
- ^Messmer, Ellen (August 28, 2000). "Security flaw found in Network Associates' PGP". Network World. Vol. 17 no. 35. Southbourough, Massachusetts: IDG. p. 81 – via Google Books.
- ^Nichols, Randall (1999). ICSA Guide to Cryptography. McGrawHill. p. 267. ISBN .
- ^"United States v. Scarfo (Key-Logger Case)". Epic.org. Retrieved February 8, 2010.
- ^McCullagh, Declan (July 10, 2007). "Feds use keylogger to thwart PGP, Hushmail | Tech news blog - CNET News.com". News.com. Archived from the original on March 24, 2017. Retrieved February 8, 2010.
- ^Grigg, Ian (2003). "PGP Encryption Proves Powerful".
- ^McCullagh, Declan (December 14, 2007). "Judge: Man can't be forced to divulge encryption passphrase | The Iconoclast - politics, law, and technology - CNET News.com". News.com. Retrieved February 8, 2010.
- ^McCullagh, Declan (January 18, 2008). "Feds appeal loss in PGP compelled-passphrase case | The Iconoclast - politics, law, and technology - CNET News.com". News.com. Retrieved February 8, 2010.
- ^McCullagh, Declan (February 26, 2009). "Judge orders defendant to decrypt PGP-protected laptop". CNET news. Retrieved April 22, 2009.
- ^John Leyden (November 14, 2007). "Animal rights activist hit with RIPA key decrypt demand". The Register.
- ^Chris Williams (November 24, 2009). "UK jails schizophrenic for refusal to decrypt files". The Register. p. 2.
- ^Staff, Ars (December 10, 2016). "Op-ed: I'm throwing in the towel on PGP, and I work in security". Ars Technica. Retrieved July 17, 2019.
- ^"What's the matter with PGP?". A Few Thoughts on Cryptographic Engineering. August 13, 2014. Retrieved July 17, 2019.
- ^moxie.orghttps://moxie.org/blog/gpg-and-me/. Retrieved July 17, 2019.Missing or empty (help)
- ^"Latacora - The PGP Problem". latacora.micro.blog. Retrieved July 17, 2019.
- ^"Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels"(PDF).
- ^Holtsnider, Bill; Jaffe, Brian D. (2006). IT manager's handbook: getting your new job done (2nd ed.). Morgan Kaufmann. p. 373. ISBN .
- ^"PGP Marks 10th Anniversary". Phil Zimmermann. Retrieved August 23, 2010.
- ^Zimmermann, Philip (1995). PGP Source Code and Internals. MIT Press. ISBN .
- ^"Lists to Check". US Department of Commerce, Bureau of Industry and Security. Archived from the original on January 12, 2010. Retrieved December 4, 2011.
- ^"Important Information About PGP & Encryption". proliberty.com. Retrieved March 24, 2015.
- ^ ab"McAfee partners with Software Diversified Services to deliver E-Business Server sales and support." 2014-01-17. Retrieved 2015-06-30.
- ^ ab"Long Live E-Business Server for Enterprise-Scale Encryption." Software Diversified Services. 2013-08-11. Retrieved 2015-06-30.
- ^"Intel Security is McAfee again." 2017-04-03. Retrieved 2018-01-08.
- ^"glueckkanja.com". glueckkanja.com. Retrieved August 6, 2013.
- ^"pgp.de". pgp.de. Retrieved August 6, 2013.
- ^"pgptrustcenter.com". pgptrustcenter.com. January 26, 2010. Archived from the original on January 9, 2014. Retrieved August 6, 2013.
- ^"News Room – Symantec Corp". Pgp.com. Retrieved March 23, 2012.
- ^"Symantec buys encryption specialist PGP for $300M". Computerworld. April 29, 2010. Retrieved April 29, 2010.
- ^"Symantec PGP Desktop Peer Review Source Code". Symantec.com. September 23, 2012. Retrieved August 6, 2013.
- ^"Critical PGP and S/MIME bugs can reveal encrypted emails—uninstall now [Updated]". arstechnica.com. May 14, 2018.
- ^"EFAIL". efail.de. Retrieved May 18, 2018.
- ^OpenPGPjs-Team. "OpenPGPjs".
- ^ abDavid, Shaw; Lutz, Donnerhacke; Rodney, Thayer; Hal, Finney; Jon, Callas. "OpenPGP Message Format". tools.ietf.org.
- ^"OpenPGP signature support in LibreOffice". Thorsten's Weblog. July 28, 2017. Retrieved December 10, 2017.
Privileged Access Workstations
Applies To: Windows Server
Privileged Access Workstations (PAWs) provide a dedicated operating system for sensitive tasks that is protected from Internet attacks and threat vectors. Separating these sensitive tasks and accounts from the daily use workstations and devices provides very strong protection from phishing attacks, application and OS vulnerabilities, various impersonation attacks, and credential theft attacks such as keystroke logging, Pass-the-Hash, and Pass-The-Ticket.
What is a Privileged Access Workstation?
In simplest terms, a PAW is a hardened and locked down workstation designed to provide high security assurances for sensitive accounts and tasks. PAWs are recommended for administration of identity systems, cloud services, and private cloud fabric as well as sensitive business functions.
Note
The PAW architecture doesn't require a 1:1 mapping of accounts to workstations, though this is a common configuration. PAW creates a trusted workstation environment that can be used by one or more accounts.
In order to provide the greatest security, PAWs should always run the most up-to-date and secure operating system available: Microsoft strongly recommends Windows 10 Enterprise, which includes several additional security features not available in other editions (in particular, Credential Guard and Device Guard).
Note
Organizations without access to Windows 10 Enterprise can use Windows 10 Pro, which includes many of the critical foundational technologies for PAWs, including Trusted Boot, BitLocker, and Remote Desktop. Education customers can use Windows 10 Education. Windows 10 Home should not be used for a PAW.
For a comparison matrix of the different editions of Windows 10, read this article.
The PAW security controls are focused on mitigating high impact and high probability risks of compromise. These include mitigating attacks on the environment and risks that can decrease the effectiveness of PAW controls over time:
- Internet attacks - Most attacks originate directly or indirectly from internet sources and use the internet for exfiltration and command and control (C2). Isolating the PAW from the open internet is a key element to ensuring the PAW is not compromised.
- Usability risk - If a PAW is too difficult to use for daily tasks, administrators will be motivated to create workarounds to make their jobs easier. Frequently, these workarounds open the administrative workstation and accounts to significant security risks, so it's critical to involve and empower the PAW users to mitigate these usability issues securely. This can be accomplished by listening to their feedback, installing tools and scripts required to perform their jobs, and ensuring all administrative personnel are aware of why they need to use a PAW, what a PAW is, and how to use it correctly and successfully.
- Environment risks - Because many other computers and accounts in the environment are exposed to internet risk directly or indirectly, a PAW must be protected against attacks from compromised assets in the production environment. This requires minimizing the use of management tools and accounts that have access to the PAWs to secure and monitor these specialized workstations.
- Supply chain tampering - While it's impossible to remove all possible risks of tampering in the supply chain for hardware and software, taking a few key actions can mitigate critical attack vectors that are readily available to attackers. This includes validating the integrity of all installation media (Clean Source Principle) and using a trusted and reputable supplier for hardware and software.
- Physical attacks - Because PAWs can be physically mobile and used outside of physically secure facilities, they must be protected against attacks that leverage unauthorized physical access to the computer.
Note
A PAW will not protect an environment from an adversary that has already gained administrative access over an Active Directory Forest. Because many existing implementations of Active Directory Domain Services have been operating for years at risk of credential theft, organizations should assume breach and consider the possibility that they may have an undetected compromise of domain or enterprise administrator credentials. An organization that suspects domain compromise should consider the use of professional incident response services.
For more information on response and recovery guidance, see the "Respond to suspicious activity" and "Recover from a breach" sections of Mitigating Pass-the-Hash and Other Credential Theft, version 2.
Visit Microsoft's Incident Response and Recovery services page for more information.
PAW hardware profiles
Administrative personnel are standard users too - they need a PAW as well as a standard user workstation to check email, browse the web, and access corporate line of business applications. Ensuring that administrators can remain both productive and secure is essential to the success of any PAW deployment. A secure solution that dramatically limits productivity will be abandoned by the users in favor of one that enhances productivity (even if it is done in an insecure manner).
In order to balance the need for security with the need for productivity, Microsoft recommends using one of these PAW hardware profiles:
- Dedicated hardware - Separate dedicated devices for user tasks vs. administrative tasks.
- Simultaneous Use - Single device that can run user tasks and administrative tasks concurrently by taking advantage of OS or presentation virtualization.
Organizations may use only one profile or both. There are no interoperability concerns between the hardware profiles, and organizations have the flexibility to match the hardware profile to the specific need and situation of a given administrator.
Note
It is critical that, in all these scenarios, administrative personnel are issued a standard user account that is separate from designated administrative account(s). The administrative account(s) should only be used on the PAW administrative operating system.
This table summarizes the relative advantages and disadvantages of each hardware profile from the perspective of operational ease-of-use and productivity and security. Both hardware approaches provide strong security for administrative accounts against credential theft and reuse.
| Scenario | Advantages | Disadvantages |
|---|---|---|
| Dedicated hardware | - Strong signal for sensitivity of tasks - Strongest security separation | - Additional desk space - Additional weight (for remote work) - Hardware Cost |
| Simultaneous use | - Lower hardware cost - Single device experience | - Sharing single keyboard/mouse creates risk of inadvertent errors/risks |
This guidance contains the detailed instructions for the PAW configuration for the dedicated hardware approach. If you have requirements for the simultaneous use hardware profiles, you can adapt the instructions based on this guidance yourself or hire a professional services organization like Microsoft to assist with it.
Dedicated hardware
In this scenario, a PAW is used for administration that is completely separate from the PC that is used for daily activities like email, document editing, and development work. All administrative tools and applications are installed on the PAW and all productivity applications are installed on the standard user workstation. The step by step instructions in this guidance are based on this hardware profile.
Simultaneous use - Adding a local user VM
In this simultaneous use scenario, a single PC is used for both administration tasks and daily activities like email, document editing, and development work. In this configuration, the user operating system is available while disconnected (for editing documents and working on locally cached email), but requires hardware and support processes that can accommodate this disconnected state.

The physical hardware runs two operating systems locally:
- Admin OS - The physical host runs Windows 10 on the PAW host for Administrative tasks
- User OS - A Windows 10 client Hyper-V virtual machine guest runs a corporate image
With Windows 10 Hyper-V, a guest virtual machine (also running Windows 10) can have a rich user experience including sound, video, and Internet communications applications such as Skype for Business.
In this configuration, daily work that does not require administrative privileges is done in the user OS virtual machine which has a regular corporate Windows 10 image and is not subject to restrictions applied to the PAW host. All administrative work is done on the Admin OS.
To configure this, follow the instructions in this guidance for the PAW host, add Client Hyper-V features, create a User VM, and then install a Windows 10 corporate image on the User VM.
Read Client Hyper-V article for more information about this capability. Please note that the operating system in guest virtual machines will need to be licensed per Microsoft product licensing, also described here.
Simultaneous use - Adding RemoteApp, RDP, or a VDI
In this simultaneous use scenario, a single PC is used for both administration tasks and daily activities like email, document editing and development work. In this configuration, the user operating systems are deployed and managed centrally (on the cloud or in your datacenter), but aren't available while disconnected.

The physical hardware runs a single PAW operating system locally for administrative tasks and contacts a Microsoft or 3rd party remote desktop service for user applications such as email, document editing, and line of business applications.
In this configuration, daily work that does not require administrative privileges is done in the Remote OS(es) and applications which are not subject to restrictions applied to the PAW host. All administrative work is done on the Admin OS.
To configure this, follow the instructions in this guidance for the PAW host, allow network connectivity to the Remote Desktop services, and then add shortcuts to the PAW user's desktop to access the applications. The remote desktop services could be hosted in many ways including:
- An existing Remote Desktop or VDI service (on-premises or in the cloud)
- A new service you install on-premises or in the cloud
- Azure RemoteApp using pre-configured Office 365 templates or your own installation images
For more information on Azure RemoteApp, visit this page.
How Microsoft is using administrative workstations
Microsoft uses the PAW architectural approach both internally on our systems as well as with our customers. Microsoft uses administrative workstations internally in several capacities including administration of Microsoft IT infrastructure, Microsoft cloud fabric infrastructure development and operations, and other high value assets.
This guidance is directly based on the Privileged Access Workstation (PAW) reference architecture deployed by our cybersecurity professional services teams to protect customers against cybersecurity attacks. The administrative workstations are also a key element of the strongest protection for domain administration tasks, the Enhanced Security Administrative Environment (ESAE) administrative forest reference architecture.
For more details on the ESAE administrative forest, see the ESAE Administrative Forest Design Approach section in Securing Privileged Access Reference Material.
Architecture overview
The diagram below depicts a separate "channel" for administration (a highly sensitive task) that is created by maintaining separate dedicated administrative accounts and workstations.

This architectural approach builds on the protections found in the Windows 10 Credential Guard and Device Guard features and goes beyond those protections for sensitive accounts and tasks.
This methodology is appropriate for accounts with access to high value assets:
Administrative Privileges - PAWs provide increased security for high impact IT administrative roles and tasks. This architecture can be applied to administration of many types of systems including Active Directory Domains and Forests, Microsoft Azure Active Directory tenants, Office 365 tenants, Process Control Networks (PCN), Supervisory Control and Data Acquisition (SCADA) systems, Automated Teller Machines (ATMs), and Point of Sale (PoS) devices.
High Sensitivity Information workers - The approach used in a PAW can also provide protection for highly sensitive information worker tasks and personnel such as those involving pre-announcement Merger and Acquisition activity, pre-release financial reports, organizational social media presence, executive communications, unpatented trade secrets, sensitive research, or other proprietary or sensitive data. This guidance does not discuss the configuration of these information worker scenarios in depth or include this scenario in the technical instructions.
Note
Microsoft IT uses PAWs (internally referred to as "secure admin workstations", or SAWs) to manage secure access to internal high-value systems within Microsoft. This guidance has additional details below on PAW usage at Microsoft in the section "How Microsoft uses admin workstations". For more detailed information on this high value asset environment approach, please refer to the article, Protecting high-value assets with secure admin workstations.
This document will describe why this practice is recommended for protecting high impact privileged accounts, what these PAW solutions look like for protecting administrative privileges, and how to quickly deploy a PAW solution for domain and cloud services administration.
This document provides detailed guidance for implementing several PAW configurations and includes detailed implementation instructions to get you started on protecting common high impact accounts:
Why dedicated workstations?
The current threat environment for organizations is rife with sophisticated phishing and other internet attacks that create continuous risk of security compromise for internet exposed accounts and workstations.
This threat environment requires organizations to adopt an "assume breach" security posture when designing protections for high value assets like administrative accounts and sensitive business assets. These high value assets need to be protected against both direct internet threats as well as attacks mounted from other workstations, servers, and devices in the environment.
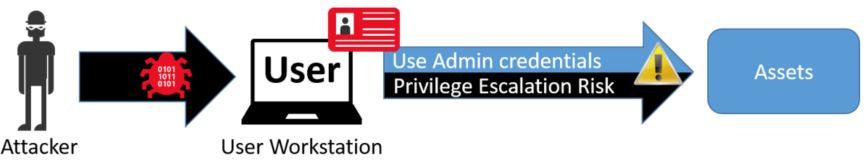
This figure depicts risk to managed assets if an attacker gains control of a user workstation where sensitive credentials are used.
An attacker in control of an operating system has numerous ways in which to illicitly gain access to all activity on the workstation and impersonate the legitimate account. A variety of known and unknown attack techniques can be used to gain this level of access. The increasing volume and sophistication of cyberattacks have made it necessary to extend that separation concept to completely separate client operating systems for sensitive accounts. For more information on these types of attacks, please visit the Pass The Hash web site for informative white papers, videos and more.
The PAW approach is an extension of the well-established recommended practice to use separate admin and user accounts for administrative personnel. This practice uses an individually assigned administrative account that is completely separate from the user's standard user account. PAW builds on that account separation practice by providing a trustworthy workstation for those sensitive accounts.
This PAW guidance is intended to help you implement this capability for protecting high value accounts such as high-privileged IT administrators and high sensitivity business accounts. The guidance helps you:
- Restrict exposure of credentials to only trusted hosts
- Provide a high-security workstation to administrators so they can easily perform administrative tasks.
Restricting the sensitive accounts to using only hardened PAWs is a straightforward protection for these accounts that is both highly usable for administrators and very difficult for an adversary to defeat.
Alternate approaches
This section contains information on how the security of alternate approaches compares to PAW and how to correctly integrate these approaches within a PAW architecture. all these approaches carry significant risks when implemented in isolation, but can add value to a PAW implementation in some scenarios.
Credential Guard and Windows Hello for Business
Introduced in Windows 10, Credential Guard uses hardware and virtualization-based security to mitigate common credential theft attacks, such as Pass-the-Hash, by protecting the derived credentials. The private key for credentials used by Windows Hello for Business can be also be protected by Trusted Platform Module (TPM) hardware.
These are powerful mitigations, but workstations can still be vulnerable to certain attacks even if the credentials are protected by Credential Guard or Windows Hello for Business. Attacks can include abusing privileges and use of credentials directly from a compromised device, reusing previously stolen credentials prior to enabling Credential Guard and abuse of management tools and weak application configurations on the workstation.
The PAW guidance in this section includes the use of many of these technologies for high sensitivity accounts and tasks.
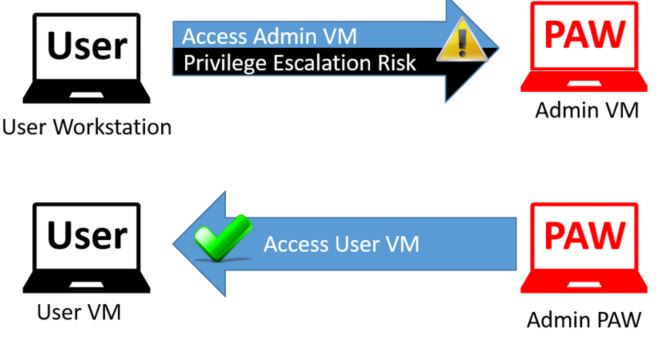
Administrative VM
An administrative virtual machine (Admin VM) is a dedicated operating system for administrative tasks hosted on a standard user desktop. While this approach is similar to PAW in providing a dedicated OS for administrative tasks, it has a fatal flaw in that the administrative VM is dependent on the standard user desktop for its security.
The diagram below depicts the ability of attackers to follow the control chain to the target object of interest with an Admin VM on a User Workstation and that it is difficult to create a path on the reverse configuration.
The PAW architecture does not allow for hosting an Admin VM on a User Workstation, but a User VM with a standard corporate image can be hosted on an Admin PAW to provide personnel with a single PC for all responsibilities.
Shielded VM-based PAWs
A secure variant of the administrative VM model is to use shielded virtual machines to host one or more admin VMs alongside a user VM. Shielded VMs are designed to run secure workloads in an environment where potentially untrusted users or code may be running on the physical machine's standard user desktop. A shielded VM has a virtual TPM which allows it to encrypt its own data at rest, and several administrative controls such as basic console access, PowerShell Direct, and the ability to debug the VM are disabled to further isolate the VM from the standard user desktop and other VMs. The keys for a shielded VM are stored on a trusted key management server, which requires the physical device to attest to its identity and health before releasing a key to start the VM. This ensures that shielded VMs can only start on the intended devices and that those devices are running known and trusted software configurations.
Because the shielded VMs are isolated from each other and the standard user desktop, it is acceptable to run multiple shielded PAW VMs on a single host, even when those admin VMs manage different tiers.
See the deploy PAWs using a guarded fabric section below for more information.
Jump server
Administrative "Jump Server" architectures set up a small number administrative console servers and restrict personnel to using them for administrative tasks. This is typically based on remote desktop services, a 3rd-party presentation virtualization solution, or a Virtual Desktop Infrastructure (VDI) technology.
This approach is frequently proposed to mitigate risk to administration and does provide some security assurances, but the jump server approach by itself is vulnerable to certain attacks because it violates the "clean source" principle. The clean source principle requires all security dependencies to be as trustworthy as the object being secured.

This figure depicts a simple control relationship. Any subject in control of an object is a security dependency of that object. If an adversary can control a security dependency of a target object (subject), they can control that object.
The administrative session on the jump server relies on the integrity of the local computer accessing it. If this computer is a user workstation subject to phishing attacks and other internet-based attack vectors, then the administrative session is also subject to those risks.

The figure above depicts how attackers can follow an established control chain to the target object of interest.
While some advanced security controls like multi-factor authentication can increase the difficulty of an attacker taking over this administrative session from the user workstation, no security feature can fully protect against technical attacks when an attacker has administrative access of the source computer (e.g. injecting illicit commands into a legitimate session, hijacking legitimate processes, and so on.)
The default configuration in this PAW guidance installs administrative tools on the PAW, but a jump server architecture can also be added if required.

This figure shows how reversing the control relationship and accessing user apps from an admin workstation gives the attacker no path to the targeted object. The user jump server is still exposed to risk so appropriate protective controls, detective controls, and response processes should still be applied for that internet-facing computer.
This configuration requires administrators to follow operational practices closely to ensure that they don't accidentally enter administrator credentials into the user session on their desktop.
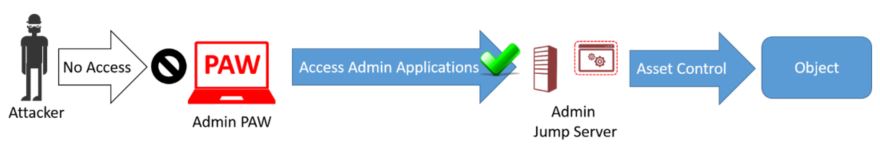
This figure shows how accessing an administrative jump server from a PAW adds no path for the attacker into the administrative assets. A jump server with a PAW allows in this case you to consolidate the number of locations for monitoring administrative activity and distributing administrative applications and tools. This adds some design complexity, but can simplify security monitoring and software updates if a large number of accounts and workstations are used in your PAW implementation. The jump server would need to be built and configured to similar security standards as the PAW.
Privilege management solutions
Privileged Management solutions are applications that provide temporary access to discrete privileges or privileged accounts on demand. Privilege management solutions are an extremely valuable component of a complete strategy to secure privileged access and provide critically important visibility and accountability of administrative activity.
These solutions typically use a flexible workflow to grant access and many have additional security features and capabilities like service account password management and integration with administrative jump servers. There are many solutions on the market that provide privilege management capabilities, one of which is Microsoft Identity Manager (MIM) privileged access management (PAM).
Microsoft recommends using a PAW to access privilege management solutions. Access to these solutions should be granted only to PAWs. Microsoft does not recommend using these solutions as a substitute for a PAW because accessing privileges using these solutions from a potentially compromised user desktop violates the clean source principle as depicted in the diagram below:

Providing a PAW to access these solutions enables you to gain the security benefits of both PAW and the privilege management solution, as depicted in this diagram:

Note
These systems should be classified at the highest tier of the privilege they manage and be protected at or above that level of security. These are commonly configured to manage Tier 0 solutions and Tier 0 assets and should be classified at Tier 0. For more information on the tier model, see https://aka.ms/tiermodel For more information on Tier 0 groups, see Tier 0 equivalency in Securing Privileged Access Reference Material.
For more information on deploying Microsoft Identity Manager (MIM) privileged access management (PAM), see https://aka.ms/mimpamdeploy
PAW Scenarios
This section contains guidance on which scenarios this PAW guidance should be applied to. In all scenarios, administrators should be trained to only use PAWs for performing support of remote systems. To encourage successful and secure usage, all PAW users should be also be encouraged to provide feedback to improve the PAW experience and this feedback should be reviewed carefully for integration with your PAW program.
In all scenarios, additional hardening in later phases and different hardware profiles in this guidance may be used to meet the usability or security requirements of the roles.
Note
This guidance explicitly differentiates between requiring access to specific services on the internet (such as Azure and Office 365 administrative portals) and the "Open Internet" of all hosts and services.
See the Tier model page for more information on the Tier designations.
| Scenarios | Use PAW? | Scope and Security Considerations |
|---|---|---|
| Active Directory Admins - Tier 0 | Yes | A PAW built with Phase 1 guidance is sufficient for this role. - An administrative forest can be added to provide the strongest protection for this scenario. For more information on the ESAE administrative forest, see ESAE Administrative Forest Design Approach |
| Admin of Azure IaaS and PaaS services - Tier 0 or Tier 1 (see Scope and Design Considerations) | Yes | A PAW built using the guidance provided in Phase 2 is sufficient for this role. - PAWs should be used for at least the Global administrator and Subscription Billing administrator. You should also use PAWs for delegated administrators of critical or sensitive servers. |
| Admin Office 365 Tenant - Tier 1 | Yes | A PAW built using the guidance provided in Phase 2 is sufficient for this role. - PAWs should be used for at least the Subscription Billing administrator, Global administrator, Exchange administrator, SharePoint administrator, and User management administrator roles. You should also strongly consider the use of PAWs for delegated administrators of highly critical or sensitive data. |
| Other IaaS or PaaS cloud service admin - Tier 0 or Tier 1 (see Scope and Design Considerations) | Yes | A PAW built using the guidance provided in Phase 2 is sufficient for this role. - PAWs should be used for any role that has administrative rights over cloud hosted VMs including the ability to install agents, export hard disk files, or access storage where hard drives with operating systems, sensitive data, or business critical data is stored. |
| Virtualization Administrators - Tier 0 or Tier 1 (see Scope and Design Considerations) | Yes | A PAW built using the guidance provided in Phase 2 is sufficient for this role. - PAWs should be used for any role that has administrative rights over VMs including the ability to install agents, export virtual hard disk files, or access storage where hard drives with guest operating system information, sensitive data, or business critical data is stored. Note: A virtualization system (and its admins) are considered Tier 0 for a Forest if Domain Controllers or other Tier 0 hosts are in the subscription. A subscription is Tier 1 if no Tier 0 servers are hosted in the virtualization system. |
| Server Maintenance Admins - Tier 1 | Yes | A PAW built using the guidance provided in Phase 2 is sufficient for this role. - A PAW should be used for administrators that update, patch, and troubleshoot enterprise servers and apps running Windows server, Linux, and other operating systems. |
| User Workstation Admins - Tier 2 | Yes | A PAW built using guidance provided in Phase 2 is sufficient for roles that have administrative rights on end user devices (such as helpdesk and deskside support roles). - Additional applications may need to be installed on PAWs to enable ticket management and other support functions. |
| SQL, SharePoint, or line of business (LOB) Admin - Tier 1 | Yes | A PAW built with Phase 2 guidance is sufficient for this role. - Additional management tools may need to be installed on PAWs to allow administrators to manage applications without needing to connect to servers using Remote Desktop. |
| Users Managing Social Media Presence | Partially | A PAW built using the guidance provided in Phase 2 can be used as a starting point to provide security for these role. - Protect and manage social media accounts using Azure Active Directory (AAD) for sharing, protecting, and tracking access to social media accounts. |
| Standard Users | No | While many hardening steps can be used for standard users, PAW is designed to isolate accounts from the open internet access that most users require for job duties. |
| Guest VDI/Kiosk | No | While many hardening steps can be used for a kiosk system for guests, the PAW architecture is designed to provide higher security for high sensitivity accounts, not higher security for lower sensitivity accounts. |
| VIP User (Executive, Researcher, etc.) | Partially | A PAW built using guidance provided in Phase 2 can be used as a starting point to provide security for these roles. - This scenario is similar to a standard user desktop, but typically has a smaller, simpler, and well-known application profile. This scenario typically requires discovering and protecting sensitive data, services, and applications (which may or may not be installed on the desktops). |
| Industrial control systems (e.g. SCADA, PCN, and DCS) | Partially | A PAW built using guidance provided in Phase 2 can be used as a starting point to provide security for these roles as most ICS consoles (including such common standards as SCADA and PCN) don't require browsing the open Internet and checking email. - Applications used for controlling physical machinery would have to be integrated and tested for compatibility and protected appropriately. |
| Embedded Operating System | No | While many hardening steps from PAW can be used for embedded operating systems, a custom solution would need to be developed for hardening in this scenario. |
Note
Combination scenarios some personnel may have administrative responsibilities that span multiple scenarios. In these cases, the key rules to keep in mind are that the Tier model rules must always be followed. See the Tier model page for more information.
Note
Scaling the PAW Program as your PAW program scales to encompass more admins and roles, you need to continue to ensure that you maintain adherence to the security standards and usability. This may require you to update your IT support structures or create new ones to resolve PAW specific challenges such as PAW onboarding process, incident management, configuration management, and gathering feedback to address usability challenges. One example may be that your organization decides to enable work-from-home scenarios for administrators, which would necessitate a shift from desktop PAWs to laptop PAWs - a shift which may necessitate additional security considerations. Another common example is to create or update training for new administrators - training which must now include content on the appropriate use of a PAW (including why its important and what a PAW is and isn't). For more considerations which must be addressed as you scale your PAW program, see Phase 2 of the instructions.
This guidance contains the detailed instructions for the PAW configuration for the scenarios as noted above. If you have requirements for the other scenarios, you can adapt the instructions based on this guidance yourself or hire a professional services organization like Microsoft to assist with it.
For more information on engaging Microsoft services to design a PAW tailored for your environment, contact your Microsoft representative or visit this page.
PAW Phased implementation
Because the PAW must provide a secure and trusted source for administration, it's essential that the build process is secure and trusted. This section will provide detailed instructions which will allow you to build your own PAW using general principles and concepts very similar to those used by Microsoft IT and Microsoft cloud engineering and service management organizations.
The instructions are divided into three phases which focus on putting the most critical mitigations in place quickly and then progressively increasing and expanding the usage of PAW for the enterprise.
It is important to note that the phases should always be performed in order even if they are planned and implemented as part of the same overall project.
Phase 1: Immediate deployment for Active Directory administrators
Purpose: Provides a PAW quickly that can protect on-premises domain and forest administration roles.
Scope: Tier 0 Administrators including Enterprise Admins, Domain Admins (for all domains), and administrators of other authoritative identity systems.
Phase 1 focuses on the administrators who manage your on-premises Active Directory domain, which are critically important roles frequently targeted by attackers. These identity systems will work effectively for protecting these admins whether your Active Directory Domain Controllers (DCs) are hosted in on-premises datacenters, on Azure Infrastructure as a Service (IaaS), or another IaaS provider.
During this phase, you will create the secure administrative Active Directory organizational unit (OU) structure to host your privileged access workstation (PAW), as well as deploy the PAWs themselves. This structure also includes the group policies and groups required to support the PAW. You will create most of the structure using PowerShell scripts which are available at TechNet Gallery.
The scripts will create the following OUs and Security Groups:
- Organizational Units (OU)
- Six new top-level OUs: Admin; Groups; Tier 1 Servers; Workstations; User Accounts; and Computer Quarantine. Each top-level OU will contain several child OUs.
- Groups
- Six new security-enabled global groups: Tier 0 Replication Maintenance; Tier 1 Server Maintenance; Service Desk Operators; Workstation Maintenance; PAW Users; PAW Maintenance.
You will also create several group policy objects: PAW Configuration - Computer; PAW Configuration - User; RestrictedAdmin Required - Computer; PAW Outbound Restrictions; Restrict Workstation Logon; Restrict Server Logon.
Phase 1 includes the following steps:
Complete the Prerequisites
Ensure that all administrators use separate, individual accounts for administration and end user activities (including email, Internet browsing, line-of-business applications, and other non-administrative activities). Assigning an administrative account to each authorized personnel separate from their standard user account is fundamental to the PAW model, as only certain accounts will be permitted to log onto the PAW itself.
Note
Each administrator should use his or her own account for administration. Do not share an administrative account.
Minimize the number of Tier 0 privileged administrators. Because each administrator must use a PAW, reducing the number of administrators reduces the number of PAWs required to support them and the associated costs. The lower count of administrators also results in lower exposure of these privileges and associated risks. While it is possible for administrators in one location to share a PAW, administrators in separate physical locations will require separate PAWs.
Acquire hardware from a trusted supplier that meets all technical requirements. Microsoft recommends acquiring hardware that meets the technical requirements in the article Protect domain credentials with Credential Guard.
Note
PAW installed on hardware without these capabilities can provide significant protections, but advanced security features such as Credential Guard and Device Guard will not be available. Credential Guard and Device Guard are not required for Phase 1 deployment, but are strongly recommended as part of Phase 3 (advanced hardening).
Ensure that the hardware used for the PAW is sourced from a manufacturer and supplier whose security practices are trusted by the organization. This is an application of the clean source principle to supply chain security.
For more background on the importance of supply chain security, visit this site.
Acquire and validate the required Windows 10 Enterprise Edition and application software. Obtain the software required for PAW and validate it using the guidance in Clean Source for installation media.
Windows 10 Enterprise Edition
Remote Server Administration Tools for Windows 10
Windows 10 Security Baselines
Note
Microsoft publishes MD5 hashes for all operating systems and applications on MSDN, but not all software vendors provide similar documentation. In those cases, other strategies will be required. For additional information on validating software, please refer to Clean Source for installation media.
Ensure you have WSUS server available on the intranet. You will need a WSUS server on the intranet to download and install updates for PAW. This WSUS server should be configured to automatically approve all security updates for Windows 10 or an administrative personnel should have responsibility and accountability to rapidly approve software updates.
Note
For more information, see the "Automatically Approve Updates for Installation" section in the Approving Updates guidance.
Deploy the Admin OU Framework to host the PAWs
Download the PAW script library from TechNet Gallery
Note
Download all the files and save them to the same directory, and run them in the order specified below. Create-PAWGroups depends on the OU structure created by Create-PAWOUs, and Set-PAWOUDelegation depends on the groups created by Create-PAWGroups. Do not modify any of the scripts or the comma-separated value (CSV) file.
Run the Create-PAWOUs.ps1 script. This script will create the new organizational unit (OU) structure in Active Directory, and block GPO inheritance on the new OUs as appropriate.
Run the Create-PAWGroups.ps1 script. This script will create the new global security groups in the appropriate OUs.
Note
While this script will create the new security groups, it will not populate them automatically.
Run the Set-PAWOUDelegation.ps1 script. This script will assign permissions to the new OUs to the appropriate groups.
Move Tier 0 accounts to the Admin\Tier 0\Accounts OU
Move each account that is a member of the Domain Admin, Enterprise Admin, or Tier 0 equivalent groups (including nested membership) to this OU. If your organization has your own groups that are added to these groups, you should move these to the Admin\Tier 0\Groups OU.
Add the appropriate members to the relevant groups
PAW Users - Add the Tier 0 administrators with Domain or Enterprise Admin groups that you identified in Step 1 of Phase 1.
PAW Maintenance - Add at least one account that will be used for PAW maintenance and troubleshooting tasks. The PAW Maintenance Account(s) will be used only rarely.
Note
Do not add the same user account or group to both PAW Users and PAW Maintenance. The PAW security model is based partly on the assumption that the PAW user account has privileged rights on managed systems or over the PAW itself, but not both.
- This is important for building good administrative practices and habits in Phase 1.
- This is critically important for Phase 2 and beyond to prevent escalation of privilege through PAW as PAWs being to span Tiers.
Ideally, no personnel are assigned to duties at multiple tiers to enforce the principle of segregation of duties, but Microsoft recognizes that many organizations may have limited staff (or other organizational requirements) that don't allow for this full segregation. In these cases, the same personnel may be assigned to both roles, but should not use the same account for these functions.
Create "PAW Configuration - Computer" group policy object (GPO)
In this section, you will create a new "PAW Configuration - Computer" GPO which provide specific protections for these PAWs and link it to the Tier 0 Devices OU ("Devices" under Tier 0\Admin).
Note
Do not add these settings to the Default Domain Policy. Doing so will potentially impact operations on your entire Active Directory environment. Only configure these settings in the newly-created GPOs described here, and only apply them to the PAW OU.
PAW Maintenance Access - this setting will set the membership of specific privileged groups on the PAWs to a specific set of users. Go to Computer Configuration\Preferences\Control Panel Settings\Local Users and Groups and follow the steps below:
Click New and click Local Group
Select the Update action, and select "Administrators (built-in)" (do not use the Browse button to select the domain group Administrators).
Select the Delete all member users and Delete all member groups check boxes
Add PAW Maintenance (pawmaint) and Administrator (again, do not use the Browse button to select Administrator).
Note
Do not add the PAW Users group to the membership list for the local Administrators group. To ensure that PAW Users cannot accidentally or deliberately modify the security settings of the PAW itself, they should not be members of the local Administrators groups.
For more information on using Group Policy Preferences to modify group membership, please refer to the TechNet article Configure a Local Group Item.
Restrict Local Group Membership - this setting will ensure that the membership of local admin groups on the workstation is always empty
Go to Computer Configuration\Preferences\Control Panel Settings\Local Users and Groups and follow the steps below:
- Click New and click Local Group
- Select the Update action, and select "Backup Operators (built-in)" (do not use the Browse button to select the domain group Backup Operators).
- Select the Delete all member users and Delete all member groups check boxes.
- Do not add any members to the group. Simply click OK. By assigning an empty list, group policy will automatically remove all members and ensure a blank membership list each time group policy is refreshed.
Complete the above steps for the following additional groups:
- Cryptographic Operators
- Hyper-V Administrators
- Network Configuration Operators
- Power Users
- Remote Desktop Users
- Replicators
PAW Logon Restrictions - this setting will limit the accounts which can log onto the PAW. Follow the steps below to configure this setting:
- Go to Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Allow log on locally.
- Select Define these policy settings and add "PAW Users" and Administrators (again, do not use the Browse button to select Administrators).
Block Inbound Network Traffic - This setting will ensure that no unsolicited inbound network traffic is allowed to the PAW. Follow the steps below to configure this setting:
- Go to Computer Configuration\Policies\Windows Settings\Security Settings\Windows Firewall with Advanced Security\Windows Firewall with Advanced Security and follow the steps below:
Right click on Windows Firewall with Advanced Security and select Import policy.
Click Yes to accept that this will overwrite any existing firewall policies.
Browse to PAWFirewall.wfw and select Open.
Click OK.
Note
You may add addresses or subnets which must reach the PAW with unsolicited traffic at this point (e.g. security scanning or management software. The settings in the WFW file will enable the firewall in "Block - Default" mode for all firewall profiles, turn off rule merging and enable logging of both dropped and successful packets. These settings will block unsolicited traffic while still allowing bidirectional communication on connections initiated from the PAW, prevent users with local administrative access from creating local firewall rules that would override the GPO settings and ensure that traffic in and out of the PAW is logged. Opening up this firewall will expand the attack surface for the PAW and increase security risk. Before adding any addresses, consult the Managing and Operating PAW section in this guidance.
- Go to Computer Configuration\Policies\Windows Settings\Security Settings\Windows Firewall with Advanced Security\Windows Firewall with Advanced Security and follow the steps below:
Configure Windows Update for WSUS - follow the steps below to change the settings to configure Windows Update for the PAWs:
- Go to Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Updates and follow the steps below:
- Enable the Configure Automatic Updates policy.
- Select option 4 - Auto download and schedule the install.
- Change the option Scheduled install day to 0 - Every Day and the option Scheduled install time to your organizational preference.
- Enable option Specify intranet Microsoft update service location policy, and specify in both options the URL of the ESAE WSUS server.
- Go to Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Updates and follow the steps below:
Link the "PAW Configuration - Computer" GPO as follows:
Policy Link Location PAW Configuration - Computer Admin\Tier 0\Devices
Create "PAW Configuration - User" group policy object (GPO)
In this section, you will create a new "PAW Configuration - User" GPO which provide specific protections for these PAWs and link to the Tier 0 Accounts OU ("Accounts" under Tier 0\Admin).
Note
Do not add these settings to the Default Domain Policy
- Block internet browsing - To deter inadvertent internet browsing, this will set a proxy address of a loopback address (127.0.0.1).
Go to User Configuration\Preferences\Windows Settings\Registry. Right-click Registry, select New > Registry Item and configure the following settings:
Action: Replace
Hive: HKEY_CURRENT_USER
Key Path: Software\Microsoft\Windows\CurrentVersion\Internet Settings
Value name: ProxyEnable
Note
Do not select the Default box to the left of Value name.
Value type: REG_DWORD
Value data: 1
- Click the Common tab and select Remove this item when it is no longer applied.
- On the Common tab select Item level targeting and click Targeting.
- Click New Item and select Security group.
- Select the "..." button and browse for the PAW Users group.
- Click New Item and select Security group.
- Select the "..." button and browse for the Cloud Services Admins group.
- Click on the Cloud Services Admins item and click Item Options.
- Select Is not.
- Click OK on the targeting window.
Click OK to complete the ProxyServer group policy setting
Go to User Configuration\Preferences\Windows Settings\Registry. Right-click Registry, select New > Registry Item and configure the following settings:
- Action: Replace
- Hive: HKEY_CURRENT_USER
- Key Path: Software\Microsoft\Windows\CurrentVersion\Internet Settings
Value name: ProxyServer
Note
Do not select the Default box to the left of Value name.
Value type: REG_SZ
Value data: 127.0.0.1:80
- Click the Common tab and select Remove this item when it is no longer applied.
- On the Common tab select Item level targeting and click Targeting.
- Click New Item and select security group.
- Select the "..." button and add the PAW Users group.
- Click New Item and select security group.
- Select the "..." button and browse for the Cloud Services Admins group.
- Click on the Cloud Services Admins item and click Item Options.
- Select Is not.
- Click OK on the targeting window.
Click OK to complete the ProxyServer group policy setting,
- Go to User Configuration\Policies\Administrative Templates\Windows Components\Internet Explorer, and enable the options below. These settings will prevent the administrators from manually overriding the proxy settings.
- Enable the Disable changing Automatic Configuration settings.
- Enable the Prevent changing proxy settings.
Restrict Administrators from logging onto lower tier hosts
In this section, we will configure group policies to prevent privileged administrative accounts from logging onto lower tier hosts.
Create the new Restrict Workstation Logon GPO - this setting will restrict Tier 0 and Tier 1 administrator accounts from logging onto standard workstations. This GPO should be linked to the "Workstations" top-level OU and have the following settings:
In Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Deny log on as a batch job, select Define these policy settings and add the Tier 0 and Tier 1 groups:
Note
Built-in Tier 0 Groups, see Tier 0 equivalency for more details.
Other Delegated Groups
Note
Any custom created groups with effective Tier 0 access, see Tier 0 equivalency for more details.
Tier 1 Admins
Note
This Group was created earlier in Phase 1.
In Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Deny log on as a service, select Define these policy settings and add the Tier 0 and Tier 1 groups:
Note
Note: Built-in Tier 0 Groups, see Tier 0 equivalency for more details.
Other Delegated Groups
Note
Note: Any custom created groups with effective Tier 0 access, see Tier 0 equivalency for more details.
Tier 1 Admins
Note
Note: This Group was created earlier in Phase 1
Create the new Restrict Server Logon GPO - this setting will restrict Tier 0 administrator accounts from logging onto Tier 1 servers. This GPO should be linked to the "Tier 1 Servers" top-level OU and have the following settings:
In Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Deny log on as a batch job, select Define these policy settings and add the Tier 0 groups:
Note
Built-in Tier 0 Groups, see Tier 0 equivalency for more details.
Other Delegated Groups
Note
Any custom created groups with effective Tier 0 access, see Tier 0 equivalency for more details.
In Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Deny log on as a service, select Define these policy settings and add the Tier 0 groups:
Note
Built-in Tier 0 Groups, see Tier 0 equivalency for more details.
Other Delegated Groups
Note
Any custom created groups with effective Tier 0 access, see Tier 0 equivalency for more details.
In Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Deny log on locally, select Define these policy settings and add the Tier 0 groups:
Note
Note: Built-in Tier 0 Groups, see Tier 0 equivalency for more details.
Other Delegated Groups
Note
Note: Any custom created groups with effective Tier 0 access, see Tier 0 equivalency for more details.
Deploy your PAW(s)
Note
Ensure that the PAW is disconnected from the network during the operating system build process.
Install Windows 10 using the clean source installation media that you obtained earlier.
Note
You may use Microsoft Deployment Toolkit (MDT) or another automated image deployment system to automate PAW deployment, but you must ensure the build process is as trustworthy as the PAW. Adversaries specifically seek out corporate images and deployment systems (including ISOs, deployment packages, etc.) as a persistence mechanism so preexisting deployment systems or images should not be used.
If you automate deployment of the PAW, you must:
- Build the system using installation media validated using the guidance in Clean Source for installation media.
- Ensure that the automated deployment system is disconnected from the network during the operating system build process.
Set a unique complex password for the local Administrator account. Do not use a password that has been used for any other account in the environment.
Note
Microsoft recommends using Local Administrator Password Solution (LAPS) to manage the local Administrator password for all workstations, including PAWs. If you use LAPS, ensure that you only grant the PAW Maintenance group the right to read LAPS-managed passwords for the PAWs.
Install Remote Server Administration Tools for Windows 10 using the clean source installation media.
Configure Windows Defender Exploit Guard
Note
Configuration guidance to follow
Connect the PAW to the network. Ensure that the PAW can connect to at least one Domain Controller (DC).
Using an account that is a member of the PAW Maintenance group, run the following PowerShell command from the newly-created PAW to join it to the domain in the appropriate OU:
Replace the references to Fabrikam with your domain name, as appropriate. If your domain name extends to multiple levels (e.g. child.fabrikam.com), add the additional names with the "DC=" identifier in the order in which they appear in the domain's fully-qualified domain name.
Apply all critical and important Windows Updates before installing any other software (including administrative tools, agents, etc.).
Force the Group Policy application.
- Open an elevated command prompt and enter the following command:
- Restart the computer
(Optional) Install additional required tools for Active Directory Admins. Install any other tools or scripts required to perform job duties. Ensure to evaluate the risk of credential exposure on the target computers with any tool before adding it to a PAW. Access this page to obtain more information on evaluating administrative tools and connection methods for credential exposure risk. Ensure to obtain all installation media using the guidance in Clean Source for installation media.
Note
Using a jump server for a central location for these tools can reduce complexity, even if it doesn't serve as a security boundary.
(Optional) Download and install required remote access software. If administrators will be using the PAW remotely for administration, install the remote access software using security guidance from your remote access solution vendor. Ensure to obtain all installation media using the guidance in Clean Source for installation media.
Note
Carefully consider all the risks involved in allowing remote access via a PAW. While a mobile PAW enables many important scenarios, including work from home, remote access software can potentially be vulnerable to attack and used to compromise a PAW.
Validate the integrity of the PAW system by reviewing and confirming that all appropriate settings are in place using the steps below:
- Confirm that only the PAW-specific group policies are applied to the PAW
- Open an elevated command prompt and enter the following command:
- Review the resulting list and ensure that the only group policies that appear are the ones you created above.
- Confirm that no additional user accounts are members of privileged groups on the PAW using the steps below:
Open Edit Local Users and Groups (lusrmgr.msc), select Groups, and confirm that the only members of the local Administrators group are the local Administrator account and the PAW Maintenance global security group.
Note
The PAW Users group should not be a member of the local Administrators group. The only members should be the local Administrator account and the PAW Maintenance global security group (and PAW Users should not be a member of that global group either).
Also using Edit Local Users and Groups, ensure that the following groups have no members: Backup Operators Cryptographic Operators Hyper-V Administrators Network Configuration Operators Power Users Remote Desktop Users Replicators
- Confirm that only the PAW-specific group policies are applied to the PAW
(Optional) If your organization uses a security information and event management (SIEM) solution, ensure that the PAW is configured to forward events to the system using Windows Event Forwarding (WEF) or is otherwise registered with the solution so that the SIEM is actively receiving events and information from the PAW. The details of this operation will vary based on your SIEM solution.
Note
If your SIEM requires an agent which runs as system or a local administrative account on the PAWs, ensure that the SIEMs are managed with the same level of trust as your domain controllers and identity systems.
(Optional) If you chose to deploy LAPS to manage the password for the local Administrator account on your PAW, verify that the password is registered successfully.
- Using an account with permissions to read LAPS-managed passwords, open Active Directory Users and Computers (dsa.msc). Ensure that Advanced Features is enabled, and then right-click the appropriate computer object. Select the Attribute Editor tab and confirm that the value for msSVSadmPwd is populated with a valid password.
Phase 2: Extend PAW to all administrators
Scope: All users with administrative rights over mission-critical applications and dependencies. This should include at least administrators of application servers, operational health and security monitoring solutions, virtualization solutions, storage systems, and network devices.
Note
The instructions in this phase assume that Phase 1 has been completed in its entirety. Do not begin Phase 2 until you have completed all the steps in Phase 1.
Once you confirm that all steps were done, perform the steps below to complete Phase 2:
(Recommended) Enable RestrictedAdmin mode
Enable this feature on your existing servers and workstations, then enforce the use of this feature. This feature will require the target servers to be running Windows Server 2008 R2 or later and target workstations to be running Windows 7 or later.
Enable RestrictedAdmin mode on your servers and workstations by following the instructions available in this page.
Note
Before enabling this feature for internet facing servers, you should consider the risk of adversaries being able to authenticate to these servers with a previously-stolen password hash.
Create "RestrictedAdmin Required - Computer" group policy object (GPO). This section creates a GPO which enforces the use of the /RestrictedAdmin switch for outgoing Remote Desktop connections, protecting accounts from credential theft on the target systems
- Go to Computer Configuration\Policies\Administrative Templates\System\Credentials Delegation\Restrict delegation of credentials to remote servers and set to Enabled.
Link the RestrictedAdmin Required - Computer to the appropriate Tier 1 and/or Tier 2 Devices by using the Policy options below:
- PAW Configuration - Computer
- -> Link Location: Admin\Tier 0\Devices (Existing)
- PAW Configuration - User
- -> Link Location: Admin\Tier 0\Accounts
- RestrictedAdmin Required - Computer
- ->Admin\Tier1\Devices or -> Admin\Tier2\Devices (Both are optional)
Note
This is not necessary for Tier 0 systems as these systems are already in full control of all assets in the environment.
- PAW Configuration - Computer
Move Tier 1 Objects to the appropriate OUs
Move Tier 1 groups To the Admin\Tier 1\Groups OU. Locate all groups that grant the following administrative rights and move them to this OU.
- Local administrator on more than one server
- Administrative Access to cloud services
- Administrative Access to enterprise applications
- Local administrator on more than one server
Move Tier 1 accounts to the Admin\Tier 1\Accounts OU. Move each account that is a member of those Tier 1 groups (including nested membership) to this OU.
Add the appropriate members to the relevant groups
Tier 1 Admins - This group will contain the Tier 1 Admins that will be restricted from logging onto Tier 2 hosts. Add all your Tier 1 administrative groups that have administrative privileges over servers or internet services.
Note
If administrative personnel have duties to manage assets at multiple tiers, you will need to create a separate admin account per tier.
Enable Credential Guard to reduce risk of credential theft and reuse. Credential Guard is a new feature of Windows 10 that restricts application access to credentials, preventing credential theft attacks (including Pass-the-Hash). Credential Guard is completely transparent to the end user and requires minimal setup time and effort. For further information on Credential Guard, including deployment steps and hardware requirements, please refer to the article, Protect domain credentials with Credential Guard.
Note
Device Guard must be enabled in order to configure and use Credential Guard. However, you are not required to configure any other Device Guard protections in order to use Credential Guard.
(Optional) Enable Connectivity to Cloud Services. This step allows management of cloud services like Azure and Office 365 with appropriate security assurances. This step is also required for Microsoft Intune to manage the PAWs.
Note
Skip this step if no cloud connectivity is required for administration of cloud services or management by Intune.
- These steps will restrict communication over the internet to only authorized cloud services (but not the open internet) and add protections to the browsers and other applications that will process content from the internet. These PAWs for administration should never be used for standard user tasks like internet communications and productivity.
- To enable connectivity to PAW services follow the steps below:
Configure PAW to allow only authorized Internet destinations. As you extend your PAW deployment to enable cloud administration, you need to allow access to authorized services while filtering out access from the open internet where attacks can more easily be mounted against your admins.
Create Cloud Services Admins group and add all the accounts to it that require access to cloud services on the internet.
Download the PAW proxy.pac file from TechNet Gallery and publish it on an internal website.
Note
You will need to update the proxy.pac file after downloading to ensure that it is up-to-date and complete. Microsoft publishes all current Office 365 and Azure URLs in the Office Support Center. These instructions assume that you will be using Internet Explorer (or Microsoft Edge) for administration of Office 365, Azure, and other cloud services. Microsoft recommends configuring similar restrictions for any 3rd party browsers that you require for administration. Web browsers on PAWs should only be used for administration of cloud services, and never for general web browsing.
You may need to add other valid Internet destinations to add to this list for other IaaS provider, but do not add productivity, entertainment, news, or search sites to this list.
You may also need to adjust the PAC file to accommodate a valid proxy address to use for these addresses.
You can also restrict access from the PAW using a web proxy as well for defense in depth. We don't recommend using this by itself without the PAC file as it will only restrict access for PAWs while connected to the corporate network.
Once you have configured the proxy.pac file, update the PAW Configuration - User GPO.
- Go to User Configuration\Preferences\Windows Settings\Registry. Right-click Registry, select New > Registry Item and configure the following settings:
Action: Replace
Hive: HKEY_ CURRENT_USER
Key Path: Software\Microsoft\Windows\CurrentVersion\Internet Settings
Value name: AutoConfigUrl
Note
Do not select the Default box to the left of Value name.
Value type: REG_SZ
Value data: enter the complete URL to the proxy.pac file, including http:// and the file name - for example http://proxy.fabrikam.com/proxy.pac. The URL can also be a single-label URL - for example, http://proxy/proxy.pac
Note
The PAC file can also be hosted on a file share, with the syntax of file://server.fabrikan.com/share/proxy.pac but this requires allowing the file:// protocol. See the "NOTE: File://-based Proxy Scripts Deprecated" section of this Understanding Web Proxy Configuration blog for additional detail on configuring the required registry value.
Click the Common tab and select Remove this item when it is no longer applied.
On the Common tab select Item level targeting and click Targeting.
Click New Item and select security group.
Select the "..." button and browse for the Cloud Services Admins group.
Click New Item and select security group.
Select the "..." button and browse for the PAW Users group.
Click on the PAW Users item and click Item Options.
Select Is not.
Click OK on the targeting window.
Click OK to complete the AutoConfigUrl group policy setting.
- Go to User Configuration\Preferences\Windows Settings\Registry. Right-click Registry, select New > Registry Item and configure the following settings:
Apply Windows 10 Security baselines and Cloud Service Access Link the security baselines for Windows and for cloud service access (if required) to the correct OUs using the steps below:
Extract the contents of the Windows 10 Security Baselines ZIP file.
Create these GPOs, import the policy settings, and link per this table. Link each policy to each location and ensure the order follows the table (lower entries in table should be applied later and higher priority):
Policies:
Policy Name Link CM Windows 10 - Domain Security N/A - Do Not Link Now SCM Windows 10 TH2 - Computer Admin\Tier 0\Devices Admin\Tier 1\Devices Admin\Tier 2\Devices SCM Windows 10 TH2- BitLocker Admin\Tier 0\Devices Admin\Tier 1\Devices Admin\Tier 2\Devices SCM Windows 10 - Credential Guard Admin\Tier 0\Devices Admin\Tier 1\Devices Admin\Tier 2\Devices SCM Internet Explorer - Computer Admin\Tier 0\Devices Admin\Tier 1\Devices Admin\Tier 2\Devices PAW Configuration - Computer Admin\Tier 0\Devices (Existing) Admin\Tier 1\Devices (New Link) Admin\Tier 2\Devices (New Link) RestrictedAdmin Required - Computer Admin\Tier 0\Devices Admin\Tier 1\Devices Admin\Tier 2\Devices SCM Windows 10 - User Admin\Tier 0\Devices Admin\Tier 1\Devices Admin\Tier 2\Devices SCM Internet Explorer - User Admin\Tier 0\Devices Admin\Tier 1\Devices Admin\Tier 2\Devices PAW Configuration - User Admin\Tier 0\Devices (Existing) Admin\Tier 1\Devices (New Link) Admin\Tier 2\Devices (New Link) Note
The "SCM Windows 10 - Domain Security" GPO may be linked to the domain independently of PAW, but will affect the entire domain.
What’s New in the 4th Pass Source Guard Enterprise Edition v4.0 serial key or number?
Screen Shot

System Requirements for 4th Pass Source Guard Enterprise Edition v4.0 serial key or number
- First, download the 4th Pass Source Guard Enterprise Edition v4.0 serial key or number
-
You can download its setup from given links:


